Red Team Village CTF - Defcon Safe Mode
Created on Fri. 09 Aug 2020

This is my team's attempt at completing the Red Team Villages CTF at the defcon safe mode. HERE IS THE WRITEUP OF MY TEAM MATE
Discord / Survey
Have you been checking your discord? (not a bot challenge)
One does not simply fill out a 60 minute survey
There where two flags, pretty easy nothing much one was just sent on the red Team Village CTF's discord and an other one was given to us after completing a survey about the CTF!.
Trainer
The password to the level
The trainer category was confusing to me in the beginning because the challenges where out of order. But after finding the link to the first challenge it was extremely straight forward.
Level0
To start the challenge you have to use ssh to login into the challenge server:
#[p4p1@p4p1_XPS15 p4p1/]$ ssh level0@trainer.threatsims.com
After logging in if you do an "ls" there is an obvious hint inside of the welcome_message telling you what to do :) in this challenge I only had to do a cat and I would get the flag:
level0@trainer:~$ cat level1_password
Level1
For the level1 you need to know the basic structure of a linux folder directory and cat the file inside
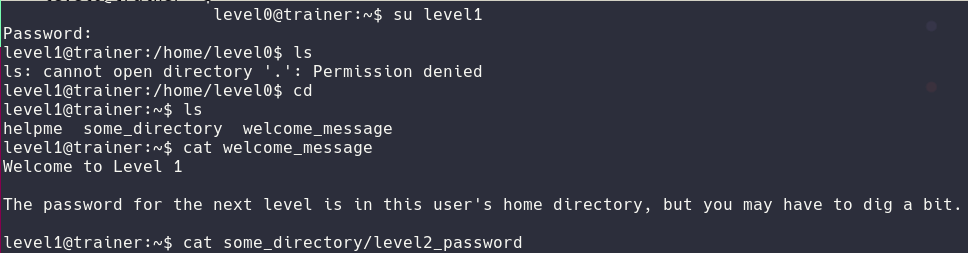
Level2
For the level2 same deal just more folders.
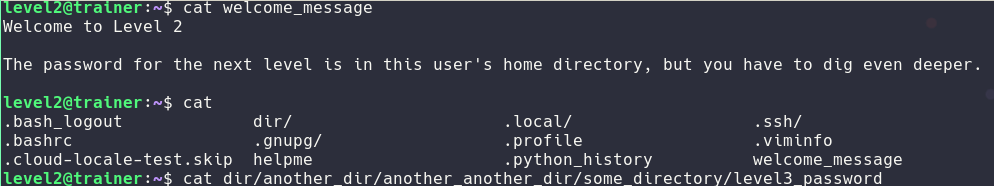
Level3
On the level3 it's basically like before the only difference is that you have to cat a hidden file
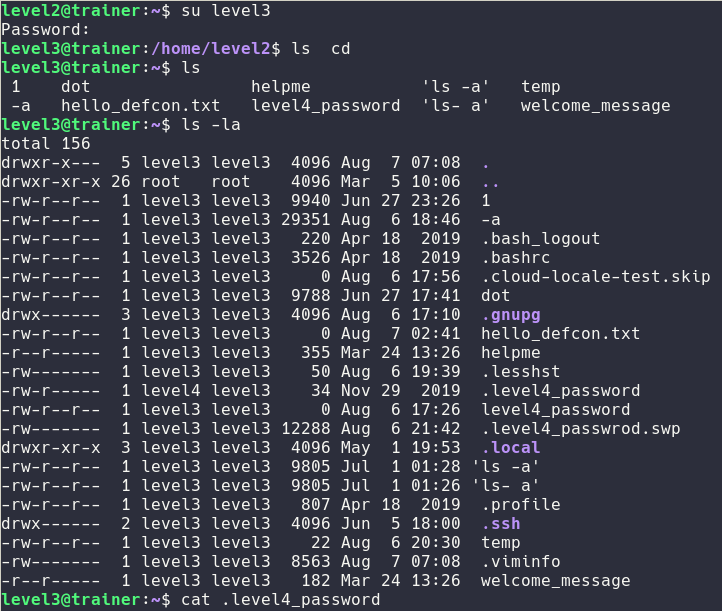
Level4
For the level4 it's as usual but we are working with a hidden directory
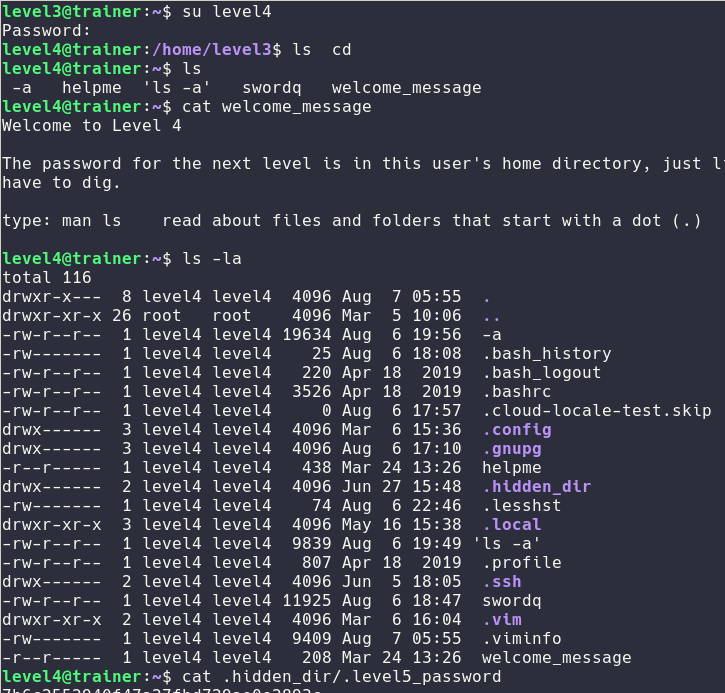
Level5
For this level I started using things a little more advanced like find. Wow :)
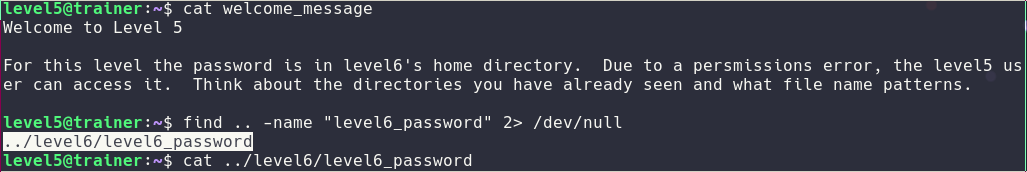
Level6
Same as before some more finding fu.
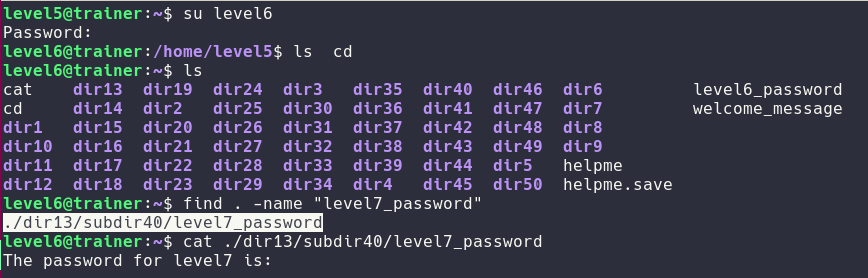
Level7
For the level 7 I had to use grep and some of my bash scripting skills
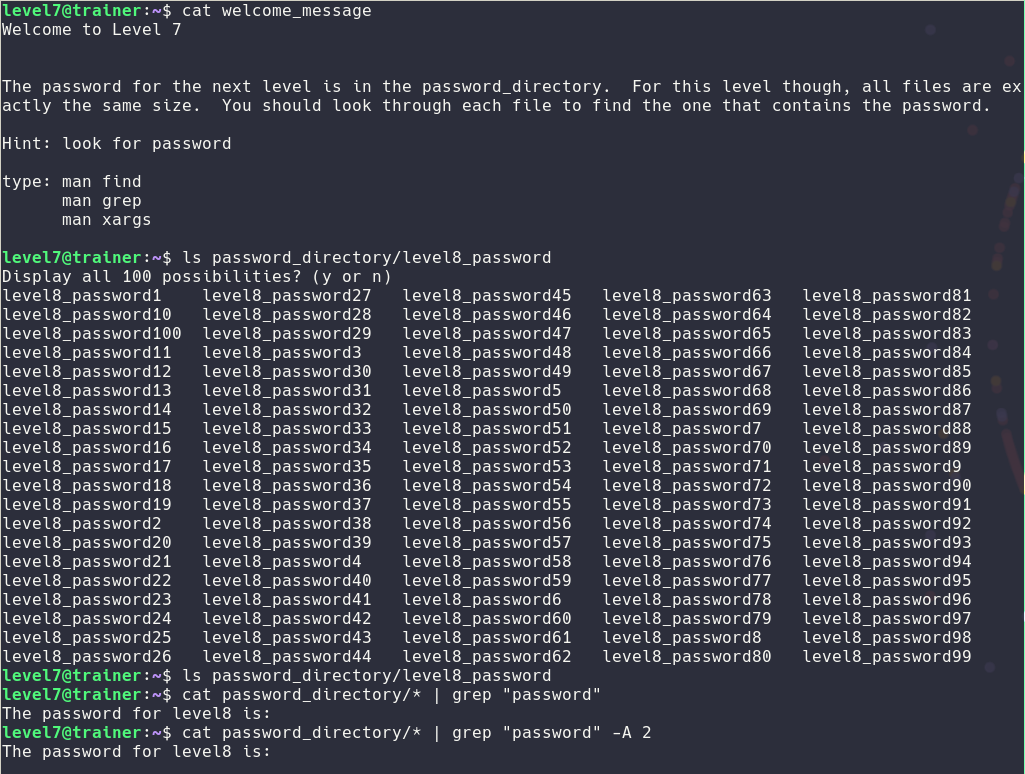
Level8
For the level8 the output was broken so I would rater retype the commands than give a crappy screenshot. But for this challenge I had to use a find command to retrieve an executable file.
level8@trainer:~$ cat welcome_message
Welcome to Level 8
For this level the password is in an executable hidden in one of these sub-directories. When you run
the executable it will print out the flag. To run the executable type: ./executable
type: man find
After finding and executing the binary, you should try to run the command strings on the it and review the output. type: strings
level8@trainer:~$ find -type f -executable
./dir24/subdir13/level9_password
level8@trainer:~$ ./dir24/subdir13/level9_password
Level9
For the 9th challenge had to use some grep fu!
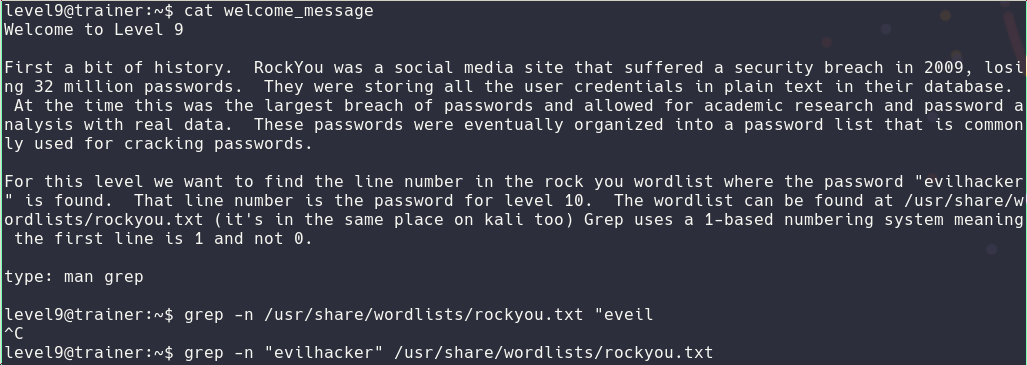
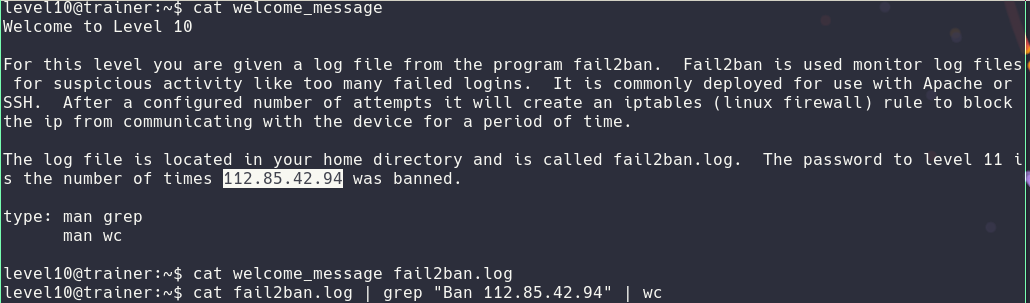
Level10
For this one I had to do some more grep, but I did spend some time analyzing the log files.
Level11
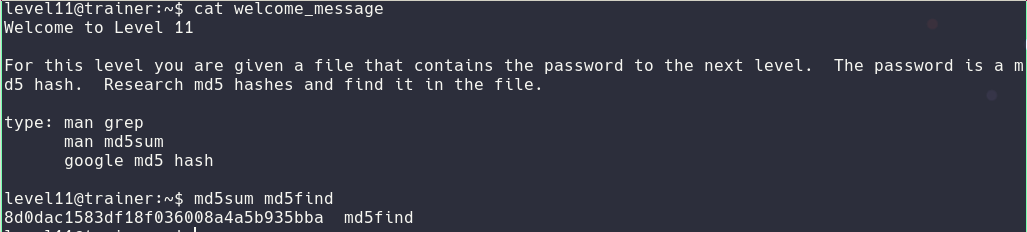
For the level11 I had to learn the command md5sum but it was nothing to hard I spent 5 min figuring out If I had to extract the sum from the file or just check the actual files sum in the end it was very straight forward. I just had to find a correct hash with a simple regex and run md5find on it.
Level12
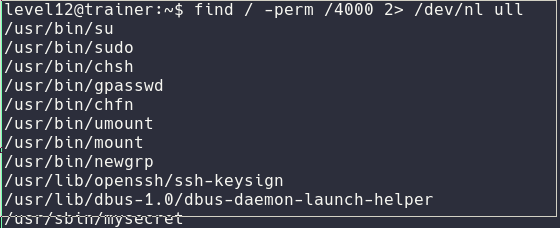
For this level I just had to use find to find a SUID or GUID bit program.
Level13
For this level I just had to do and 'env' command and the flag was inside of a AWS_TOKEN variable
level13@trainer:~$ cat welcome_message
Welcome to Level 13
For this level you are going to familiarize yourself with environment variables. They are used for a
wide variety of applications. Specifically, they can be used for docker and cloud providers to store
credentials. They password to level 14 is is the one that ends with ID.
type: man environ
google environment variables
level13@trainer:~$ env
SHELL=/bin/bash
HISTTIMEFORMAT=%Y-%m-%d %T
AWS_DEFAULT_REGION=us-west-2
PWD=/home/level13
LOGNAME=level13
XDG_SESSION_TYPE=tty
HOME=/home/level13
LANG=en_US.UTF-8
AWS_SECRET_ACCESS_KEY=2fE3dasswJalrXs2UtnFEMIs/gK7MDENG/bPxRfiCY
XDG_SESSION_CLASS=user
TERM=st-256color
USER=level13
SHLVL=14
AWS_ACCESS_KEY_ID={IT WAS HERE}
XDG_SESSION_ID=3380
XDG_RUNTIME_DIR=/run/user/1001
SSH_CLIENT=82.67.110.73 37200 22
PATH=/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
MAIL=/var/mail/level13
SSH_TTY=/dev/pts/218
OLDPWD=/home/level12
_=/usr/bin/env
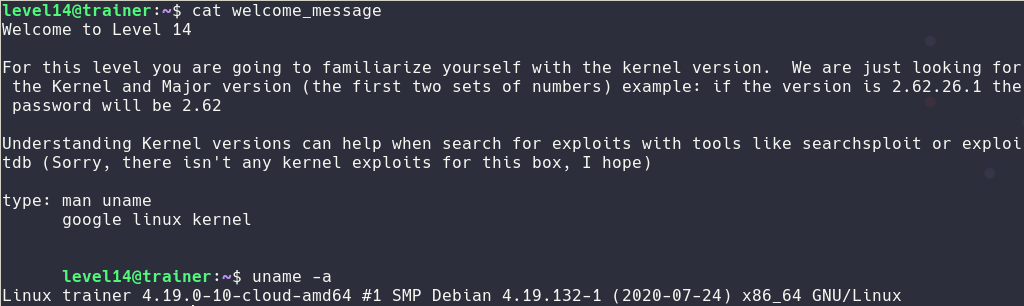
Level14
An other very straight forward challenge. I needed to find the kernel version.
Level15
Same as 14 but I had to find the distribution of linux
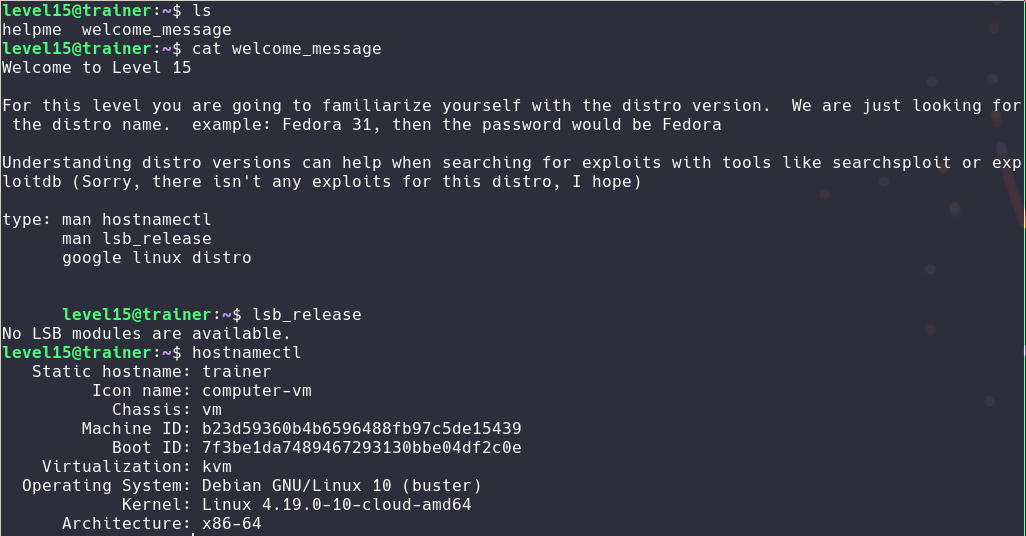
Level16
In this level I had to look at bash aliases. So I decided to cat the .bashrc to find them:
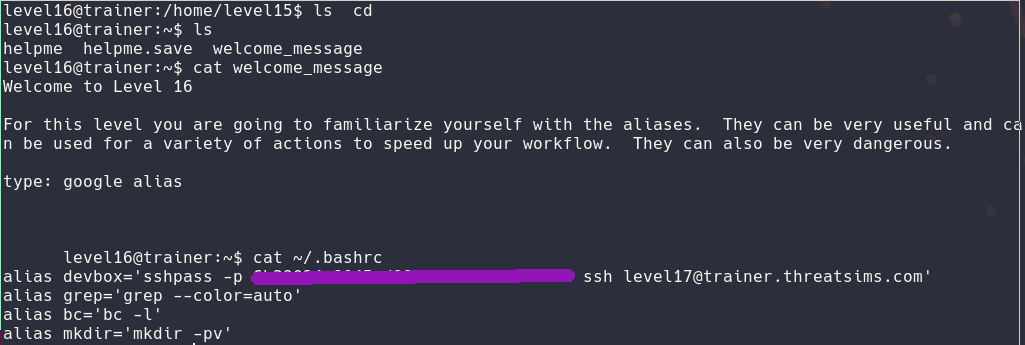
Level17
For this challenge I had to use vim (lol, I'm using vim to write this). I just had to check the .viminfo file and the flag was there:
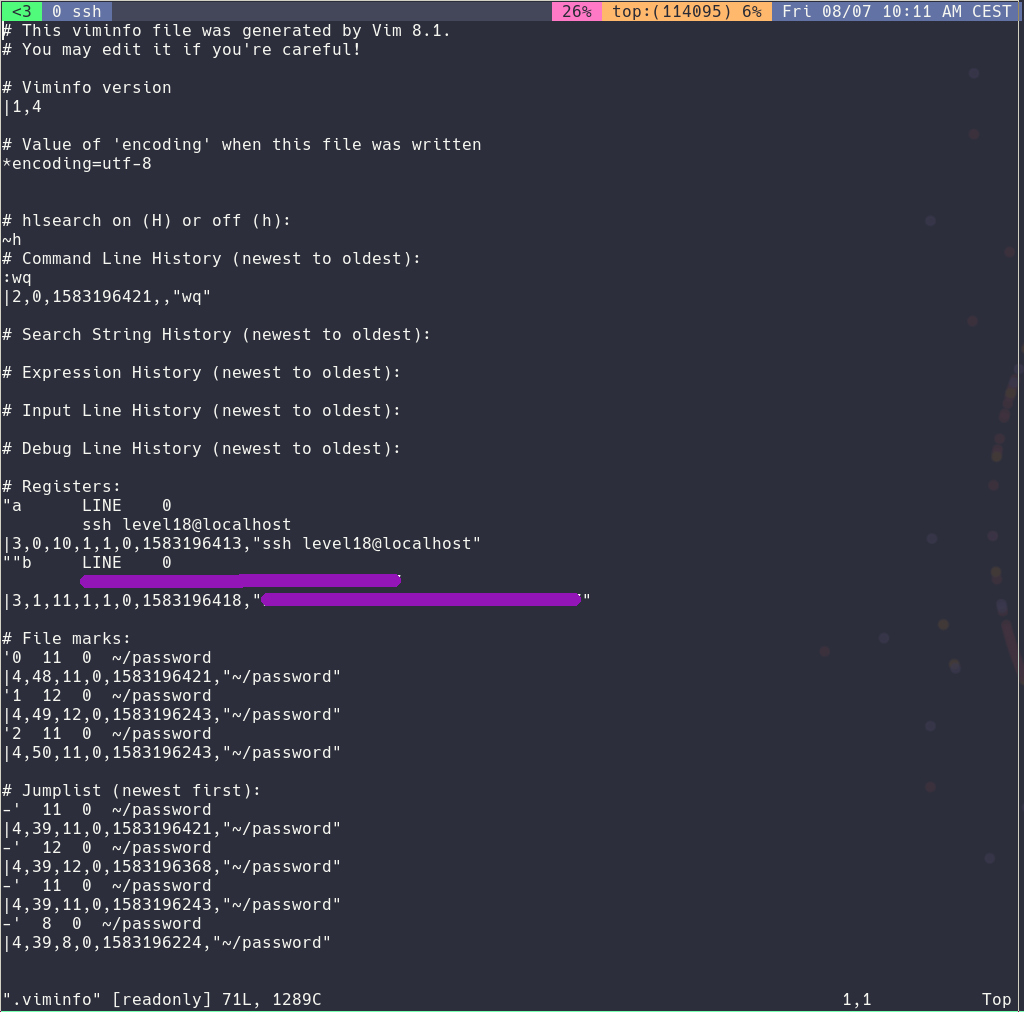
Level18
For this challenge I just had to cat the .bash_history file because this user is an idiot :P
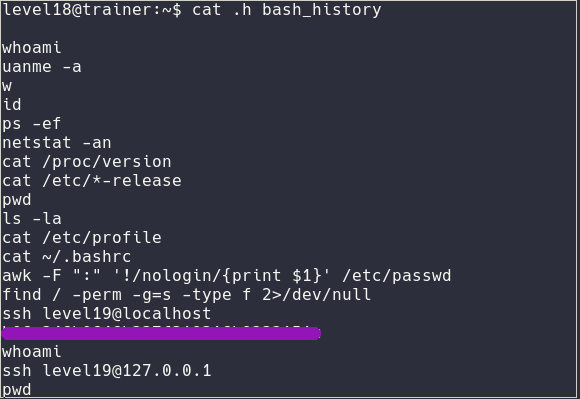
Level19
For this chal I had to use ssh on the server it gives us a private key. Then on my machine I used it to login:
#[p4p1@p4p1_XPS15 defcon_safemode/]$ ssh -i id_rsa level20@167.71.187.239
Level20
In this challenge the password is located in a compressed file, so I just had to use tar:
level20@trainer:~$ tar -xf backup.tgz
Level21
Exactly as before but the compressed file did not have an extention
level20@trainer:~$ tar -xf backup
OSINT
flag-543as
Peter Gibbons has been looking for a job. Flag format is not ts{} or TS{}
This was the first flag I tried doing for some reason I was really hyped by the OSINT Challenges. Reading the instructions it said that: "Peter Gibson" was looking for a new job. So my first instinct was linked in I put in Peter Gibson but the first link wasn't successful there are real people named Peter Gibson so I then googled the name really quick. I found that Peter Gisbson is a character from Office Space(some TV show) and he works at "Initech"
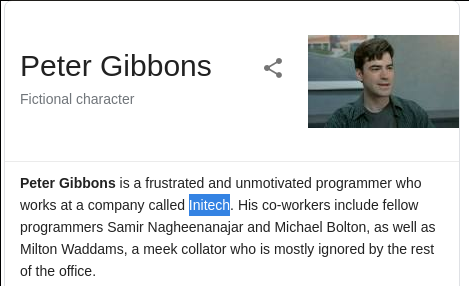
With this new information I then returned to linkedIn and researched a bit more:
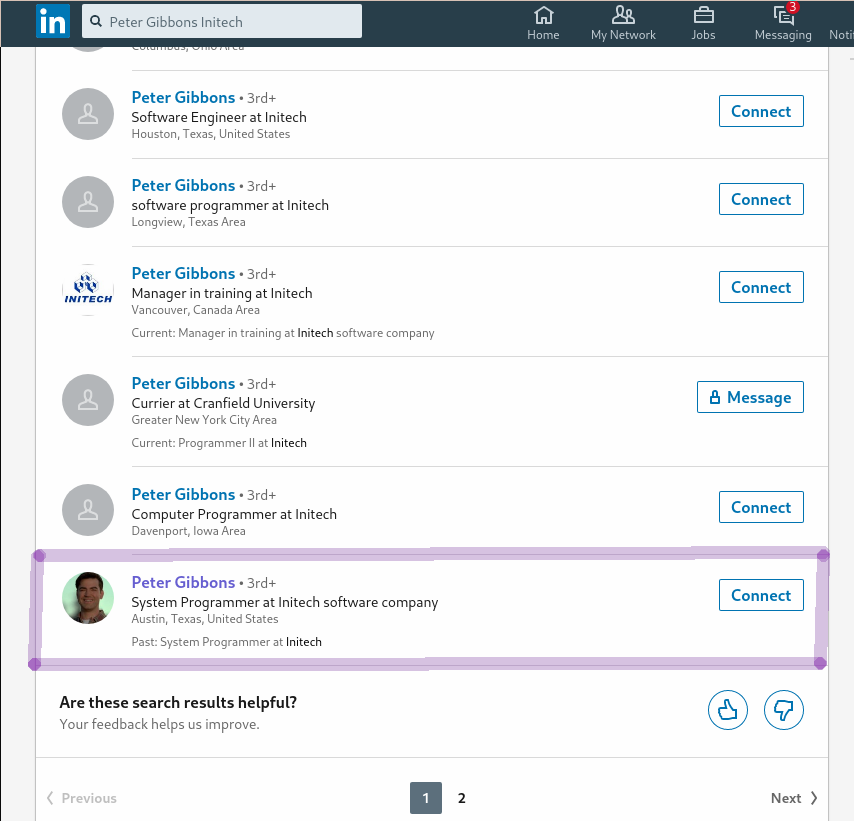
Looking at this persons bio I found the flag!
flag-443kj.txt
Peter Gibbons has a specific set of skills.
The hint for this flag is Peter Gibson has a specific set of skills, looking back at the last exercises I guessed that on his linked skills there would be some skills mentioned. But there wasn't I then looked at his posts and he posted his resume looking for jobs so I dug in there to find his "skill":

flag-32798nm
Michael Bolton is trying to get in with penetrode now? Flag format is not TS{} or ts{}.
For this flag I had to find someone else he was called Micheal Bolton, the one and only :P I started by digging around in the people at initech (the company of Peter Gibson) to see if they where connected somehow.
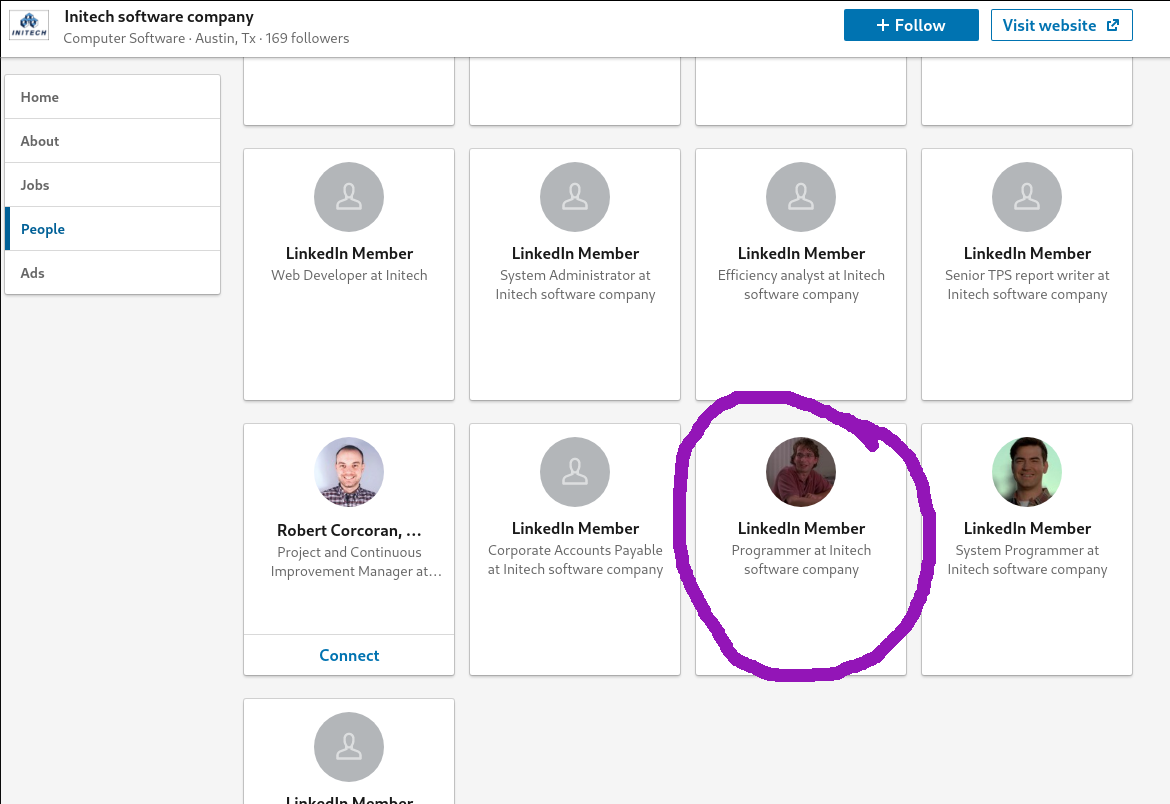
This person doesn't have a name yet but I was guessing it was Micheal. So I searched the name on LinkedIn to see what I could find:
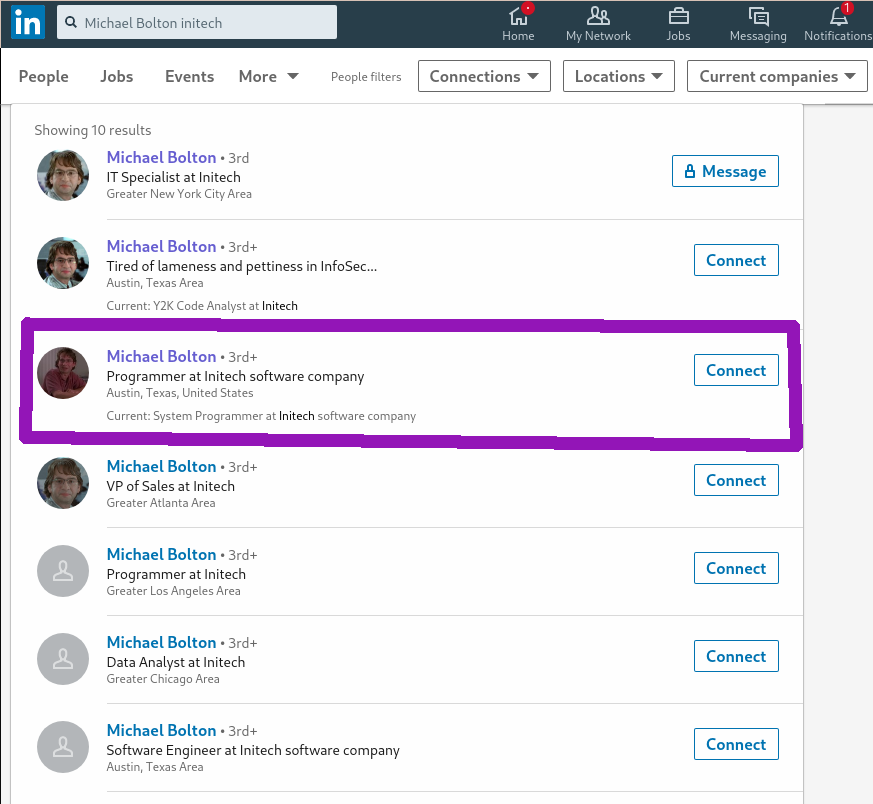
After finding him I looked at his resume and I saw a post with written penetrope, it was a hint from the challenge. In the resume I found the flag:

tweets
The sponsors have surronded the flag
Easy flag found on twitter, I just had to decode the base64.

tweets2
I got a sweet battlestation
This one was kind of a pain because my internet is really slow so loading the images was a pain in the ass but in the end I found it after looking at a thousands of desks :D
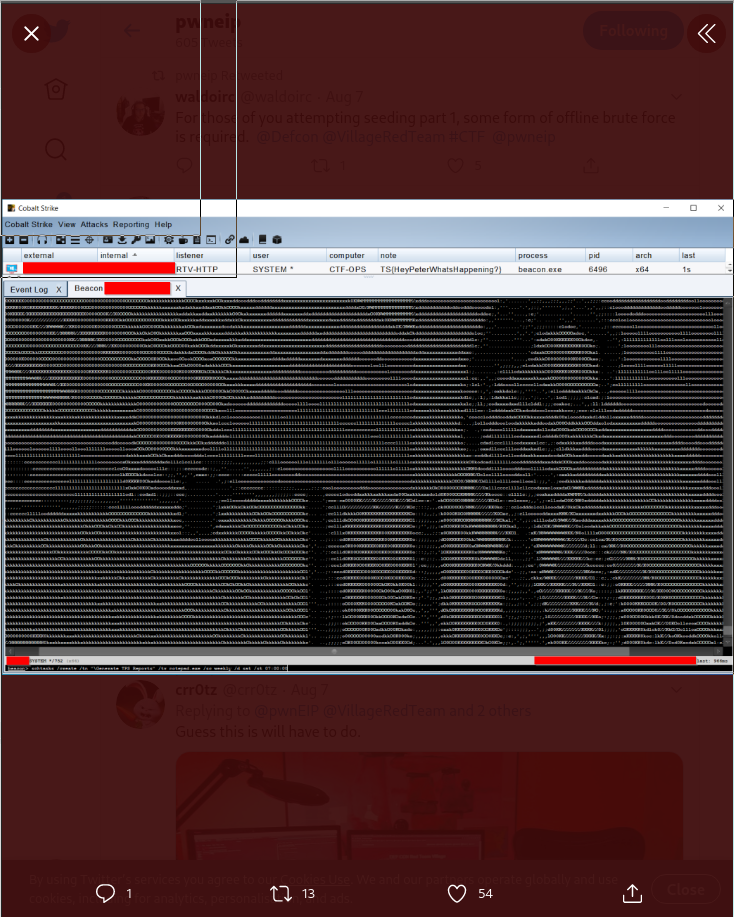
Bill Lumbergh
Get a taste of whats to come in the Finals with an immersive enterprise environment to hack your way through!
This flag was also an easy one I just went on twitter looked for an ascii art image and got the flag:
Tiger Tunes
Lookin' for dem Tiger Tunes
You might be looking around blind, but I'm sure you'll find the flag.
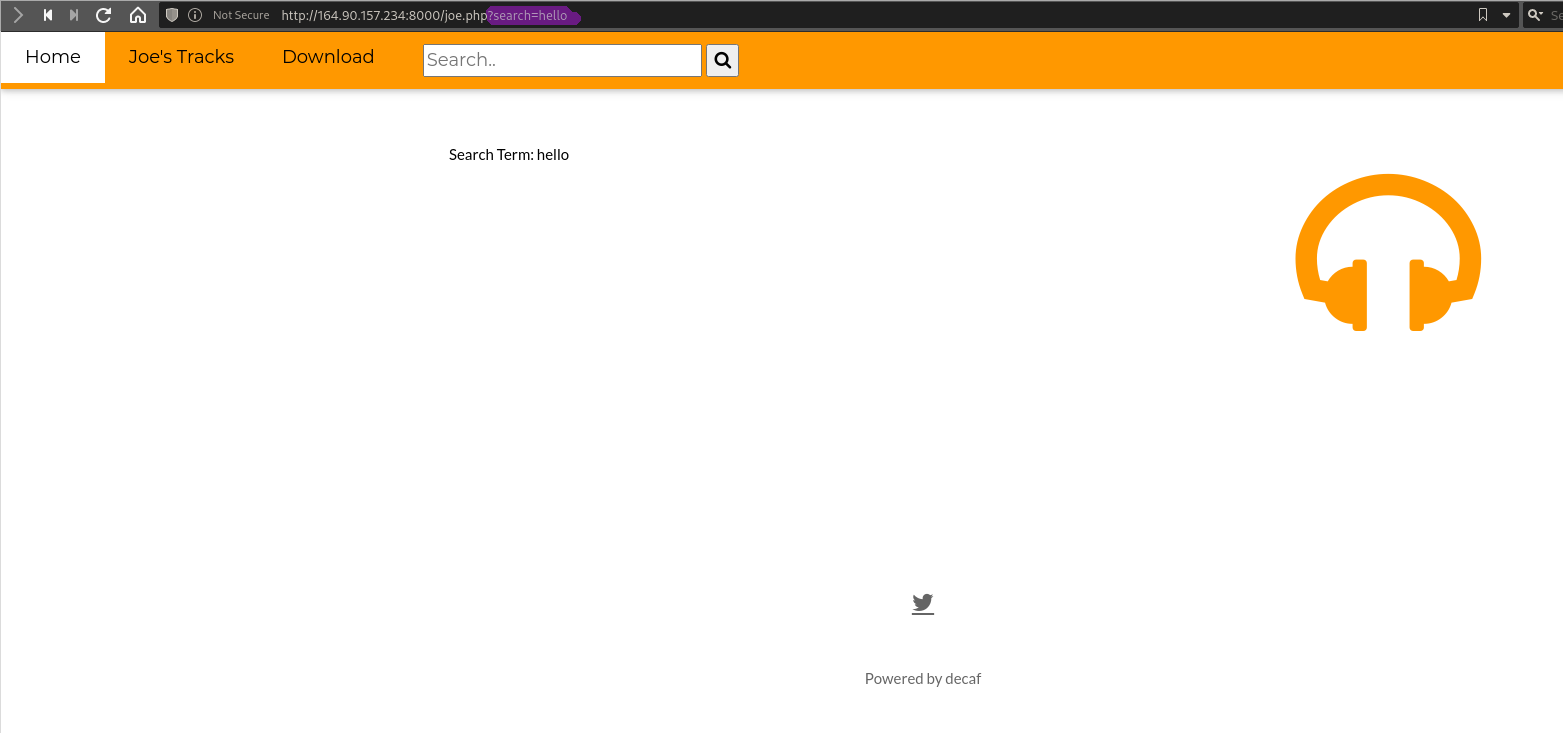
Going into this challenge I didn't know that to expect so I first started looking around the pages of the website. I then decided to look at the robots.txt file:
User-agent: *
Disallow: /
Disallow: /etc/flag.txt
Disallow: /images/
Disallow: /images/CarolsHusbandsBody.jpg
Disallow: /notes/
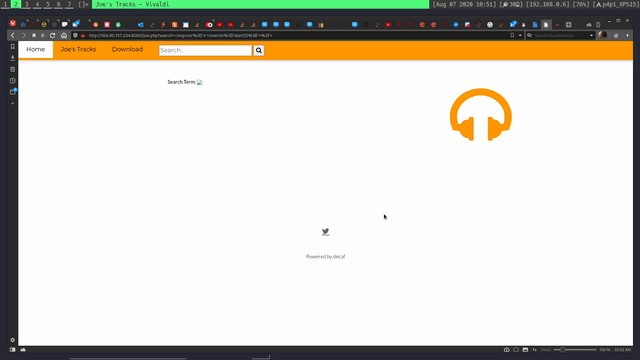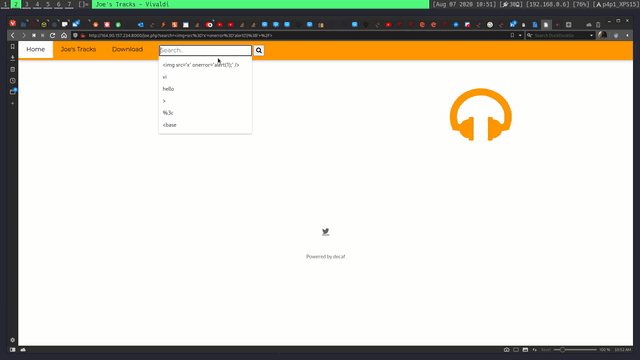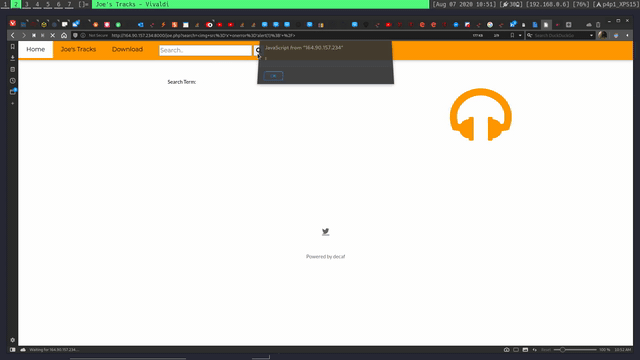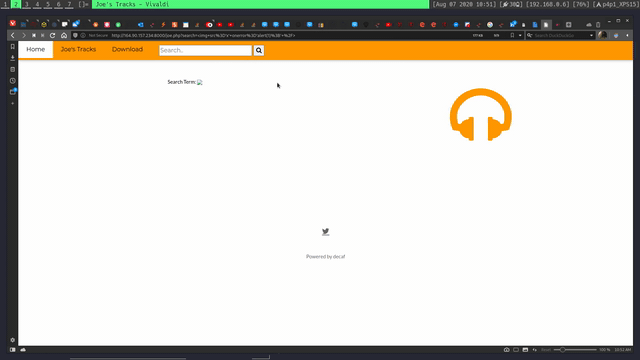
Seeing the third line I tried injecting that into my search bar but the link was not active after a bit of digging around on the page I could not find the location of the flag. Then after a bit it clicked what if it was a path in the server and not just the website. So I decided to look for a Local File Inclusion vulnerability. So I looked at linkes and pages. After some time I found one in the search page(highlighted in purple):
I then changed the parameter for this and got a hit:
http://164.90.157.234:8000/joe.php?search=../../../etc/flag.txt
Doing this challenge I also found that the search page is vulnerable for reflected XSS:
Crypto Cypher and Encodings
All about that base
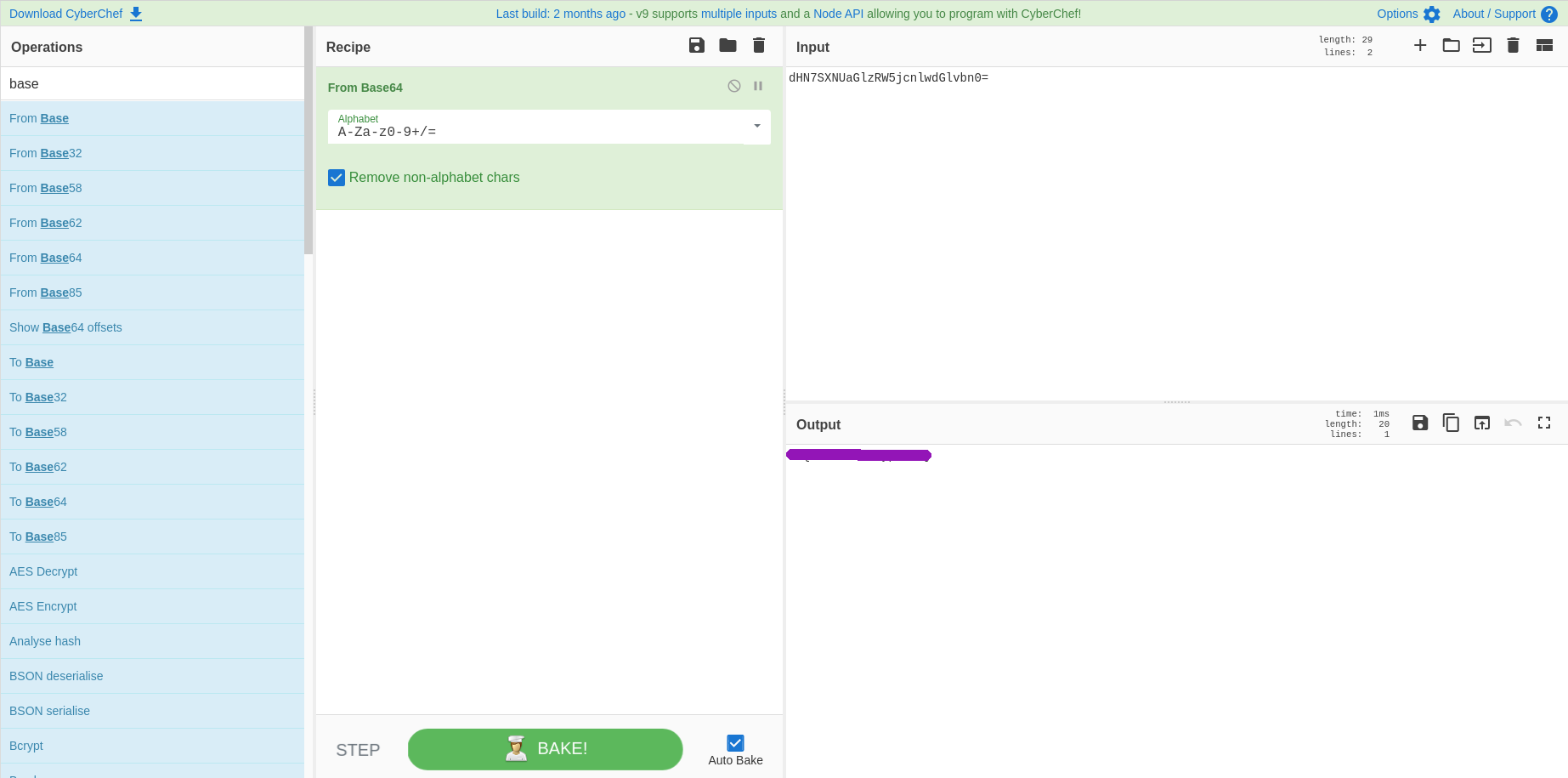
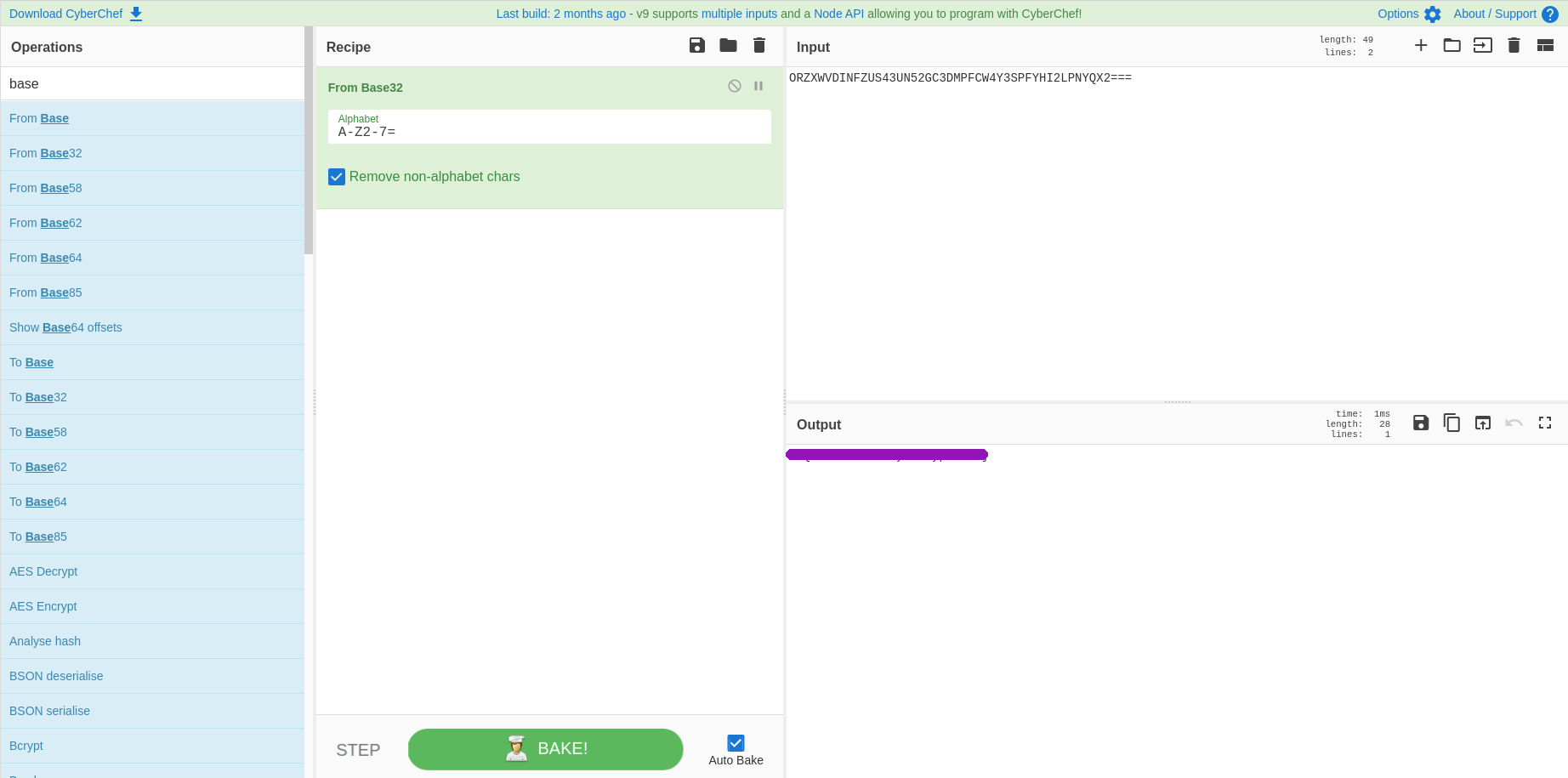
For this challenge It was very straight forward the hash looked like base64 so I ran it through cyberchef:
All about that base remix
For this challenge I knew my friend did the base 64 one and it was pretty easy for him so I went on cyberchef and tried to crack it using multiple layers of base64. It didn't really work so I went back to the drawing board. I remembered a challenge I did on TryHackMe where I used the different bases 64-32-16 so I figured I should check there:
Logs
2 - Who failed
How many different IP addresses were banned?
For this challenge we want to find out how many different people got Banned inside of a provided log file:
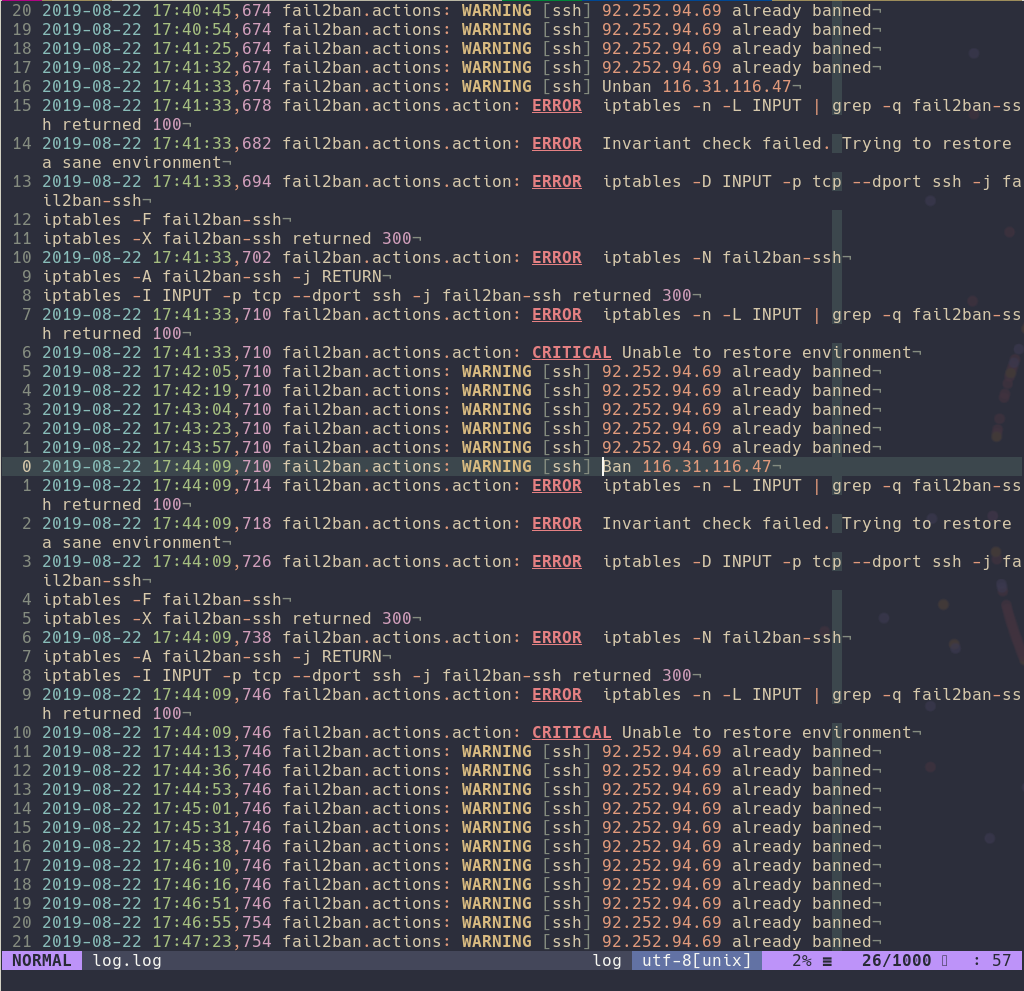
I first started using grep and regex to find all of the lines with ip addresses. I then used sort to remove duplicate lines to get rid of dup ip's I then used grep to find the Ban ones and with wc get the number:
#[p4p1@p4p1_XPS15 defcon_safemode/]$ grep -E "([0-9]{1,3}[\.]){3}[0-9]{1,3}" log.log | sort -u -t' ' -k6,7 | grep "Ban" | wc
CovidScammers
For this challenge they gave us a binary to crack called client. Like an idiot I ran the binary so I spent my days looking at this as well:
Free Flag (and binary)
You've been contacted by a high-end but morally ambiguous finance company (unhackable-bitcoin-wallet.com) to investigate a data breach. The box in question is a mail server in their internal network, a sample of the malware found on the system has been pulled and given to you. Your task, should you choose to accept it, is to reverse-engineer the sample and locate, fuzz and exploit the C2 server, and then hack-back to learn about the malicious actor and recover the stolen documents.
For this flag i started by running radare2 on the binary (a little kill I Know). I then saw a huge mess of code so I quited radare I tried running it nothing showed up I then did a strings greping for a flag and found one :)
#[p4p1@p4p1_XPS15 defcon_safemode/]$ strings client | grep TS{
Syscall
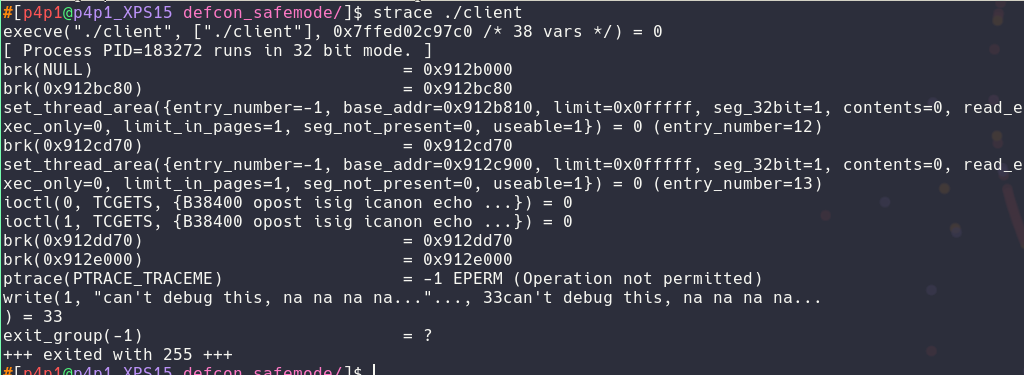
What syscall is hindering your dynamic analysis? Flag is just the syscall, no brackets or anything.
In this challenge I just ran strace and found the ptrace syscall that blocked me from debugging the binary.
Who Me?
What is this malware sample called (not the actual binary name)? Flag is the name as a string, no brackets or anything.
In this challenge I had to find the name of the binary pretty easy just and other string :)

Scouting
What is the C2 server? Provide the domain as the answer, no brackets or anything..
In this challenge I had to find a domain name server in wich the binary connect to. I first started looking through the domain names that where appearent inside of strings but i didn't find the solution there after a bit I found a base64 encoded string and decided to run it through cyberchef and voilas!
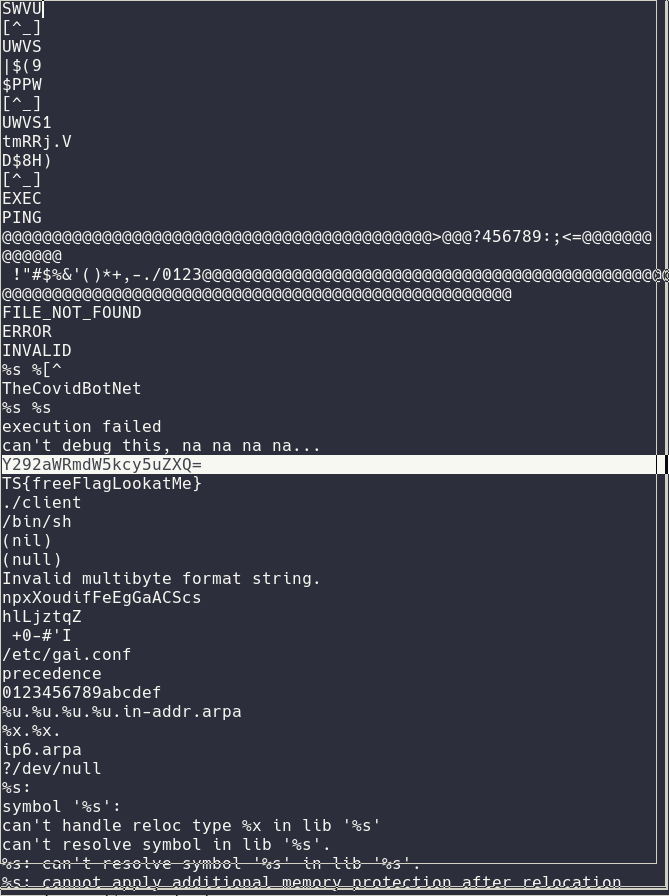
Interlude
To make things easier for my team I decided to patch the binary really quick using radare2 so that we can run strace on it as much as we want. I simply changed the je inside of the condition to a jne so that we can only run the binary with strace :)
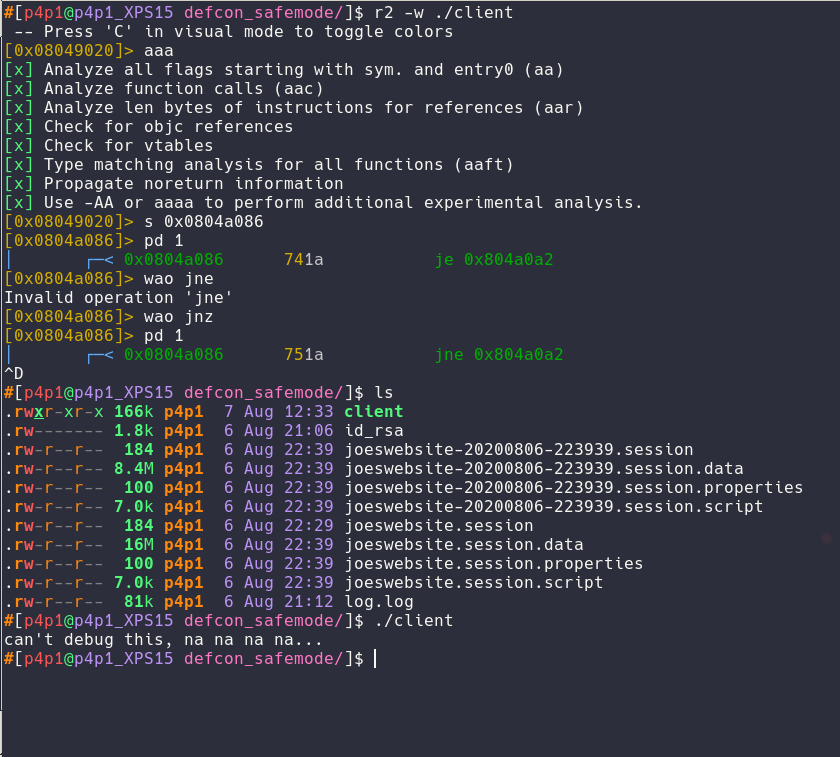
I also did a lot of decompiling using Ghidra and taking a lot of notes on how the program actually works to aid my future research here are the cool things I found:
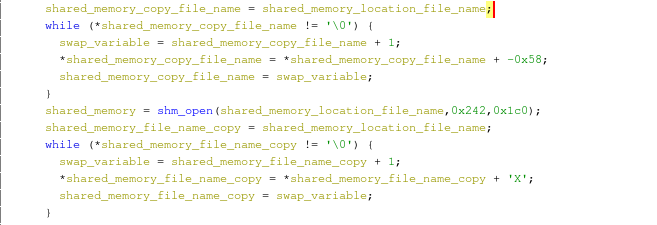
The covid scammer software uses some kind of shared memory seen in the screenshot above and has a sort of crypto on the file names so they cant be extracted with strings. It uses that technique thought the program so that you can't extract all of the files.
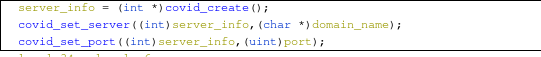
This part was also really cool it's like some kind of data structure generated by the malware so that it can find the server and port to connect to. The port is set as a hard coded variable 8888.
This is nice, might stay a while...
How does the malware persist? SHA1 hash the path of the persistence location.
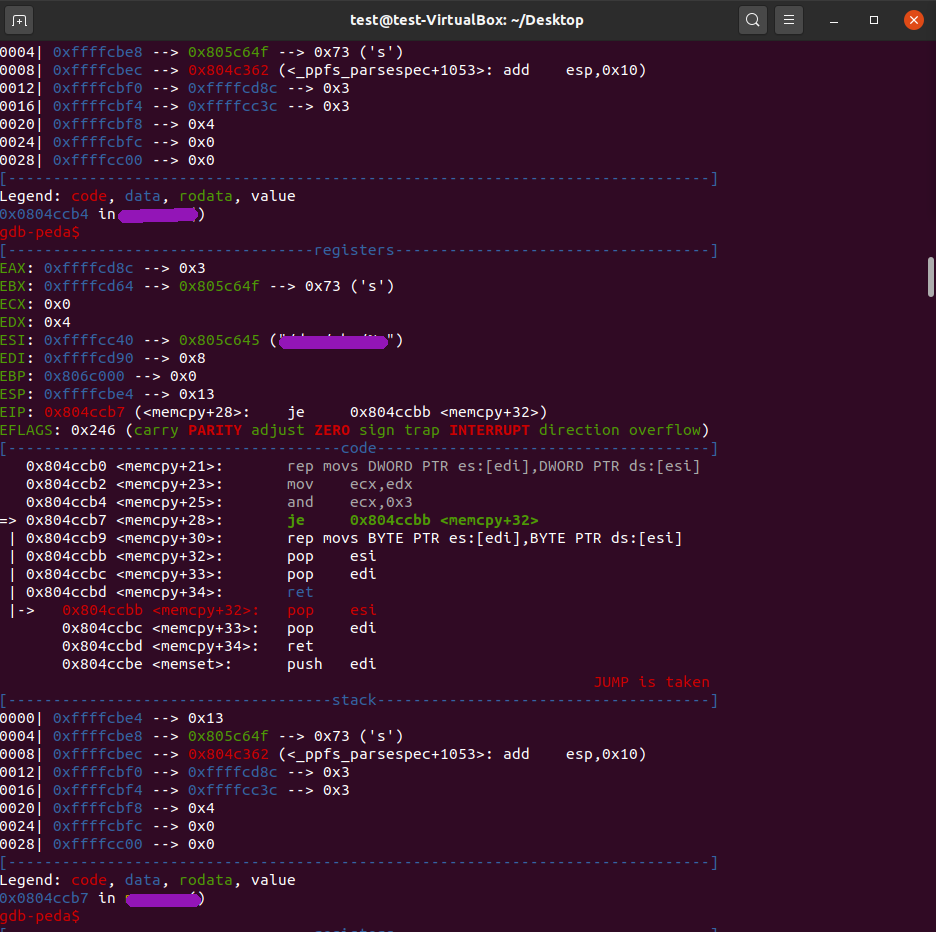
For this part I used a virtual machine, seeing that all of the strings variables are "crypted" I decided to use the patch binary and ran it through gdb-peda. Because inside of Ghidra I saw that it was calling fopen a lot I guessed that it was for persistence:
Because of that I decided to put a breakpoint on fopen in gdb and I just stepped through the program until it hit!
License and Registration Please
The malware creates a UUID and stores it in a file, what is the name of this file. Provide the SHA1 hash of the full path as the flag.
For this exercise I basically did the same thing as before and I was able to get the folder path!
Shared Secrets
The malware creates a shared-memory object and stores a flag inside. Recover the flag. Flag has the TS{} format, you'll know when you get it.
Personally I have never used shared memory objects in C so I had no idea how this worked so I spent some time on Ghidra figuring it out, I looked around and saw this code:
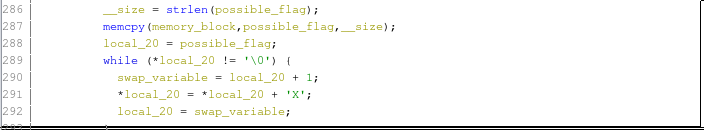
Seeing this I guessed that the flagged would be copied inside of the memory I did some digging around on the net to see if I could inspect shared memory with radare2 but I've never done that so I just figured I could figure it out by using gdb on memcpy and on shm_open. With gdb I found that the location of the shared memory was in:
/dev/shm/egartos_divoc
I then went back to gdb set a breakpoint to memcpy and saw a pretty weird string so I then tried to open the file with vim and saw the same string. I kind of freaked out because I didn't know the encryption so I ran it through a hash detection software It didn't give me any information. I even tried cesar cypher on it :D. In the end it was very straight forward I ran it on CyberChef using the Magic mode and figured out it was Base 32:
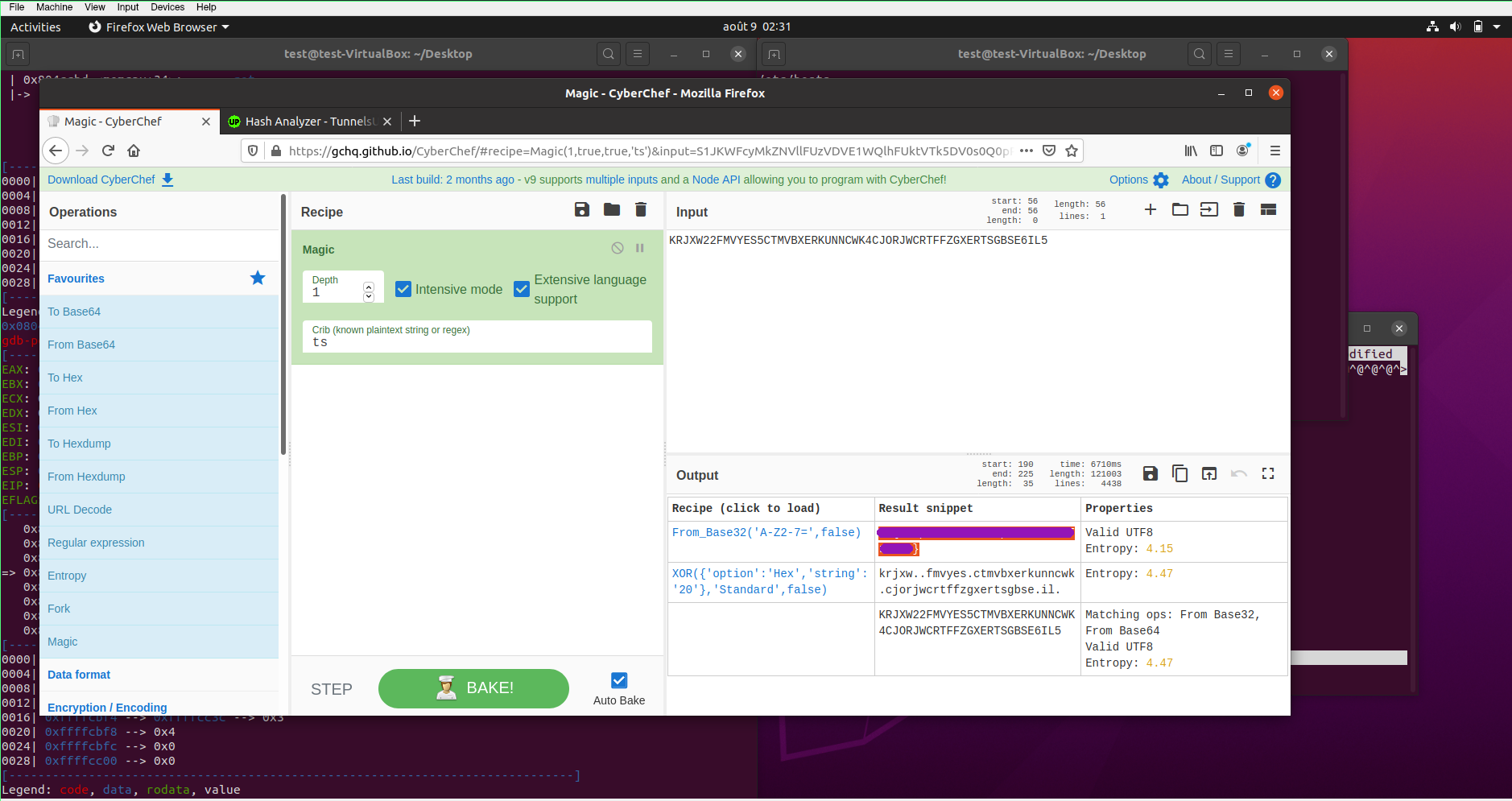
RE
Debug Me
Or just dissasemble me.
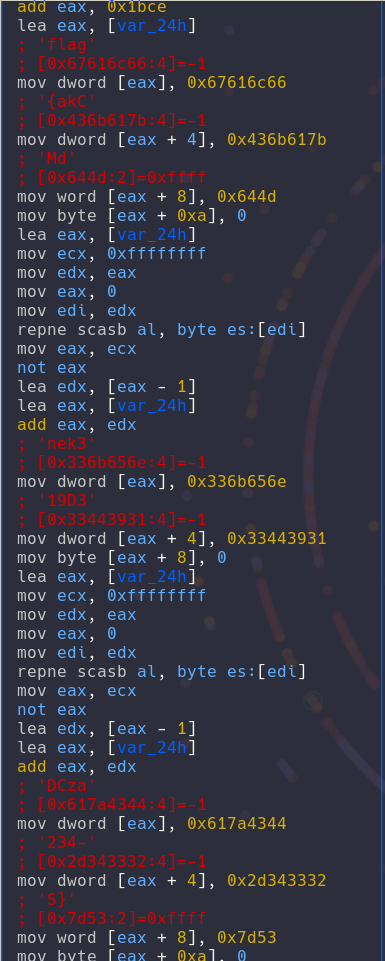
This one was so easy, I just opened the file in radare went to the function named vuln and recreated the flag.
PWN
Clicker
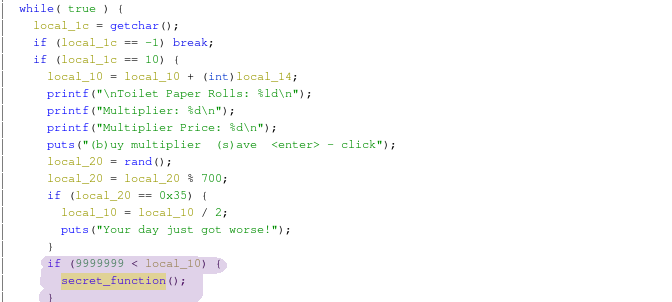
All you have to do is score 10,000,000 to get the flag. Get Clicking!!!!!
For this challenge I really just did exactly what I know how to do best and it's cheating the system, I opened the binary in ghidra. Looked at the general structure of the code, found the function that displayed the flag:
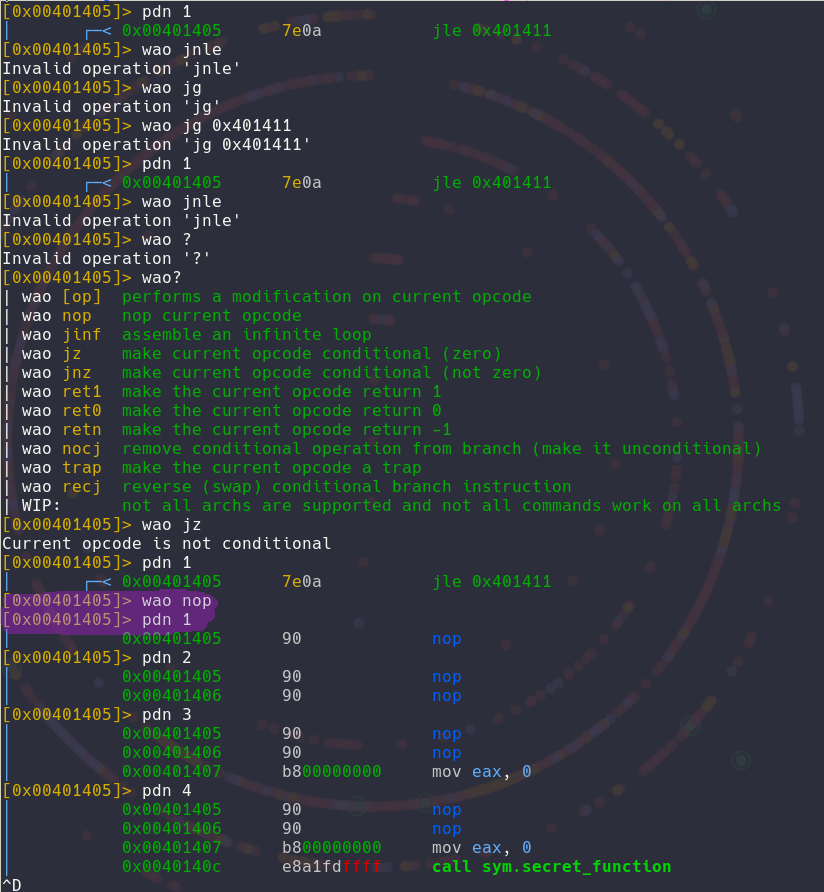
I then used radare to change the op code with some NOP, so that it would do any checks and just run the function on every round :) if you look closely I just add one NOP but radare adds 5, that's because NOP is 1 byte long but the previous instruction JLE is 5 bytes long so we have to replace everything so that the binary doesn't crash:
ltrace-easy
Can you run the binary? You may have to trace it or something.
For this flag I was very perplexed I could open it with ghidra and running strace and ltrace (I don't have much experience with those tools) confused me a lot. So I decided to just look at the assembly to see what information I could extract. Looking at the visual representation of the code it was obviously doing 3 checks, the first one was the username of the person running the program:
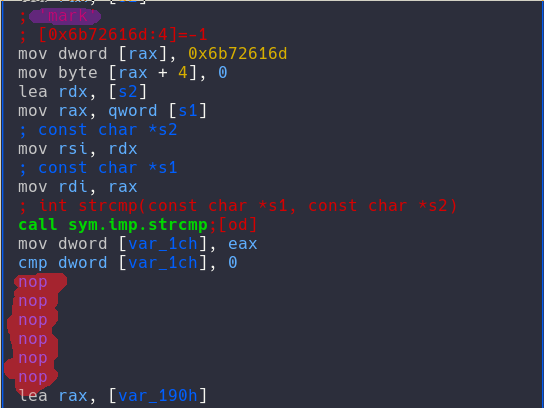
Then it was the current working directory of the program:
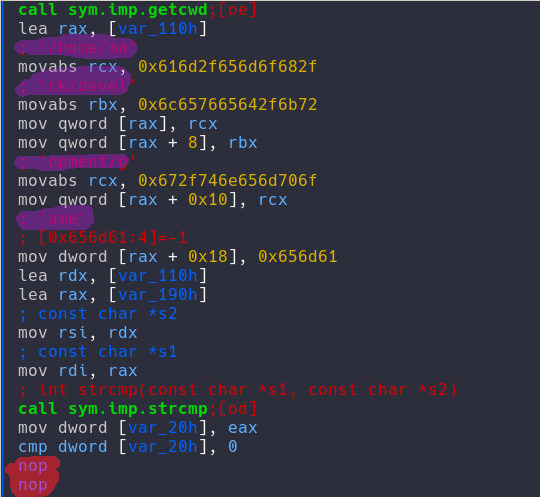
And at last it was the presence of a file in /tmp/:
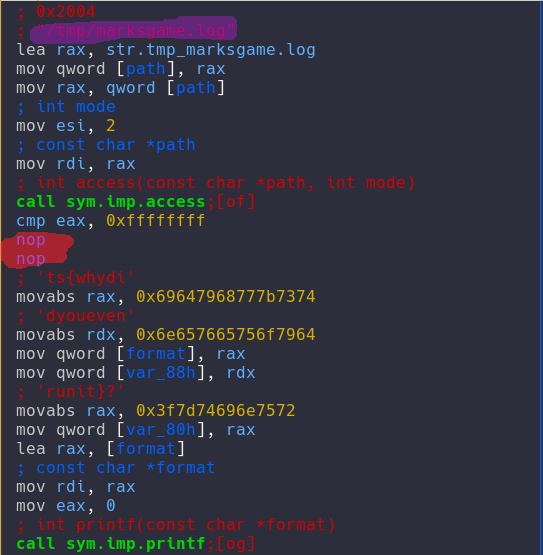
As you can see in the screen shot I was having none of that so with radare I just change the conditions with NOP op codes(in red) and I retrieved the flag that way!
Forensics
Tom Nook - 1A - Internet Traffic
There's been suspicion that Tom Nook has been exfiltrating data out of the network. Could you help me find out what he's doing? Attached is a PCAP.
This challenge was pretty easy I just opened the pcap file inside of wireshark looked around for a bit and found the flag inside of a tcp request :)
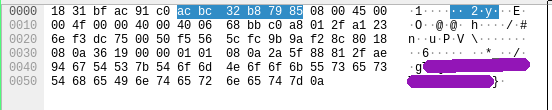
Tom Nook - 1B - Internet Traffic
The government is asking for Tom Nook Host, Ip.
An other really easy flag his host ip was inside of the request :)

Tom Nook - 1C - Internet Traffic
What's the ip from the server he is interacting with?
Same as above.

Tom Nook - 1D - Internet Traffic
You found files in the pcap, nice what is the filename?
I just had to run through the file a bit more and found the file name in an other request.
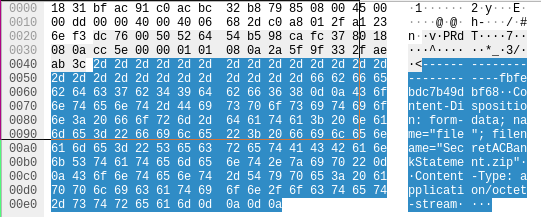
Thank you for reading, this capture the flag was awesome I really enjoyed reversing the Covid Scammer malware. In conclusion we arrived at the 156th place for my first "live" ctf where me and my team where competing against real people. It was a lot of fun this report does not have all of the challenges we did I mostly showcased mine, but I will link to Ismail's write-up on the side widget!
Categories
Questions / Feedback
Donate

If you like the content of my website you can help me out by donating through my github sponsors page.