PWA Phishing
Created on Mon. 22 Jul 2024

Well I got beaten to this one to be fair I preferred playing skyrim than rushing this blog post. I discovered these progressive web apps from funny enough a French pentest company over on linked-in. Up-on doing some research on them I got a popup on my phone:
Download the XYZ app. Usually that wouldn't shock me but in this case the pop-up was a android system one from the base OS so I thought what is this, is the web-app calling some API on my phone so I digged deeper. Full disclosure mrd0x did do a great blog post about this topic that you should check out here
Progressive Web Applications
First lets look at PWA on a legitimate use case I have setup this very website as a PWA through the creation of the manifest.json file at the root of the website this has two main repercussions that I think are interesting.
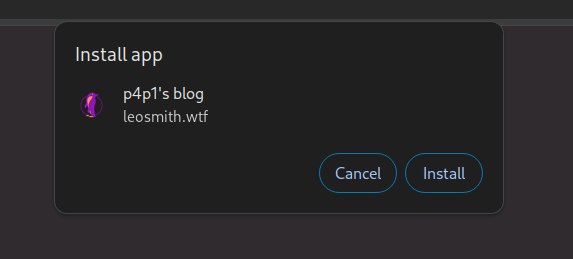
These amazing system looking pop-ups that look legit because they are and second is this when you open the app there is no url bar:
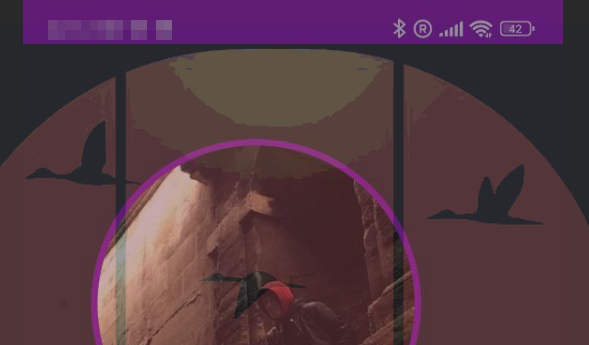
Before anything security wise let's look at the manifest.json file. We can set a lot of cool things inside of this file from the name of the application it's icons and also it's start_uri:
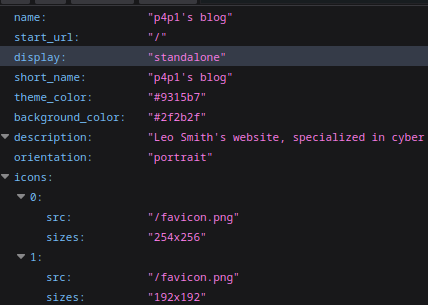
Now these features in the context of a legitimate application are quite cool but if you think about security for a minute this is quite funny you can basically set any icon any name for an app that has a install pop-up that is cross platform and is system specific so fully legit. To note also that if this is opened on the victim's end there is no URL in the top bar, so no real reason on how to verify if the page is legit.
Weaponisation
My first idea when I saw this was how to turn this into a powerful phishing toolkit. The first idea I had with this was Modlishka the main problem with this to me was the subdomains that this tool generates to track it's "infected" sessionss then I thought of using evilnginx2. This would work more on how later but I am not that versed with this tool to push it to have my own manifest.json file on that end even though I am sure it is possible. I also thought of an other venue where you could be able to use apache and custom redirects to make it more easy to be plugged with other attacks.
Inside of apache2 you can setup a sort of Proxy System where on your machine if you host an app on port 8080 for example you can set a URI or even a subdomain to proxy the traffic on this app. Now in my example I am using my website but you could do it for any other:
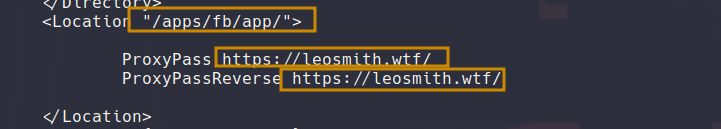
As you can see if someone visits the endpoint /apps/fb/app on my website you should then see my website:
Brilliant now that I know it works I need to have it so that the URI of my manifest points the endpoint of the URI and we should be good to go:
{
"name" : "Facebook",
"start_url" : "/apps/fb/app/",
"display" : "standalone",
"short_name" : "Facebook",
"theme_color" : "#036DE4",
"background_color" : "#fff",
"description" : "Facebook",
"orientation" : "portrait",
"icons" : [
{
"src": "https://store.p4p1-leosmith.xyz/apps/fb/favicon.png",
"sizes": "254x256"
},
{
"src": "https://store.p4p1-leosmith.xyz/apps/fb/favicon.png",
"sizes": "192x192"
},
{
"src": "https://store.p4p1-leosmith.xyz/apps/fb/favicon.png",
"sizes": "512x512"
}
]
}
Brilliant with this we now have a functioning malicious PWA!
Store
From this I decided to make a quick static store page that showcases a simple phishing scenario: A victim would either be tricked into thinking this is a legit store or a company only store to target corporate phone devices since these PWA's only need chrome on the phone to function.

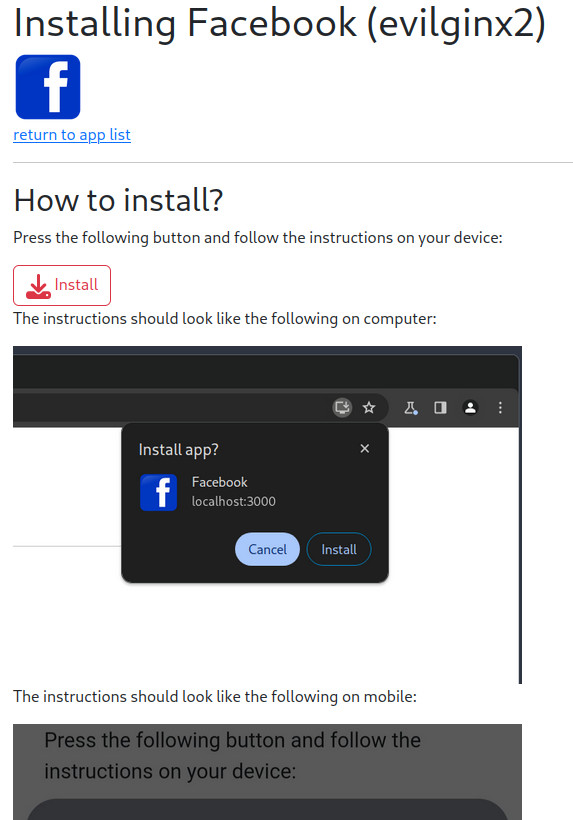
From there a user would get a tutorial on how to install the malicious applications:
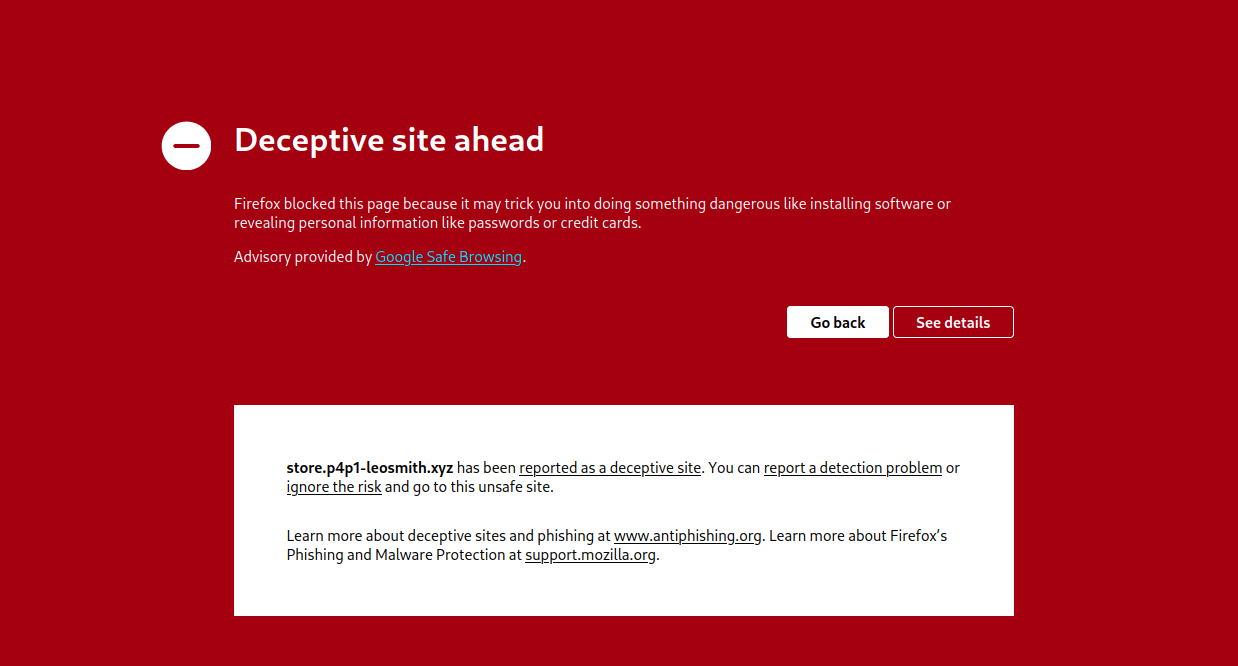
And then forget about the existence of this website. Note after setting up this website and testing it out for around 2 months I only got the domain blocked 1 hour ago so it takes a bit longer for sauron to catch on this phishing technique might be useful for a red team of course don't do anything illegal:
Thank you for reading you can support this blog directly through Github sponsors also stay in tune with me through using my PWA or just following me on twitter :)
Categories
Links
p3ng0s
Questions / Feedback
Donate

If you like the content of my website you can help me out by donating through my github sponsors page.