Ice - Gettin' cold
Created on Wed. 28 April 2020
This box was very fun, I really enjoyed completing it but I found it was to easy. So I decided to try and exploit it with a some source code I found on the CVE-2004-1561 page.
Using this source code I wanted to be able to run some simple shellcode on the machine to pop-up calc.exe.
I downloaded the exploit from the exploit-db page After downloading the source code, I found it very messy so I decided to clean it really quickly so that I could start working on the exploit. The big problem about the source code was that all of the "\" where missing on the escape characters.
After that I compiled the .c file with clang, and ran the binary:
clang 568.c
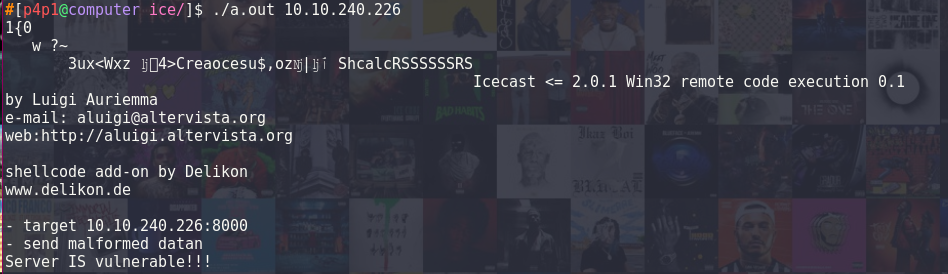
So now that I new that the exploit worked I started looking into the shellcode provided by the current exploit. The shellcode provided downloaded a version of netcat for windows on the machine and ran it listening on port 9999. Visiting the download link for netcat I saw that the .exe file was not hosted anymore.
Then after some research I found some shellcode so that I could spawn a calculator on the machine. In metasloit I ran the screenshare command and started looking at the screen of the victim.
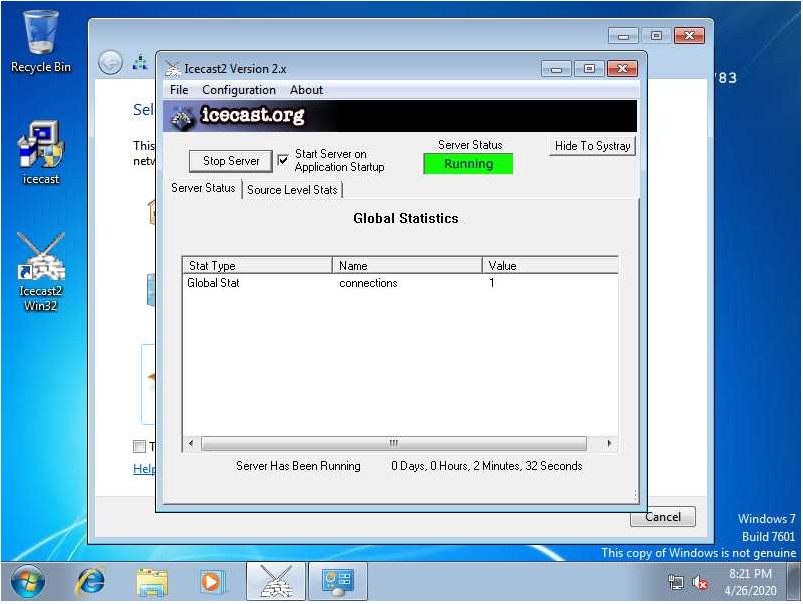
On the screen there was a few windows open but at least I could see the screen correctly so that I could debug the exploit in case. I then implemented the shellcode to spawn calc.exe and looked back at the screenshare.
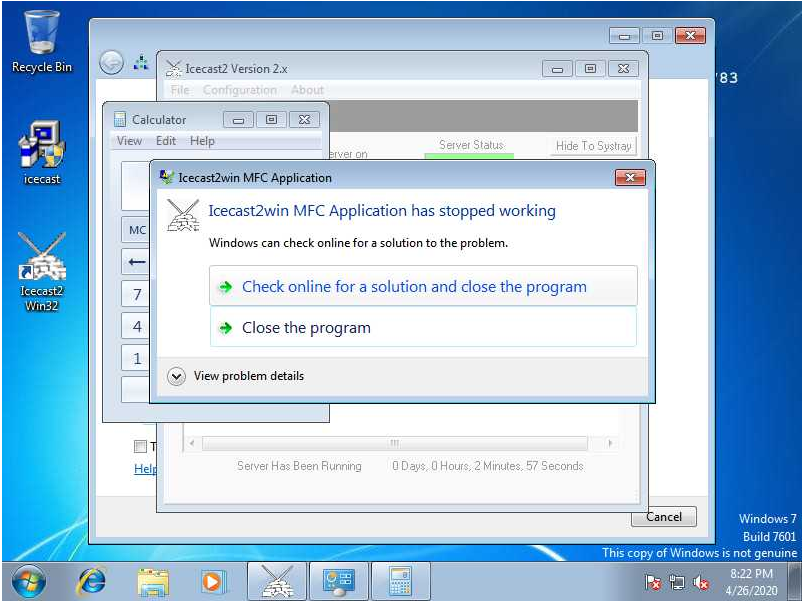
Thank you for reading, please follow me on Github and read my other write-ups :)
My tryhackme account
thm-badge-workflow

A github workflow to add your tryhackme stats to your github profile.
store | How it was build | repoLinks
Questions / Feedback
Donate

If you like the content of my website you can help me out by donating through my github sponsors page.