Wifi Pineapple Karma Attack
Created on Sun 23 Oct 2022

Lately I've been working on getting my wifi pineapple ready for engagements and I was casually cruising modules which got me thinking what if I had a captive portal setup to dump credentials to different services through phishing.
After a bit of research on the subject I discovered the KARMA attack! Which can be used to trick a victim into connecting to your own network with the use of a captive portal on that network it will make the reception of the credentials trivial! The only problem is that we need to clone the SSID so it's either the wifi is already public or you know what SSID the victim previously connected to which was open.
The attack
This attack is actually very simple to do and follows three easy steps. The first is to identify our target. After that we want to de authenticate them from the network they are on while our spoofed Access Point is running then the device automatically connects to the spoofed Access Point where a user will be prompted into typing it's credentials in! Here provided is a little slide show showing with examples how this is all organised:
Now explained like this doesn't really show the attackers point of view let's get to that!
In practice
I will be using my wifi pineapple to do the attack. It does trivialise a lot of the work :) After the pineapple is booted up you will need the Evil Portal module. I will also be using kleo's evilportals repo which comes with a sweet selection of portals built in.

After installing the module and selecting the portal wanted I also recommend quickly editing the redirection page. By default the redirection page is setup to show a message like: You are not authorized. I think this ruins the stealthy aspect of the attack so to do that navigate to /www/captiveportal/ and edit the index.php file. I chose to redirect to google.com but it can even be a custom message.
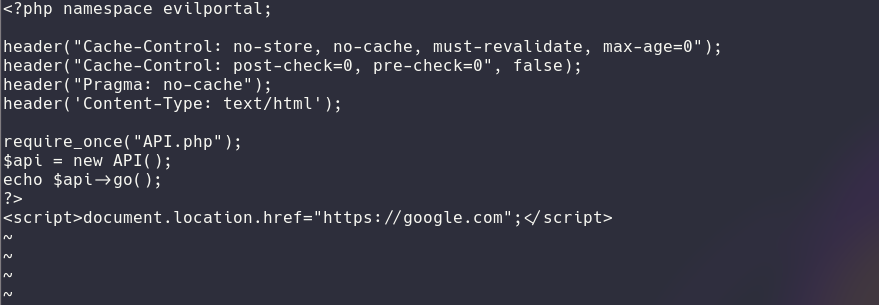
It could be more elegant with Header redirection instead of Javascript but I was just lazy at that point :) After setting this up you will then need to locate your target in the recon section.

After finding the client just saved the Mac address in your notes just to keep track of what you are doing. I sometimes get confused and deauth the wrong one. After taking note of our client we can then setup PineAP to allow associations and spoof FreeWifi connections.
We can then add to the PineAP pool all of the Wifi's we want to impersonate. In my case I have a wifi which was already open that I connected to on my phone called defgh which I will impersonate. The last step is to death the client to get it to automatically connect.

In the case you do not know what ssid the target has previously connected to you can just use a common open ssid wordlist which should help in tricking a victim to connect.
Hopefully you enjoyed this new post. I have an other post about wifi pineapples which is equally as interesting as this one I have been playing a bunch with the wifi pineapple lately and I might be doing a few harware stuff in the future. I never blogged about it but hardware is actually where I did a lot of my hacking in the beginning I used to love soldering stuff together before. I'm currently looking at the flipper zero and the pine phone to start working on some open source stuff as well.
Categories
Book a phishing campaign

You can book a phishing campaign from me on your organisation by contacting me.
LinkedIn or twitter / X. I also use twitter as a platform to update on new posts!Questions / Feedback
Donate

If you like the content of my website you can help me out by donating through my github sponsors page.