Anonymous - tryhackme
Created on Wed. 20 may 2020
It's been a longtime I haven't done this. So this room is a cool little challenge I completed today and I wanted to do a write-up about it.
Reconnaissance
As per usual I started by scanning the IP address with nmap.
#[p4p1@writeups untracked/]$ nmap -F x.x.x.x
Starting Nmap 7.60 ( https://nmap.org ) at 2020-05-19 23:46 CEST
Nmap scan report for x.x.x.x
Host is up (0.023s latency).
Not shown: 96 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
139/tcp open netbios-ssn
445/tcp open microsoft-ds
Nmap done: 1 IP address (1 host up) scanned in 0.16 seconds
This time around I decided to do a really quick nmap to start going somewhere because I really didn't want to wait for a full nmap. A few day's ago I met up with a friend and we where talking about FTP and that he had to login to a box with the "Anonymous" username on FTP. So logically seeing ftp open I had to try it out :), now looking back at this the room of the name is also anonymous so it's kind of obvious what the creator is hinting at.
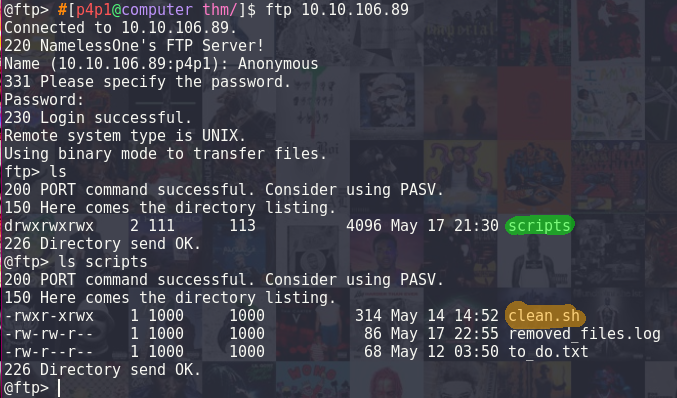
In the image we can see my login is Anonymous with no password. After logging in I started digging around, I found a folder named scripts/ highlighted in green. That is obviously interesting to us. Inside of scripts their is also a really nice file called clean.sh, highlighted in orange. I decided to copy that file to my machine so that I could look at it.
Exploitation
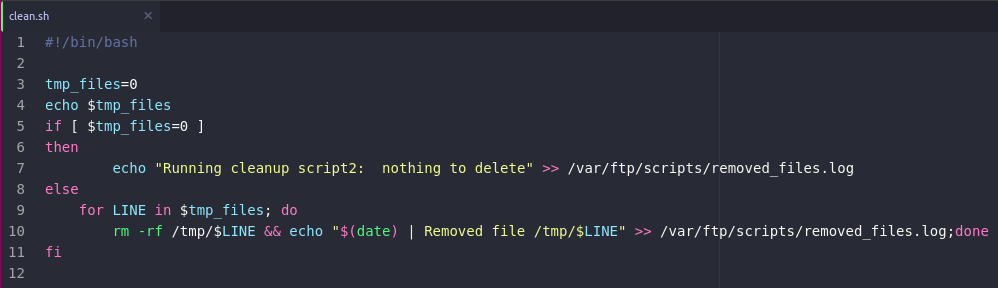
Looking at the script it's clear that it's a simple log cleaning script, by this the script is probably automatically ran by the server so I embedded a reverse shell inside of the script and uploaded it to the server and amazing I got a reverse shell.
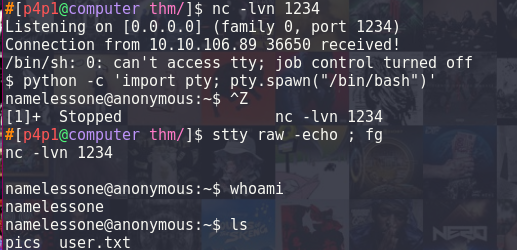
From there I then cleaned my shell with stty and started working on rooting the box!
Privilege Escalation
As usual I got stuck on privilege escalation for a while. After running linpeas.sh and LinEnum.sh going through kernel exploits, sudo etc... I found something peculiar the current user is part of a group called lxd.
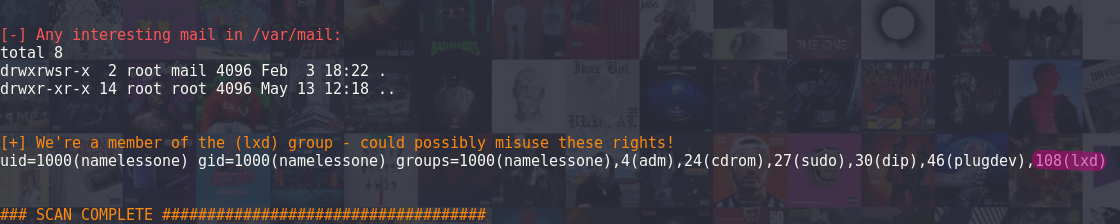
Seeing this I researched online lxd and found a website explaining that lxd is a linux container service a bit like docker. A few weeks bag I saw a few exploits using docker and I decided to exploit lxd! After some quick research I found a basic exploit on exploit-db named lxd privilege escalation. Looking in the exploit it's pretty straightforward lxd mounts the entire disc on a mount point and give us a root shell to maintain the container.
Thank you for reading, check out my other write-ups here or some of my personal project I am currently working on here.
Categories
My tryhackme account
thm-badge-workflow

A github workflow to add your tryhackme stats to your github profile.
store | How it was build | repoLinks
Questions / Feedback
Donate

If you like the content of my website you can help me out by donating through my github sponsors page.