$ Presentation

Your growth is my priority, With the services I offer I invest myself professionally in guiding you on securing your organisation. My expertise meets education, My past experience as a software developer and cyber security teacher allows me to understand complex architectures and provide comprehensive reports. The reports can then be used as actionable insights to allow your teams to understand and foster a culture of security awareness. A culture of collaboration, I will work in tandem with your teams during penetration tests to make sure your current defenses work as they should do and so that my work fits your company unique dynamics. To foster complete collaboration, I maintain complete transparency in my penetration testing process, ensuring your teams grasp the intricacies of my attack paths and strategies. Tailored Support, Our partnership would ensure that security solutions are integrated seamlessly with your current and future operational processes.
Offensive Security
Elevate your security posture with tailored offensive security testing. Collaborate with me to prioritize growth and organizational security. I provide comprehensive insights to foster security awareness within your teams. Through close collaboration, we fortify defenses and integrate solutions, ensuring holistic protection. Partner for testing, including Network Penetration Tests, Web Application Penetration Tests, Wireless Penetration Tests, and Red Team Simulations. Gain insights and enhance security posture.
Defensive security
Prioritize the security of your infrastructure for sustained growth and protection against threats. My expertise in Security Operations ensures the resilience of your environment. Services include Active Analysis, Vulnerability Scanning, and Patching. Benefit from tailored security practices and training sessions, enhancing your team's awareness and readiness.
Still deciding?
If you still are not sure in starting our partnership together you can view a full detailed list of my expertise inside of the following document and on my Linked In. A sample report is also provided here to provide you with a better understanding of my work. I also have provided bellow a full detail of my methodology as well.
$ Methodology
To ensure quality service I am totally transparent on my methodology and working culture which is one of the strong points I would offer to you. My main goal through our future relationship is to enrich your understanding of computer security and allow you to position your business securely inside of the cyber space with an unmatched understanding of the risks. With my years of experience inside of the field I am able and positioned to deconstruct complex security problems and explain them in a simple and digestible way.
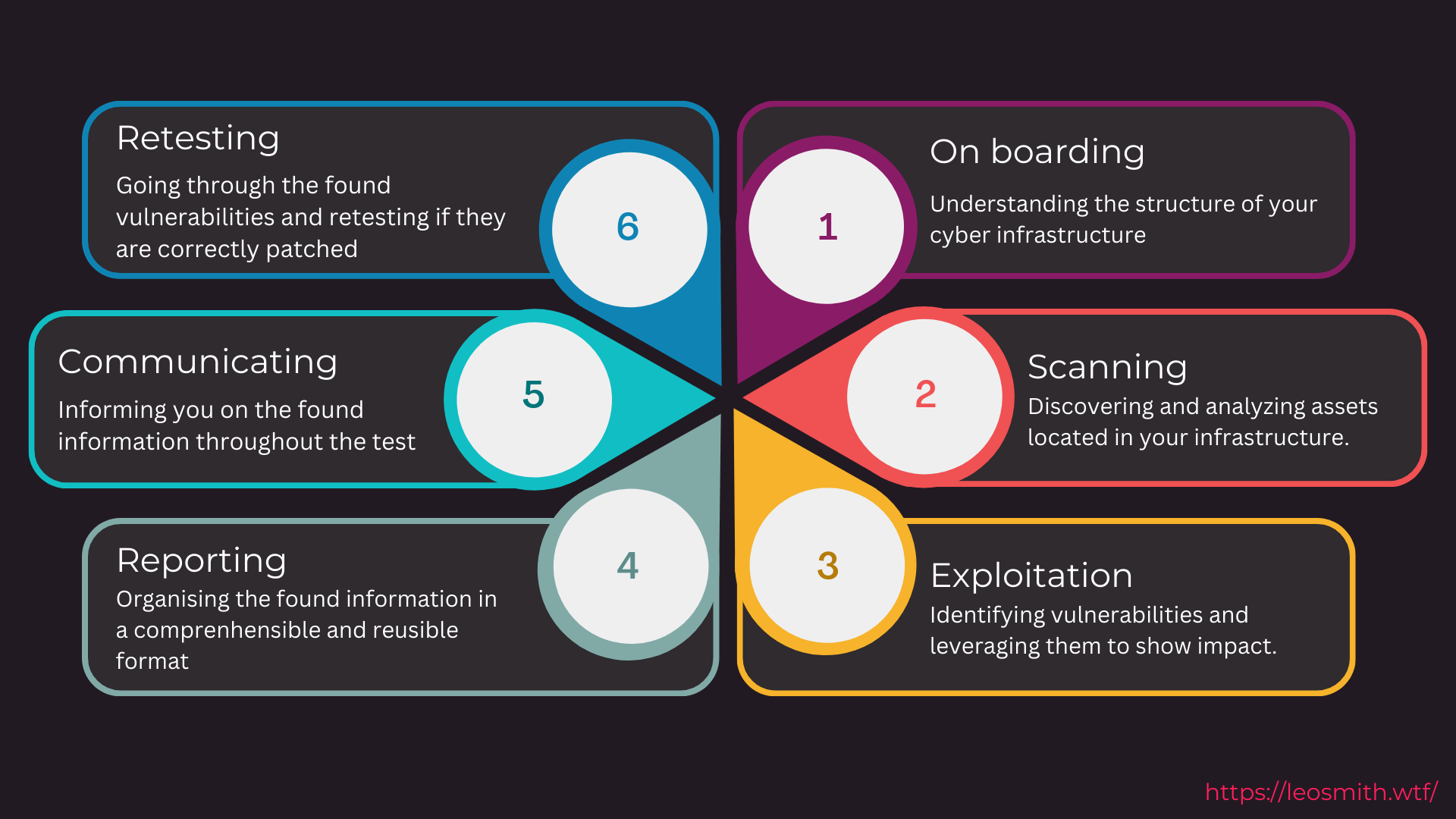
Assessment Methodology
To ensure I cover all of the tactics, techniques and procedures utilised by threat actors I use a basic, easy to understand and solid methodology that makes sure you are able to understand what I assess inside of your environment.
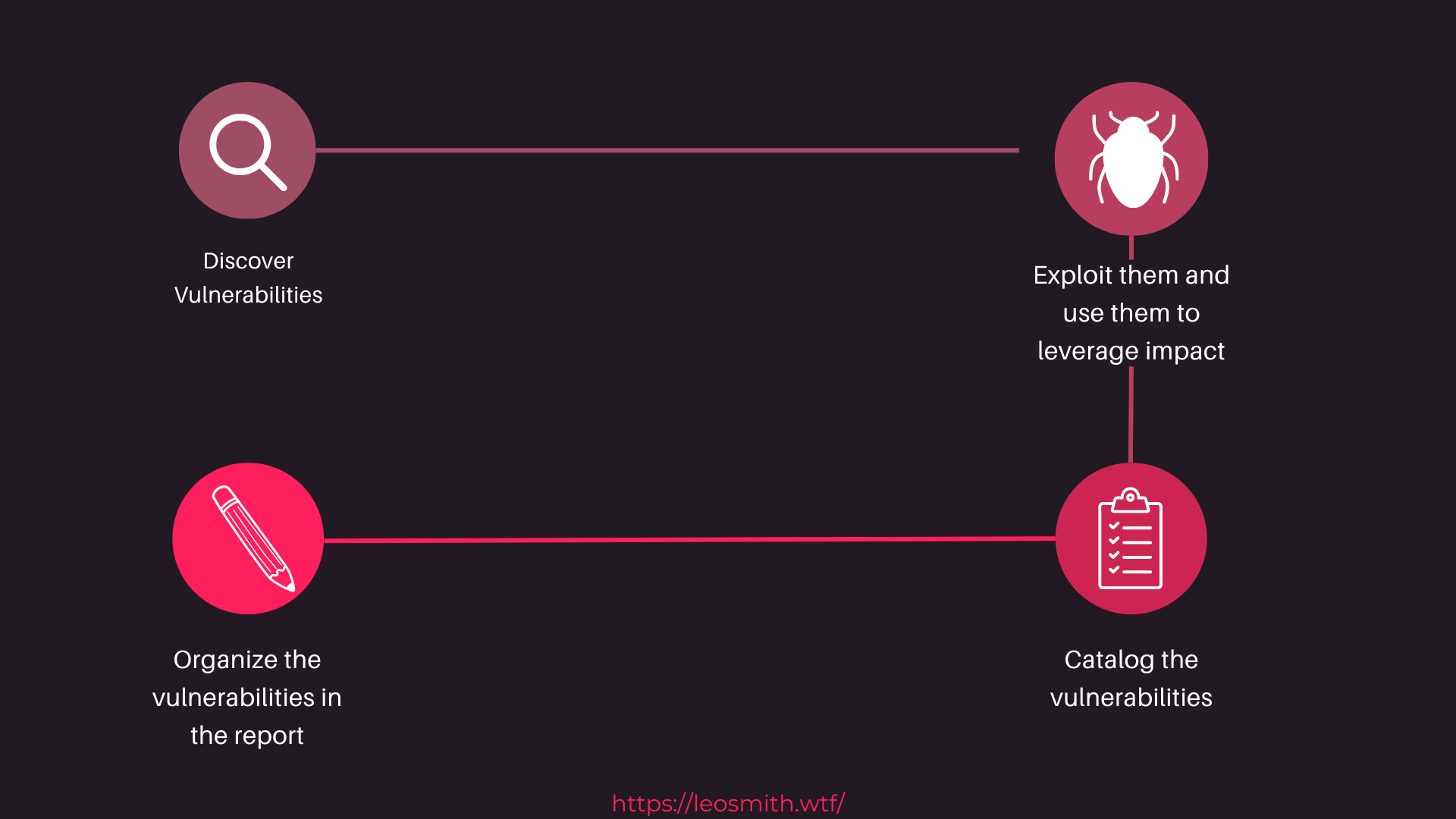
Reporting Methodology
To optimize the acquisition of pertinent information during our collaboration, I furnish comprehensive reports elucidating my work. These documents are presented in an easily comprehensible format, facilitating a thorough review of all necessary details to ensure utmost confidence and assurance in understanding complex security challenges.
$ Work & Accreditation

I've been working in computer science and information security professionally since 2017. By going through this section you can have more information about my past work and industry relevant certificates that I acquired over the years.
Proudly Trusted By
I have worked for multiple companies throughout my career and I am proud to have worked with them to secure their infrastructures and data.








My Accreditations
Built Industry Relevant Tools
I have also created tools to assist my work and to allow other penetration testers to use my methodology.
I also maintain a blog where I publish my research and the latest cybersecurity offensive topics I work on in my spare time. Bellow is the latest post I have been working on.