Checklists in Cybersecurity
Created on Sat. 10 Feb 2024
Wesh Wesh Wesh le gang! In the past I did a blog post explaining my organisation in cybersecurity through using Trello and other tools I used to organise my work as a developer through agile and how that transferred to me working in cyber security and in the past I used tools like xmind to map networks and other not taking to keep notes during my first early engagements.
Obviously a year later I migrated to a more centralised way and I gave myself a bit more of a structure for all of my work. I'm not going to lie I migrated fully to notion. Sadly it is not open source and I am still looking if their would be an equivalent where I could not be tied to big corpo environments. But notion for what it is it works great! In this post take it as a tutorial on making checklists for your own and what logic I take to make those for my work.
HackTricks and friends
The lord the all mighty hacktricks and website of the equivalents are like the ultimate checklists for penetration testers and I think they are great tools for people to use in a pinch but in some corporate environments websites like hacktricks are blocked behind firewalls since they are "Hacking" websites.

This website was a few years ago my bible while I was training for the OSCP it had all of the information I needed to do some cool hacking. These websites are so good while you are doing a pentest to go through and I think they are amazing to showcase / find new attack paths or TTPS for your engagements. I also believe that they are a great place to start building your own checklists. Let's be honest if you want to be good at all of this you should make your own checklists. Here is a quick list of the hacktricks like I think are relevant for people that don't know.
Pre-Made Checklists:
Reinventing The Wheel
Simply put you can view the publicly available checklists and think wow why would I need my own checklists everything is already online for free. But I would argue that remaking your own checklists is an integral part of your learning and development. Since you could put your own exploits and techniques in the checklists and base yourself on the existing ones and add your own functionality / exploits. I personally did that I took HackTricks & OWASP and created my original Internal Network pentest and Web Pentest checklists. From there I added shortcuts to automatically fill in the checklists on some scan output to greatly make my workflow faster. When I find new exploits that aren't inside of my checklists I then add them to the checklists explaining how to exploit them:
Now with this let me showcase you a few example to base yourself upon
My Examples
I organised my checklists with at the root of the projects distinct categories depending on the type of audit:

Main Categories
From the main types of audit I'll do I structure my audit with a simple todo list that will show me what actions on a macro level that I have to take on an audit:

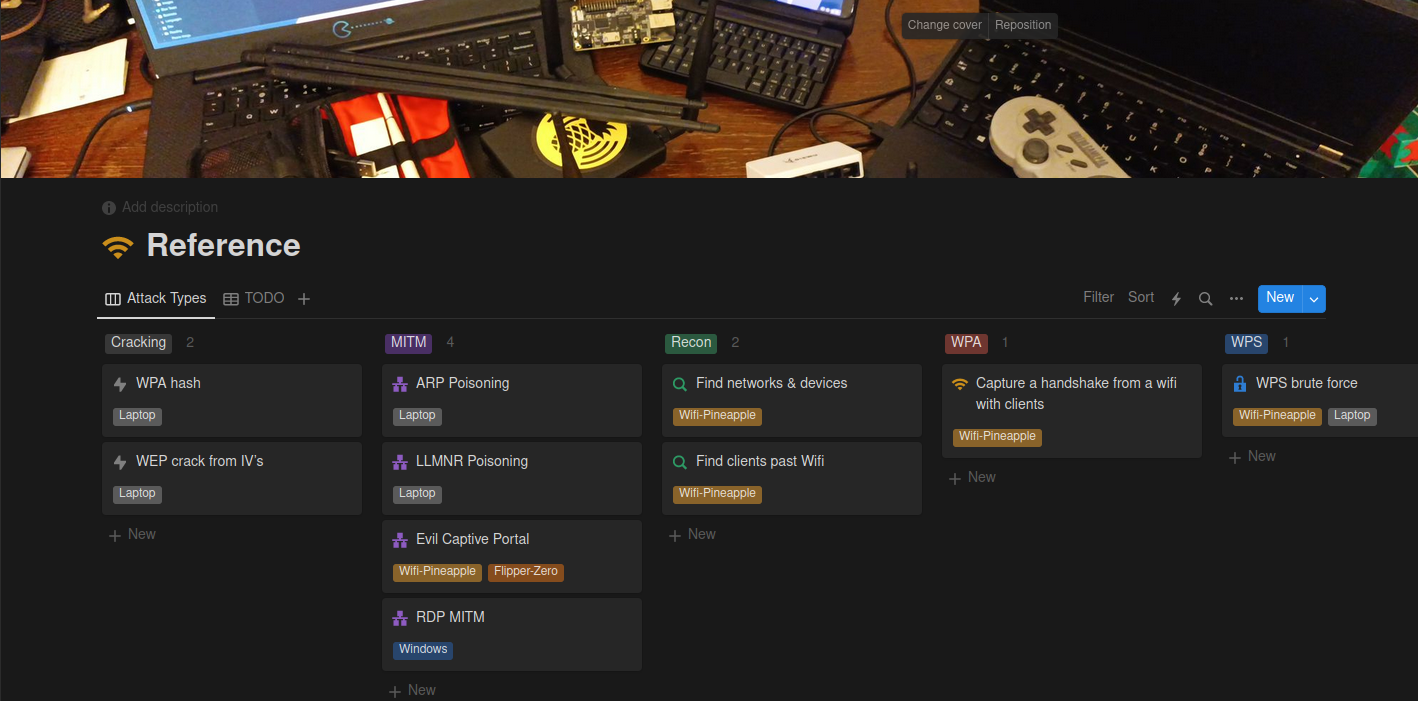
From that I organise the different assets (Endpoints on webapps, Hosts on network tests)

I used this approach on APT since this is why this section is blurred but it shows you a quick overview of one during an engagement instead of just a empty one. Then usually I need to sort through my findings for during an engagement like what did I find what did I exploit etc..
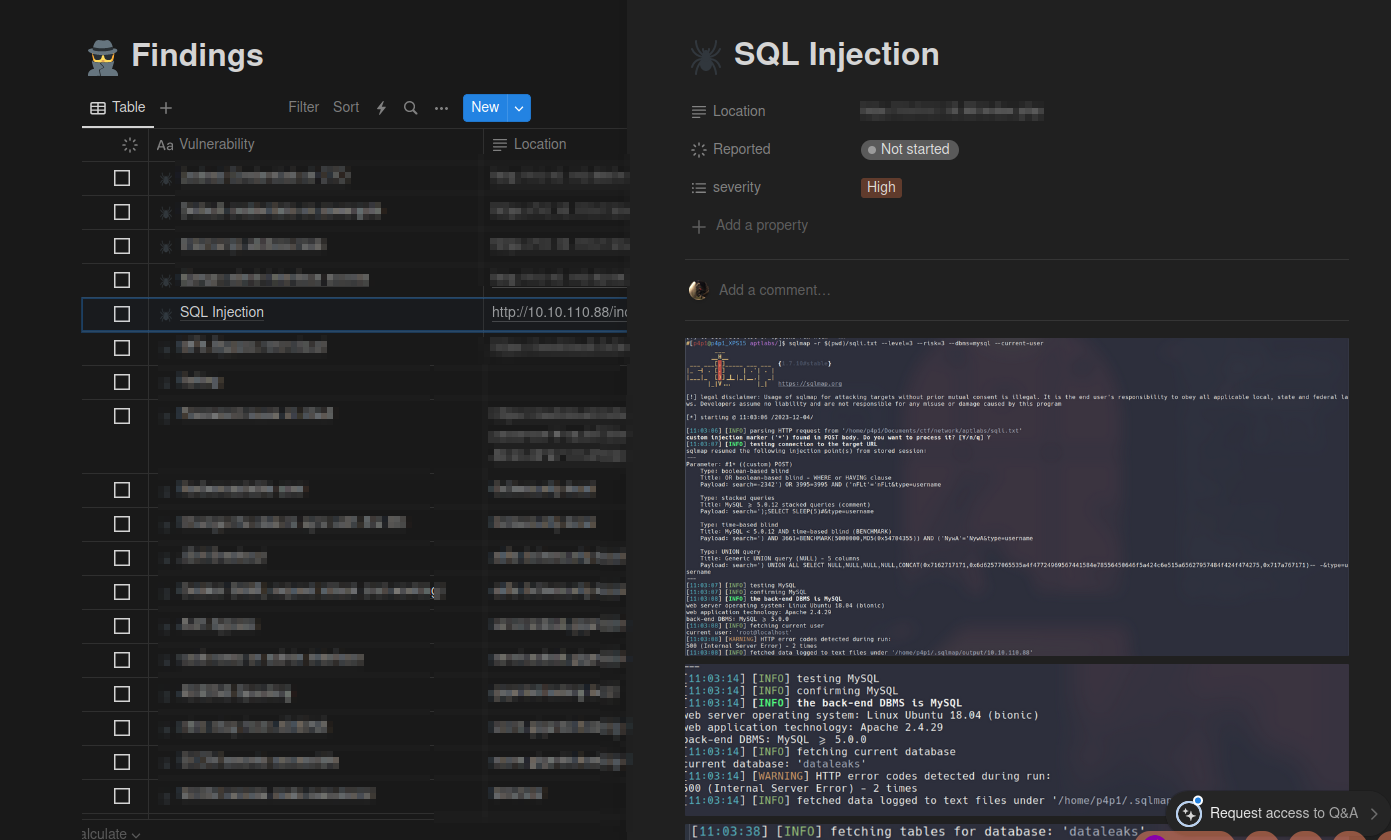
Usually this section starts empty and I slowly add vulnerabilities and how I exploited them great to then copy paste inside of the pentest reports.

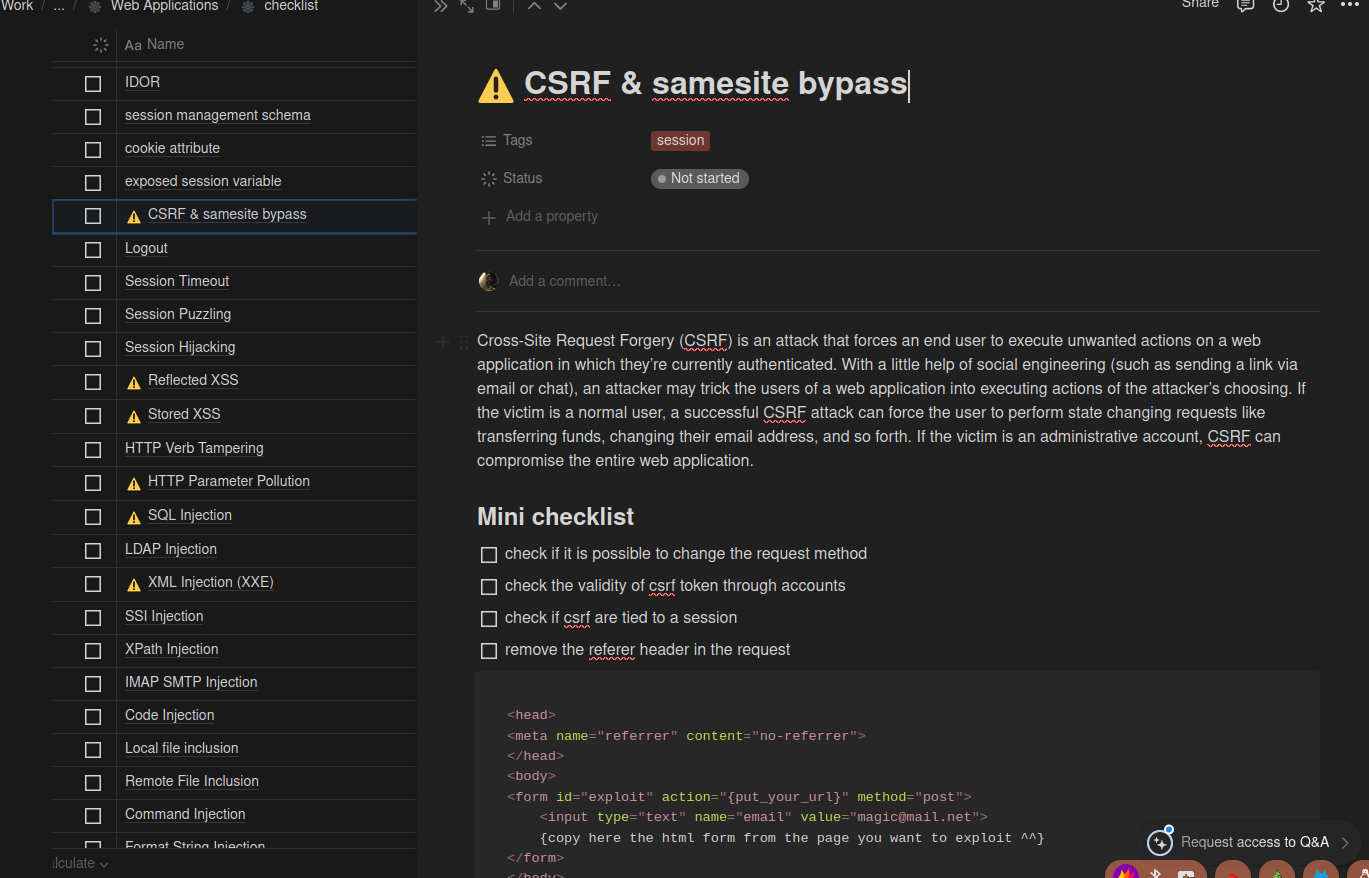
Then it's the actual checklists the meat and potatoes of my organisation where you can find all of the vulnerabilities and how I would detect them and exploit them. This section really just organises my workflow.
Now with this approach there is a bit of an obvious problem let's say one section of this checklist has a advanced tool that would basically need it's own checklists like let's say Wifi Networks?
Specific Tooling lists
In some scenarios I will make checklists for some specific tooling or field without tying it into a full engagement. I inspired this concept from Jakob Friedl who has amazing checklists I am jealous :).

This is less a checklist but more a organised view of vulnerabilities where I can quickly reference things when I forget how to do a certain thing on my wifi-pineapple or flipper zero for example.

A case for AI
Funny that I'm finally talking about ChatGPT inside of a blog post but this is actually a use case of Chatgpt I saw no one talk about and I think it is a great way to start making your own checklists. ChatGPT won't tell you how to hack? But it will give you a step by step checklist if you find out how to ask him 😆
I am a penetration testor on an audit I would need a list of all of the Impacket tools with their names, a description, the kerberos service affected by the tool, the ports they would communicate with and finally a mock command on how to use the tool can you format all of this in a markdown table please?
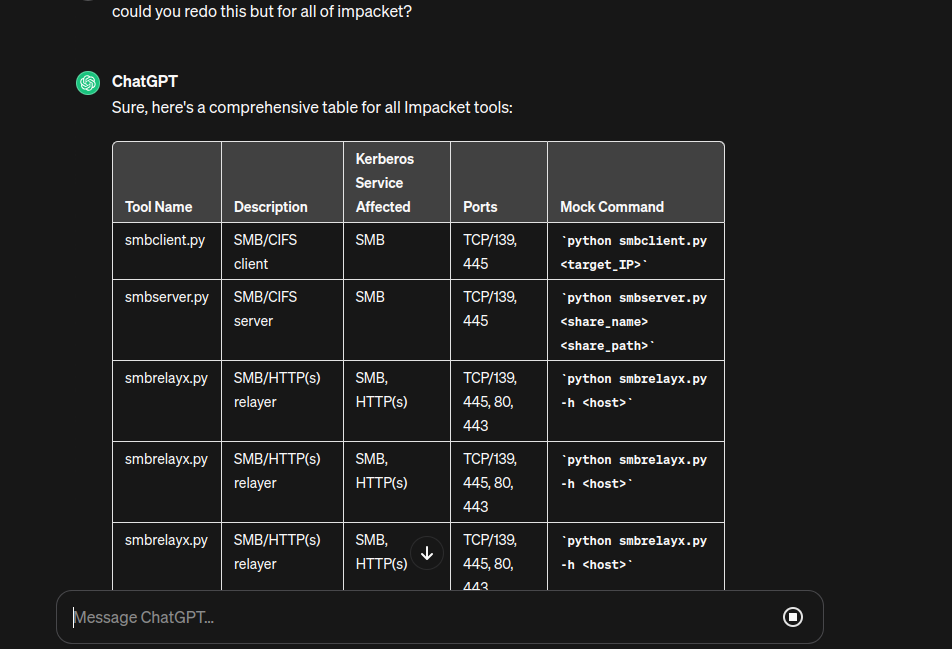
Honestly I couldn't see the use of chat GPT in my work the code sample are quite wrong most of the time and it can't really tell me how to exploit certain things. But for report writing and having starting checklists I think chat GPT is amazing. I use it to quickly explain me certain exploits like CSRF definitions etc.. I actually use the impacket example in my notion:

I hope this post showed you a new project you could work on! Thank you so much for reading you can support me on github sponsor and check out my twitter to get latest news about this blog and follow me on github for new code things :)
p3ng0s
Similar content
Questions / Feedback
Donate

If you like the content of my website you can help me out by donating through my github sponsors page.