HTB ProLabs review
Created on Wed. 17 Jan 2024

Like previously stated in my last post this has been a 10 year journey this year and I am happy that I got quite far after spending time to look at the past in the last post I'd like to talk about current / future stuff. I've been doing certificates for at least the past 3 years and after discussing OSCP and the more expensive ones let's go through the cheaper ones.
Before I dive in to the individual certs I'd like to point out that the knowledge that I acquired during the past 4 certs I did (OFFSHORE, RASTALABS, CYBERNETICS and APT LABS) is literally the most amount of knowledge I got at once. None of the expensive certs with proper courses can get on the level of these certificates I just did these certs compared to those exams where way way way harder there is a lot of help on the discords except for APT LABS, more on that later but because of this challenge / difficulty you get a lot of value out of those certificates.
I honestly after doing those certificates I do not see the point of OSEP or any of those expensive certs other than HR recruitment anymore OSCP EJPT where great to get started but the HTB pro labs are honestly so rewarding and good to train I would honestly use those in the future as a gage for recruiting someone for pentesting over OSCP since they are so affordable anyone could do them and test you on your core understanding and skill a lot better than these "Industry Standard" certs like OSCP. After completing OFFSHORE I honestly just thought that it was just a more hardcore OSCP.
Pricing
Quick foreword before talking about the certs more in detail is pricing. HTB are honestly really fair on their new monthly pricing model for around 50E a month you get all pro labs no strings attached. It is a lot better than OSCP 1.6k. There is no hand holding on completing these labs the only help you can get is either Discord where you can ask the community for help on certain vulnerabilities and next steps but nothing else no writeup are available online. Now some people leak it but it does defeat the purpose for some pro labs but I think for the harder ones mainly APT Labs you would need it since the discord is fucking dead since everyone is kinda scared to do that one.
My personal objective
The main objective that I set myself on these pro labs was to refine my checklists and overall penetration test process. I have made on notion and at work checklists to assist me during audits and I wanted to either add new techniques / tools to the checklists and also fill up the more obscure vulnerabilities report templates to progress in my coverage for future engagements. This helped me structure how I tackled most labs and really helped me when I took brakes here and there. The whole thing took me 5 months if you put everything back to back. I also wanted to setup maybe more advanced tools inside of my workflows specifically Havoc that because of these certificates I ended up contributing a lot towards.
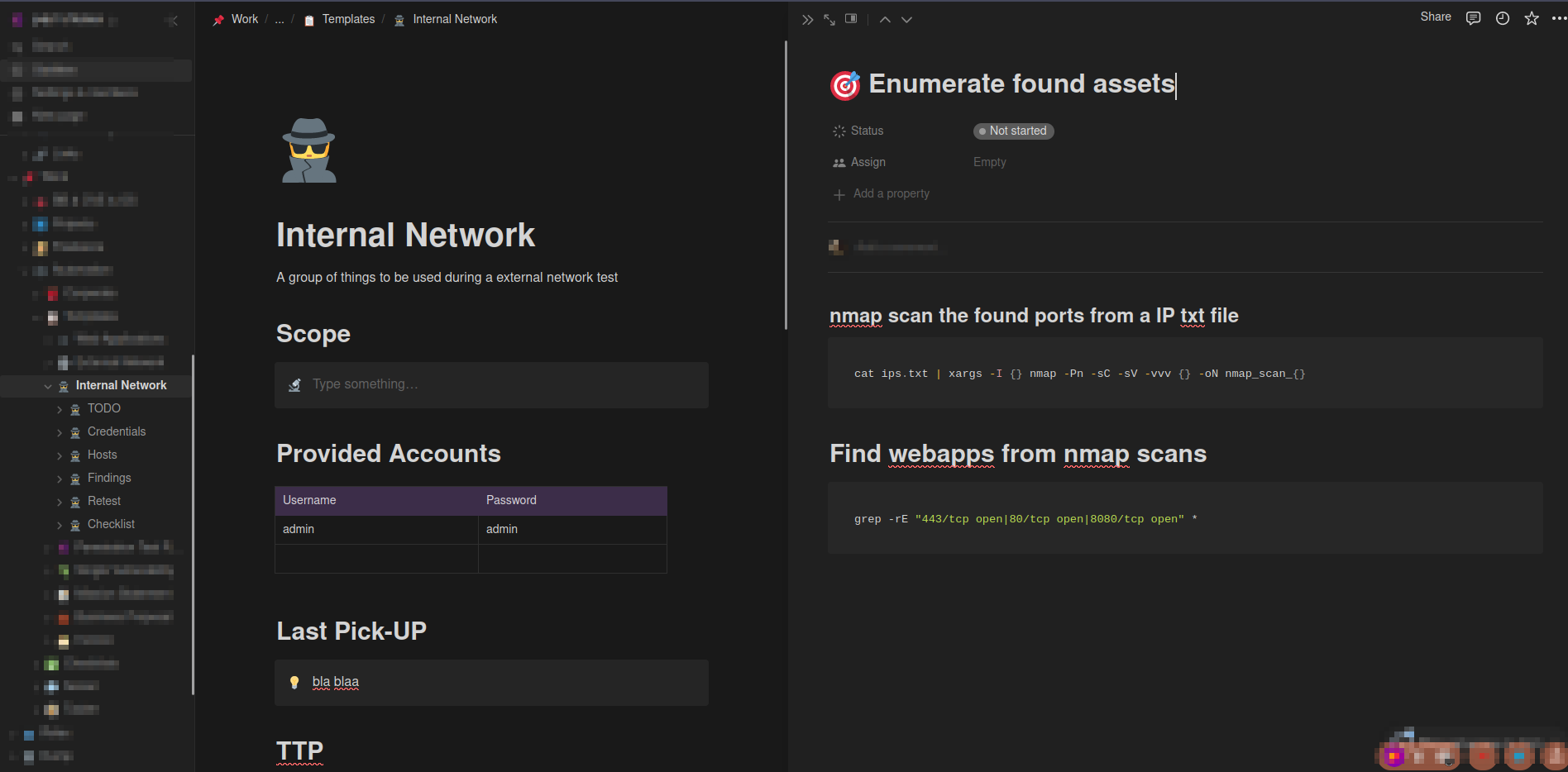
I also ended up automating a lot of redundant tasks through red team so that in the future I can optimize certain engagements!
The Dante

This certificate I previously reviewed in the port, My view on infosec certs. I still think it's good to revisit this post since my opinions did change a bit since I finished most of the HTB pro labs now and looking at the different vulnerabilities that come on Pentest Level 2 aka OFFSHORE it's nice to see the differences. What I wrote back in the day for the Dante still stands it is a great certificate for OSCP training I thing anyone aiming for the OSCP should do the Dante. Vulnerability wise the Dante does have a few oddities but for a junior penetration testing cert it is perfect. It covers most things that would be entry level and does go a bit in depth on obscure things that are beneficial in the long run. For someone looking to do the Dante I would recommend an approach where the Dante should be your training on Reconnaissance and Analysis I think the Dante shines if you just focus on practicing your Reconnaissance and Analysis first and outline your personal penetration test process through it instead of just thinking Pwn Pwn Pwn which is a mistake everyone does in the beginning.
Zephyr
I did not do this one yet and will do it in the future as a refresher after APT Labs trauma has worn off it is currently January 27th 2024 and I think I might to this certificate around September 2024. So you will have to come back then if you want to see my opinion on that one.
Offshore

This challenging certificate is honestly not that hard. I have you could say real world experience that might make my opinion clouded but you could compare the Offshore penetration test to a normal to tackle company during an audit. A lot of the vulnerabilities are Active Directory oriented which is what you see on most corporate networks and most of the findings are things I've put in reports time and time again. After completing the OSCP and you are a average penetration tester I thing offshore might be a challenge on one or two vulnerabilities but nothing ground breaking. I probably could say that what makes offshore "Hard" is that it is time consuming a lot of machines have to be hacked and a lot of flags are more rabbit holes than an actual way forward to completing the network. This could feel like a problem or a negative overall but I think this is what makes Offshore the best place to start training on using more advanced tools like a proper C2 framework. Which is what I did during this pro labs after a few days of using just regular tools and metasploit that you would use during a pentest I took the famous C2 Matrix I just picked Havoc and started setting that up on my end to see how useful it would be. It become such an integral part of my workflow that I coded multiple plugins for it since then.
RastaLabs
After getting Havoc down inside of Offshore I was most excited for RastaLabs since friends of mine that completed it told me about the challenges in bypassing defender etc.. I will be totally honest Havoc might have been over kill because between the week before rastalabs I was tinkering with Havoc an bypassed the latest versions of Defender multiple times and was doing cool things inside of my personal environment at home and at work on the laptops as well. RastaLabs was still a great introduction to Red Teaming the beginning of the certificate and just the general path to compromise the network is what I liked the most about that certificate without spoiling to much. The beginning is extremely realistic since it takes a more External Pentest Approach with some OSINT / Investigation on their website and what not which comes back in the other certificates later on. I also really liked how you don't just straight go into attacking servers and services you really feel like you are on a corporate network with this certificates now a pretty small and insecure one but a corporate network non the less. My only complaint was that I found it too easy to my liking but I think for what it is it is amazing and done right after offshore maybe is what made it so easy to me since it felt like offshore was harder on some aspects compared to rasta labs. Also if I didn't know the process of pentest inside of an actual live company and without the previous red team experience I had at work this certificate would've been a lot harder for me I am sure.
Cybernetics
This certificate is what I expected rastalabs to be if I am honest it is missing the OSINT start that rastalabs had which is a real shame but the network is for sure challenging compared to rastalabs and the antivirus here did block me more than it did inside of rastalabs. The first inital network I exploited inside of cybernetics did leave me very confident but I got then hit by reality the moment I moved to the main network and the phishing section does not fuck around I struggled a lot more than I can admit in this post on this section and really felt relieved once I went past that section since it is pretty hard and a lot of research was done during that bit. Then after that it was quite smooth sailing up until the last 2 machines nothing really crazy and after offshore a lot of the AD attacks you are quite familiar with them so this section was quite easy. The last few boxes where a real struggle and really pushed my way of thinking it felt more like I was solving puzzles in a hacking realistic way than just ticking off a checklist of vulnerabilities which was amazingly challenging and rewarding. For cybernetics I mainly challenged myself by doing a lot of attacks on the AD network linux side instead of on Windows with Rubeus since I wanted to train my impacket skills through this certificate and I am so glad I did since they got quite useful for the last pro lab...
APT Labs
The big daddy of certifications. This one is no joke it kicked me around the last section of cybernetics which was all about puzzle solving in a hacking way with the struggles of the AV and things not going right when you run your tools with the fishing of cybernetics is exactly what this certificate is about everything here is hard the entry point going through the network finding vulnerabilities everything about this felt like a real penetration test. Usually during audits it's like a curve where when I start a pentest I struggle to figure out everything about the network with recon seeing if the environment detects certain attacks etc.. Then at some point during the pentest it clicks and I have all the information at hand to own the infrastructure, web application etc.. That is what apt labs felt like but longer all of the previous prolabs I finished them in 1 month or less APT Labs took me two months. I was honestly so done with this certificate around 3/4 in which you don't know you are 3/4th in because even if the flag system tells you your progress near then end (last 1-2 week) I was getting flags quicker than at the beginning but yeah most of the vulnerabilities are things that felt like sometimes I had to just pull out of my ass but after studying them and understanding how to exploit them it was very very rewarding.
Thank you for reading hopefully this helps you advance your cybersecurity carrer and give you a good picture about these certificates I recommend everyone doing those certificates they are just pure gold I have loved every second of doing these and I probably wont do many more certs I am a bit over these things I'd rather do bug bounty / CVE research now since I think for my resume that would be more beneficial than just practice / play grounds. I will revisit this post in a few months once I do Zephyr since I didn't complete that one yet I am waiting to loose a bit of practice to do that one as a refresher. Follow me on twitter and github to get the latest updates on my work and go try out p3ng0s :)
Useful links
p3ng0s
Questions / Feedback
Donate

If you like the content of my website you can help me out by donating through my github sponsors page.