GLInet CTF
Created on Tue. 30 Jan 2024

Last year I spent a lot of time going to different security event's all over Europe a sort of Europe tour kind off thing where my objective was to grow my network. I realised that a lot of the bsides around europe where missing events from CTF's and challenges that where made by the people going. The organizers always did a great job but sometimes it felt like it was missing a bit of personality.
I then got an amazing idea what if I built a CTF that I could just bring anywhere at every bsides I went to and I could give out a little present for the people that completed it as like a side challenge to the main CTFs that most bsides have. I then looked through amazon and found the GL-Inet 300M Mini Router for an affordable price.
Building the CTF
With the router arriving last September I rattled my brain at what I thought would be a good challenge I though a mini CTF where you brute force a real wifi network then crack the shitty password then from there find a website where you have a command injection on a non protected admin interface.
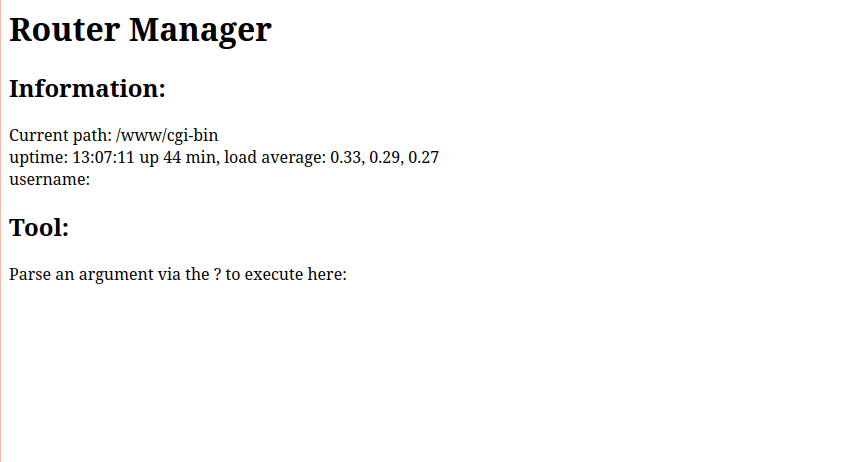
To get this idea working I first started looking at the default web server of the router. I don't really want people messing with the actual website but what if I could configure a hidden page inside of the structure. Inside of openwrt that page is located in /www from there you can see the default structure of the webserver:
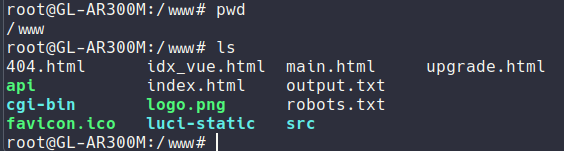
There was also the config of the http server that I found which one was running with netstat:
# netstat -tnlp
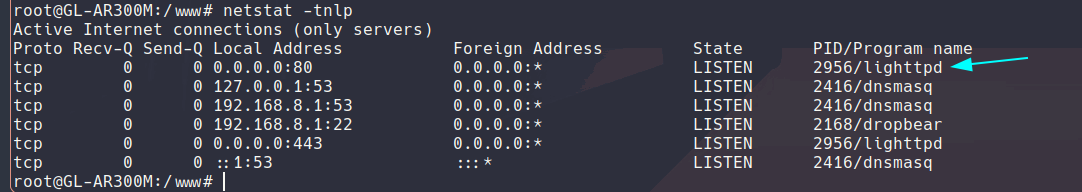
The config by default for this is located inside of /etc/lighttpd I used to use lighttpd back in the day when I had a pentium laptop that was to shitty for running apache2 while I was running other stuff on my old garbage ubuntu setup the computer would get hot when I had ssh, apache and other service running for some reason :c
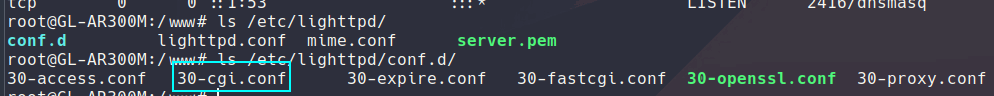
Highlighted is a cgi.conf file which is what I thought I should focus on cgi-bin is great to create vulnerable apps since it basically allows a web browser to run bash scripts. With this I am now able to modify the config and allow shell scripts:
@@ -15,6 +15,7 @@ server.modules += ( "mod_cgi" )
cgi.assign = ( ".pl" => "/usr/bin/perl",
".cgi" => "/usr/bin/perl",
".rb" => "/usr/bin/ruby",
+ ".sh" => "/bin/sh",
".erb" => "/usr/bin/eruby",
".py" => "/usr/bin/python",
".php" => "/usr/bin/php-cgi" )
After adding the /bin/sh as a cgi-bin interpreter I can just drop a vulnerable shell script inside of /www/cgi-bin. Since every script in that folder will be executed.

After that I just had to hide a few flags here and there and it was a cool little CTF ^^
Write Up
I'd like to put a little disclaimer if you found this article because you discovered the wifi network in a conference and think you will get a free beer by using this sure man but the beers are out of my pocket give it a proper shot at least :)
Initial Access
So you would discover the Free beer wifi in my case it is called GL-AR300M-810-NOR but in the future the SSID will be clear that it is a CTF I just don't want to spoil that bit ^^
In the example I am using a wifi pineapple to attack the wifi but you could use any wireless adaptor that can get into monitor using airmon-ng. From there you will see a client connected to the wifi. Basically what you have to do is capture the handshake of the WPA2 Encryption to brute force it later. I will do iterations with WEP in certain conferences to change it up a bit as well I think. After clicking on the little arrow next to the encryption type I have the option to start the capture and deauth the clients which I do and I then get a partical handshake for the wifi.
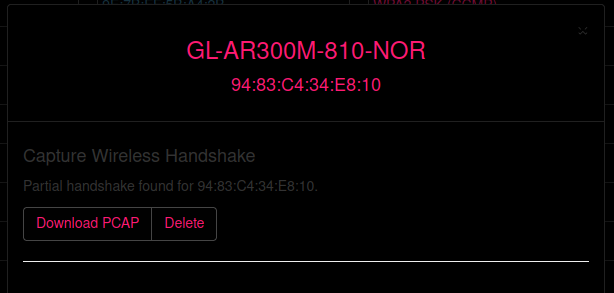
You can also open the file in wireshark which would give you a pcap like this:

You next have to convert the file into something hashcat can crack which would be done with the following command:
# hcxpcapngtool -o hash.hc22000 -E wordlist ./file_partial.pcap
The cracking can then be done with the following command:
# hashcat -m 22000 ./hash.hc22000 /path/wordlist.txt

If you can't crack this password just think outside of the box and you should just be fine.
Recon
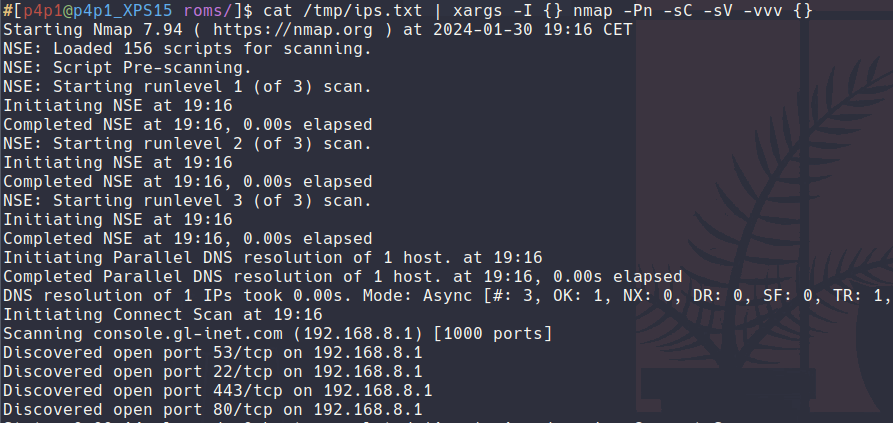
From there you have access to the network so you can try and find out what is running two quick shorthand I would run...
$ fping -g -a 192.168.8.1/24 &> /tmp/ips.txt
$ cat /tmp/ips.txt | xargs -I {} nmap -Pn -sC -sV -vvv {} -oN nmap_scan_{}
The nmap should then provide you with a few clues like a web portal that is accessible.
Now you might loose time with that web portal there might be CVE's I am not aware of but this bit is a rabbit hole since there is an easier way...
Exploit
On web engagements the first step should be robots.txt so after navigating there I can see a cool disallow entry... Even though output.txt is not accessible :c
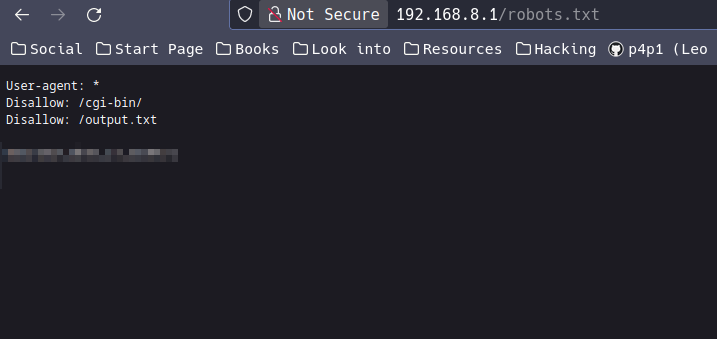
You will get your first flag here congrats but the rest is a bit more tricky most of the common enumeration techniques like gobuster will not work since the router will always return 200 'OK' for any path and finding hidden paths will require a more involved system. During a normal request there is 9 lines per request if we just start by checking everything that is above 9 and slowly increment we will get at some point a request with more that 9 lines or a bigger size you can use BurpSuite which would be great but here is the ffuf command:

From there you can find a hidden web page that has some cool stuff...

This message is quite explicit we can run commands inside of the server with this basic debug page but after running commands we cannot really see ouput of the command... Remembering earlier the output.txt file let's have a look...

From there you have code running on the router I'll let you figure out the rest :P
Thank you so much for reading you can support me on github sponsor and check out my twitter to get latest news about this blog and follow me on github for new code things :)
Categories
p3ng0s
Questions / Feedback
Donate

If you like the content of my website you can help me out by donating through my github sponsors page.