Ultimate Home Lab
Created on Sun. 03 Dec 2023

I'm back! Ever since 2 years ago I started working on making my own little home setup with cool services on my network. I wanted to build a network where I could see live the network for debugging and to monitor what was running on it. I also spend a lot of time working on repairing my installs and desktops so I needed a service to boot fast recovery tools on my machines
This is where my current little project came in. I setup a router I bought for monitoring and debugging purposes. I was also fed up of having adds online so this is where an other section of this project came in. This year for Christmas I bought myself a openwrt router that I had in mind to customise and secure to the max so that I could run multiple services on it to fit my hacking needs.
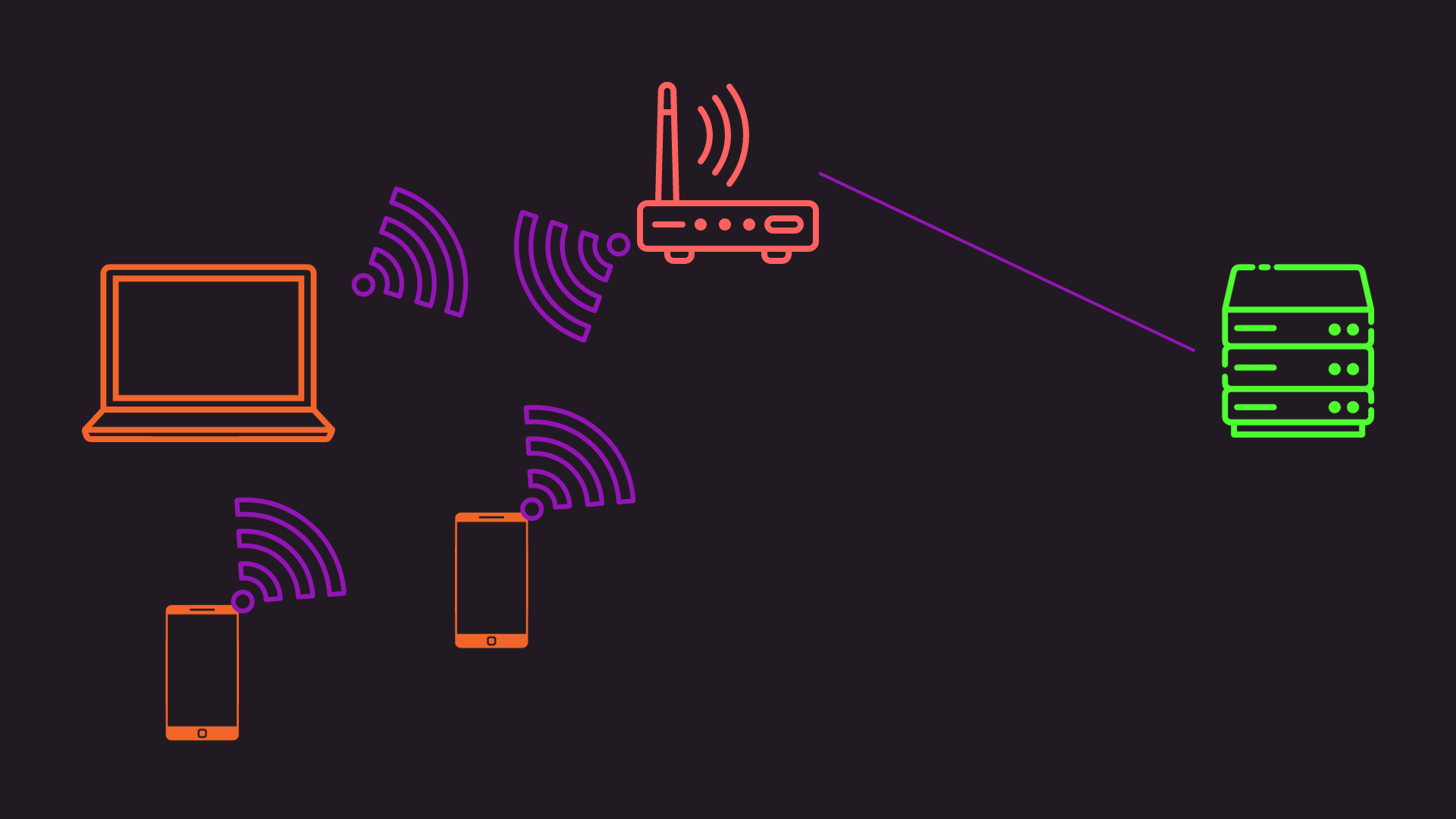
The way I designed my network is actually quite simple my router has a little rasp-pi server hooked up on a special Ethernet port with a static IP address for all of the tools and most of the rest of the network is wifi. Unless I setup a new router where this will be plugged in through cable as well.
Router setup
The first main central part of my network is the router or the GL-INET A1300. This is a open source travel router that comes pre setup with it's openWRT firmware perfect for customization since you can be root on that router with ssh and all the advanced config that comes with it!

These routers made me fall in love with setting up openWRT routers they are so easy to use out of the box which I found a little crazy it uses the same package manager as the wifi pineapple opkg since the pineapple is based on openWRT with a custom front-end for all the attacks and such. So coming from that world it was quite simple to understand how they worked. By default these routers come with such cool pre-setup apps like openvpn, add guard and wireguard. This would allow you to setup the router in such a way where you are always constantly connected to a VPN which would be great to have a router like such setup with your red team cloud setup!
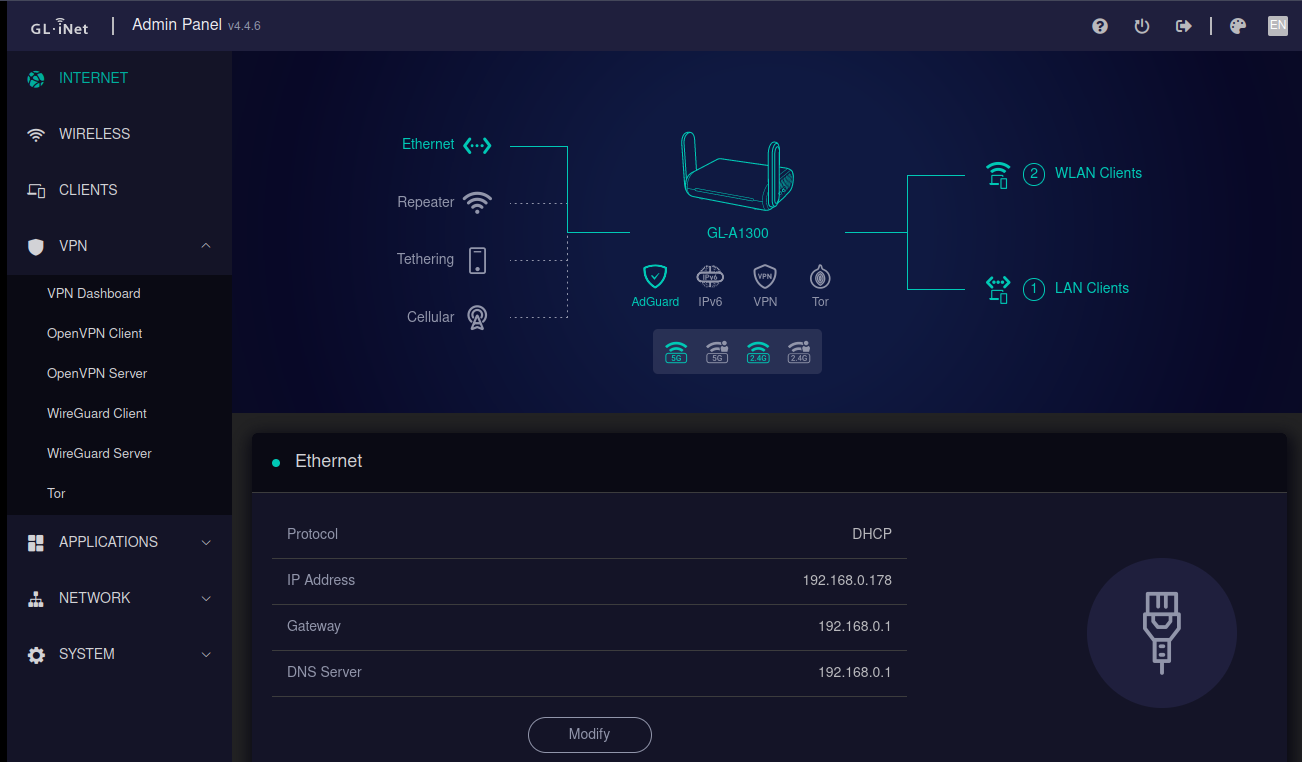
Since this is a openWRT router it also comes with the advanced admin panel luci which is even cooler for more advanced things like log monitor and setting up firewall zones etc..

Coming from a shitty TP-Link router at home that I couldn't modify at all this is amazing I feel like I have so much power now over my home network!
Honestly on the normal router end the only thing I decided to setup was the Ad Guard thing this is the only normal consumer thing I would personally want! With AdGuard it is actually quite funny since the router handles a bit of the DNS it is really funny to observe everything on the pannel:
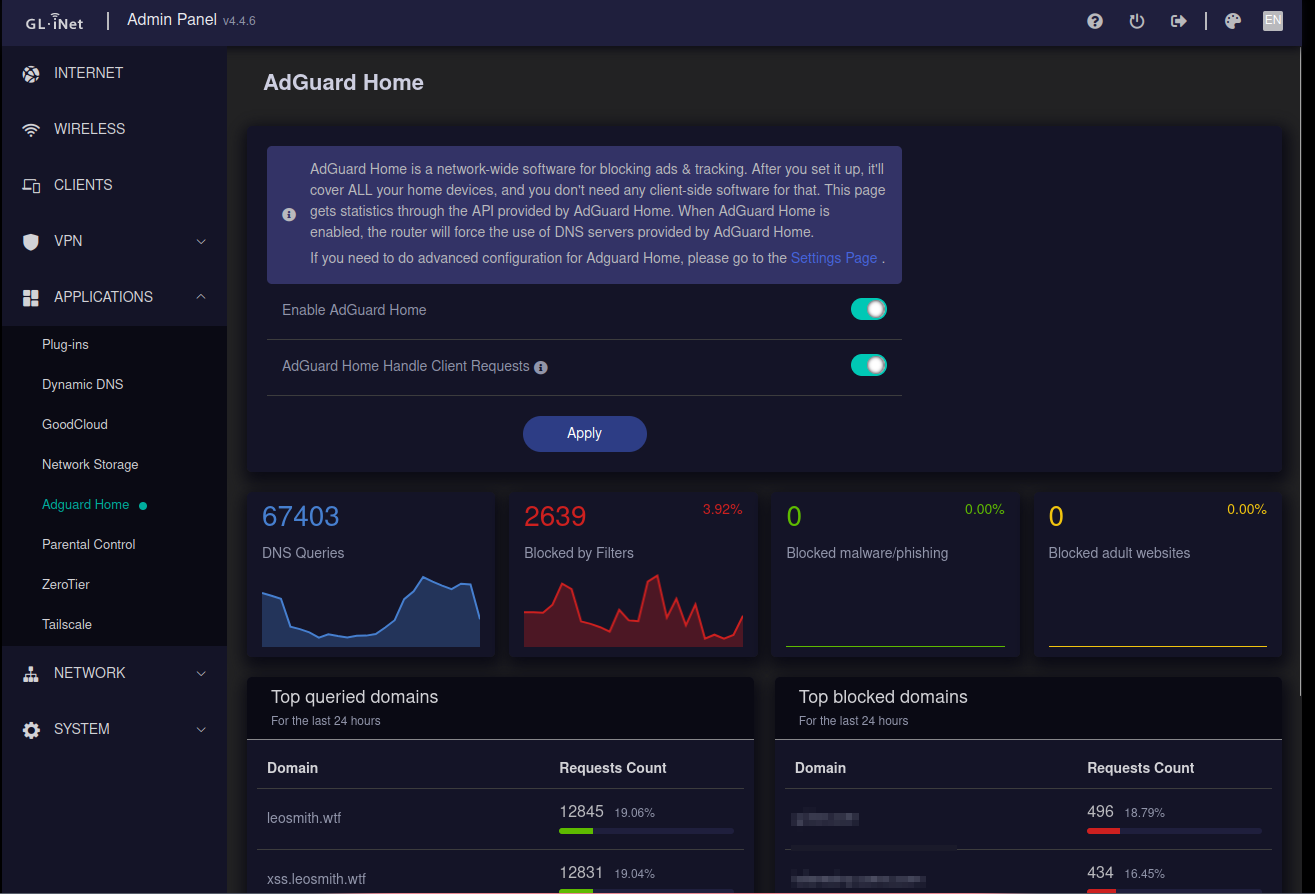
After activating Add Guard you also get the "advanced" dashboard which is just the normal ad guard dashboard where you can also define more advanced blocking like phishing and such. I thought since at home I'm not the only one using the wifi and other people usually are my weakest link network security wise this would be a great thing to setup!

After having this run for a bit I managed to find the Chinese government snooping around:

Monitoring tools
Now this is the stuff I actually was most hyped about. At work I started doing a bit of threat intel using tools such as rita and zeek and I wanted to have that setup inside of my network! The first step in setting up the monitoring is that I needed a mirror port on my router. A mirror port is where all of the traffic of the network is mirrored on too so that it can either be monitored / inspected. With openwrt this is easy as hell you just need to SSH find the correct port and run 3 commands with the appropriate port number:
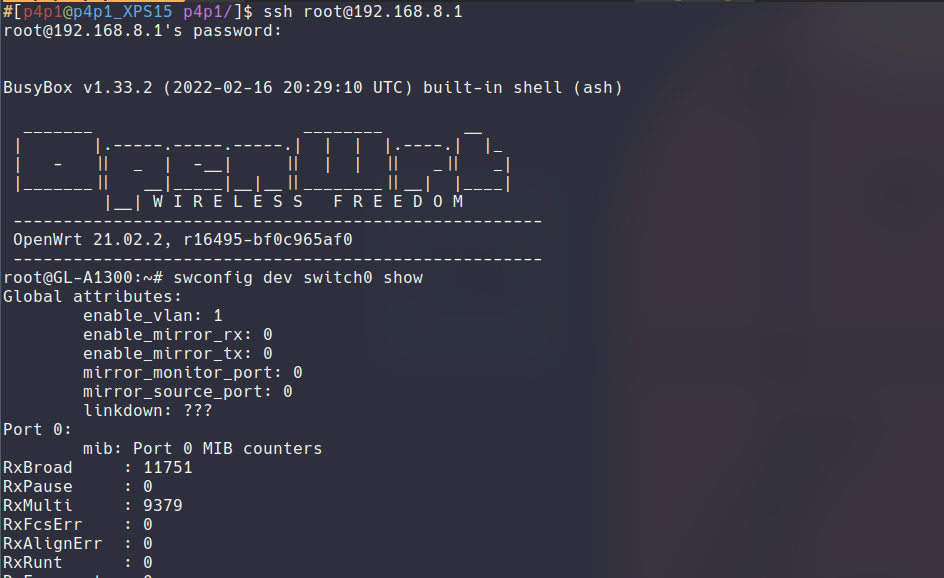
I setup my mirror port to be the opposite port from the WAN port that I plugged in to my ISP router, for me in my router that port was number 3:

Here are the commands I had to run:
$ swconfig dev switch0 set mirror_monitor_port 3
$ swconfig dev switch0 set enable_mirror_rx 3
$ swconfig dev switch0 set enable_mirror_tx 3
From here opening up wireshark with a ethernet plugged in to that port I am then able to inspect all of my traffic (more on that in the next section since I was mad stuck on what service I setup next)

Now I am able to run a tool like zeek to capture network packets and view long connections on my network (perfect to see if any beacons are running on some of my guest hosts)
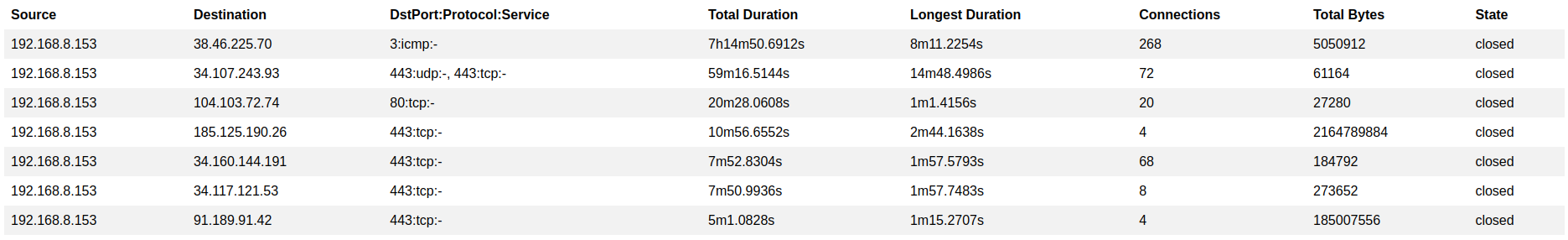
Netboot.xyz
After turning my router into a all powerfully spy/debug machine I also needed a network boot option. I discovered this project netboot.xyz online and thought this would be an amazing add to my network. If any of my tester friends came over they could quickly from their laptop boot into the network and potentially test out my OS p3ng0s directly from the network or just use any ISO offered:
What is also crazy about network boot is that you can access it from virtual machines as well as computers on the network. Truly one of the most useful tools I have ever found. To setup netboot I decided to go ahead with the self hosted method since I will eventually port my arch linux distro to it ^^ since my OS has cool live boot tools included. To do so I used their official docker container that can be found here. From there it was as simple as running the following command while the dockerd back-end was running:
sudo docker-compose up --build
From there you need to configure your dhcp server to respond correctly to "boot ask" requests not sure how they are properly called. Now this is the bit that took me a good 48 hours with chat GPT debugging I'll be honest but chat gpt was fucking wrong as usual and I just found the solution by trying everything I could think about the desperate last try method (100% recommend).

Above is a DHCP packet in wireshark explaining how the machine asks the network how it should boot from it. Inside of option 55 the machine asks the network the different information to boot from the network. In this packet the type of boot is also provided (legacy, efi, etc..). In my case I only setup legacy but I will add efi support later on in the future. From here the router should answer with a packet like this:
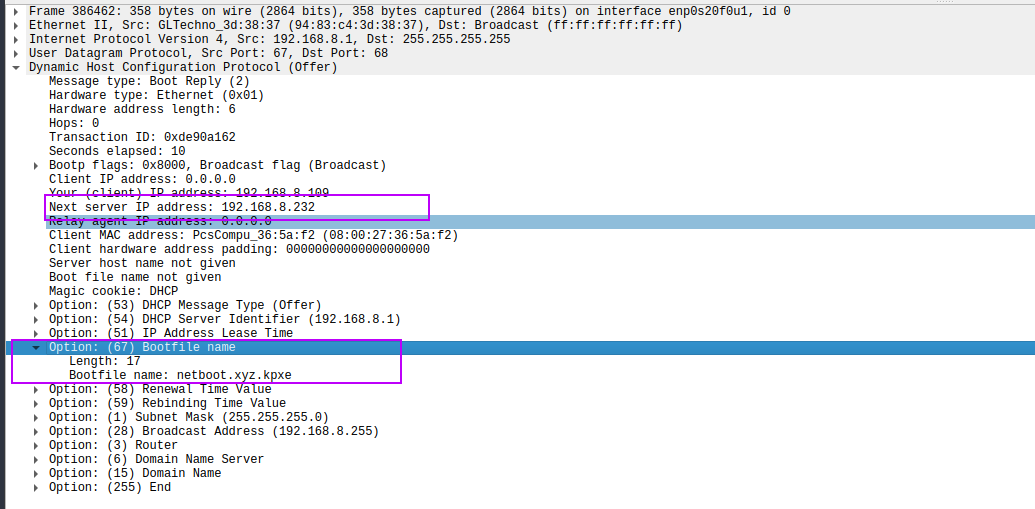
This packet has the next-server, this is where the tftp boot server is hosted and the filename to boot from. In my initial setup following tutorials this was not working for some reason I was not able to have those flags set. The commands where not cutting it so I edited directly my DHCP config to have the following and it magically worked!
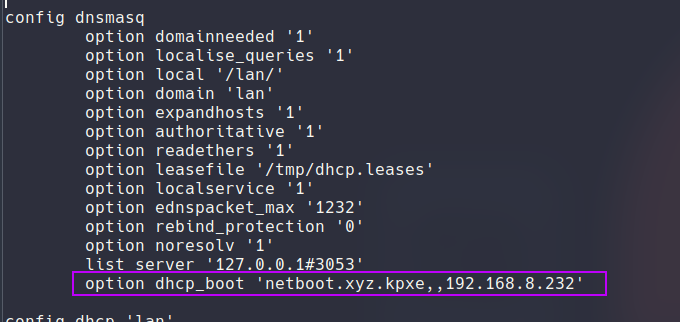
With this added and DHCP restarted I was then able to boot from network!
Thank you so much for reading! This was honestly such a cool project for me to do. I loved every second of it follow me on github / linkedin to see the next work I do I was convinced by cspider to get myself a twitter account so stay tuned to that I'll probably be using it as a mailing list for the blog.
Categories
p3ng0s
Questions / Feedback
Donate

If you like the content of my website you can help me out by donating through my github sponsors page.